Wireless access key management method and system
A wireless access and key management technology, which is applied in wireless communication, electrical components, security devices, etc., can solve problems such as poor security, frequent information security accidents, and low key confidentiality, so as to ensure security and modify The effect of heavy workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
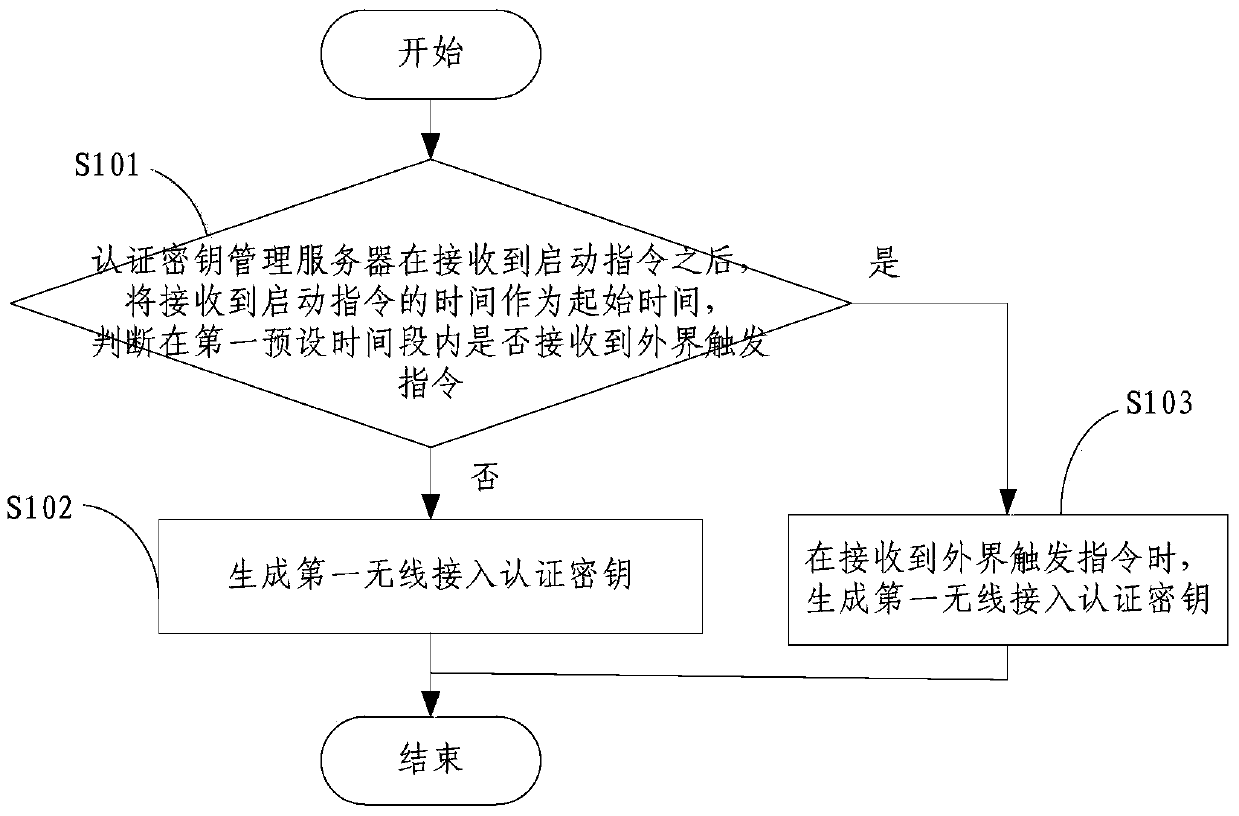
[0051] figure 1 A flow chart of a wireless access key management method provided by an embodiment of the present invention is shown.
