Social networking system privacy security runtime verification method based on PPTL3
A social network, privacy security technology, applied in the field of PPTL3-based social network system privacy security runtime verification, can solve problems such as security, WeChat red envelope design flaws, and lack of Omega's full regular expression capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
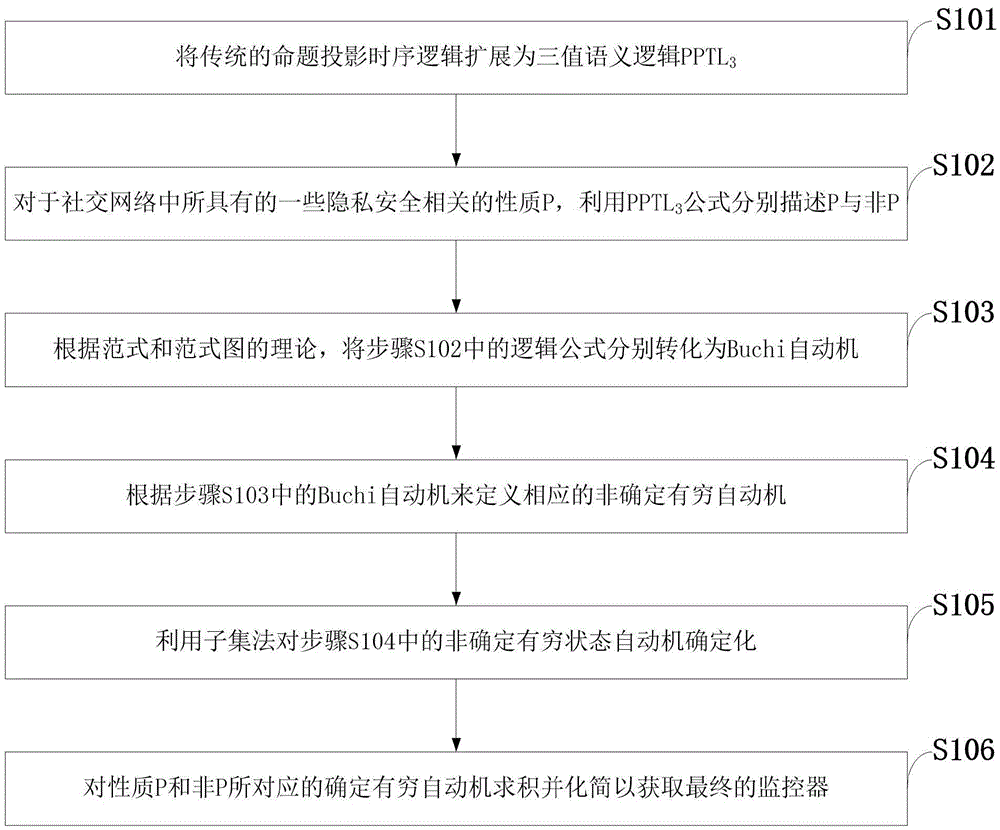
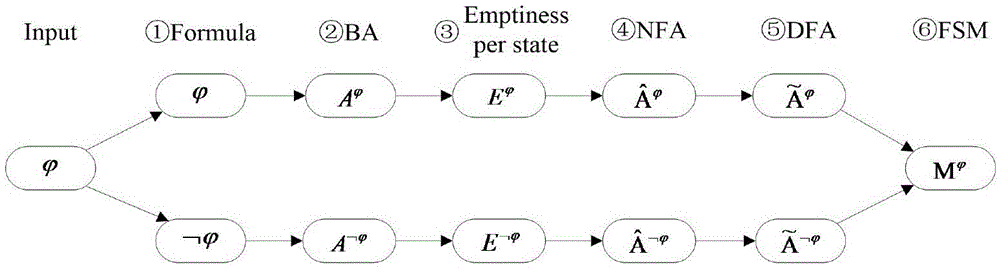
[0088] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0089] The present invention proposes a runtime verification method with projection temporal logic (ProjectionTemporalLogic, PTL) as the underlying logic. First, its propositional subset propositional projection temporal logic (PropositionalPTL, PPTL) has Omega complete regular expression ability, and PPTL can be determined The performance has been proven, and has MSV support platform, applied to task scheduling system, C program verification, composite Web service simulation, description and verification, memory management system verification. PPTL 3 (Propositional Projection Temporal Logic with Three-valued Semantics), N...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com