[0052] refer to figure 1 A wireless access key management method, comprising the following steps:
[0053] S101. After receiving the activation command, the authentication key management server takes the time of receiving the activation command as the starting time, and judges whether an external trigger command is received within the first preset time period; if not received, execute step S102 , if received, execute step S103;
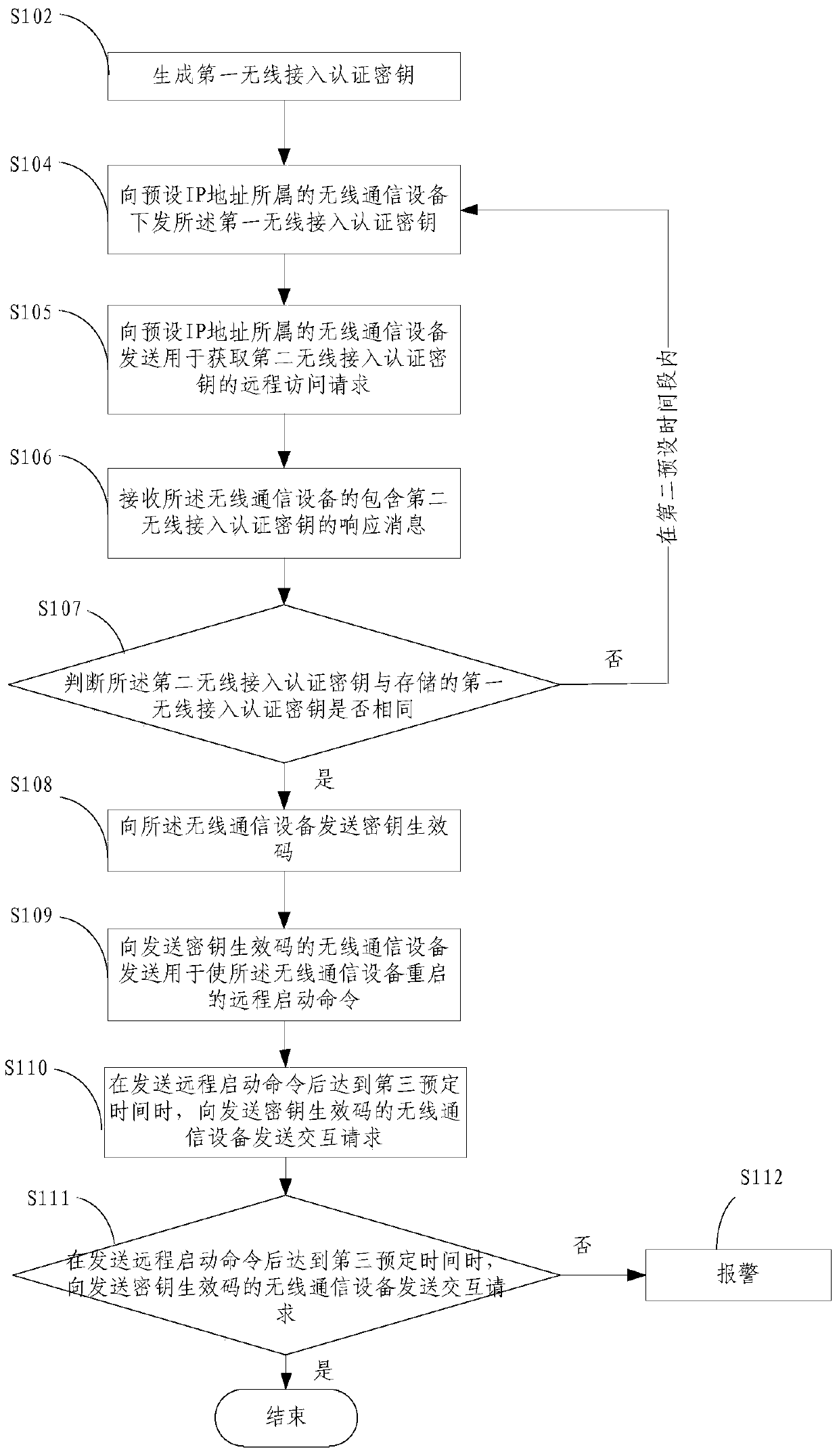
[0054] S102. If not received, generate a first wireless access authentication key, so that the wireless comm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com