Multi-fingerprint cross-unlocking method and system
A multi-fingerprint and unlocking technology, applied in the direction of digital data authentication, to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] In this embodiment, a multi-fingerprint cross unlocking method is provided, and the steps are as follows: figure 1 As shown, including the following steps:
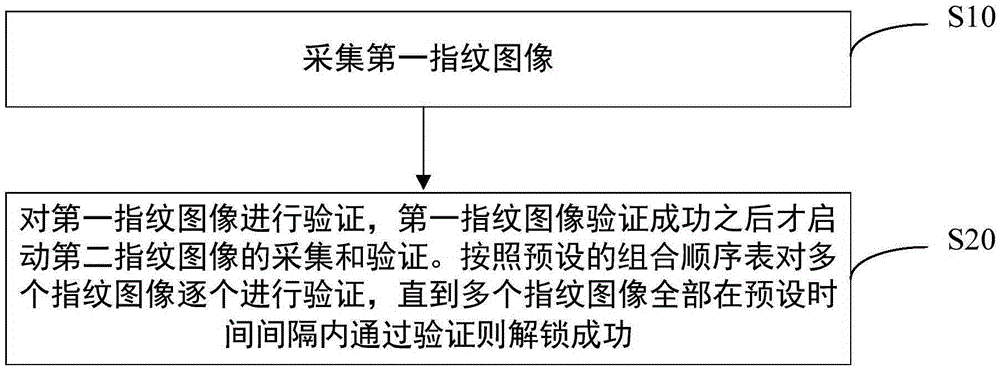
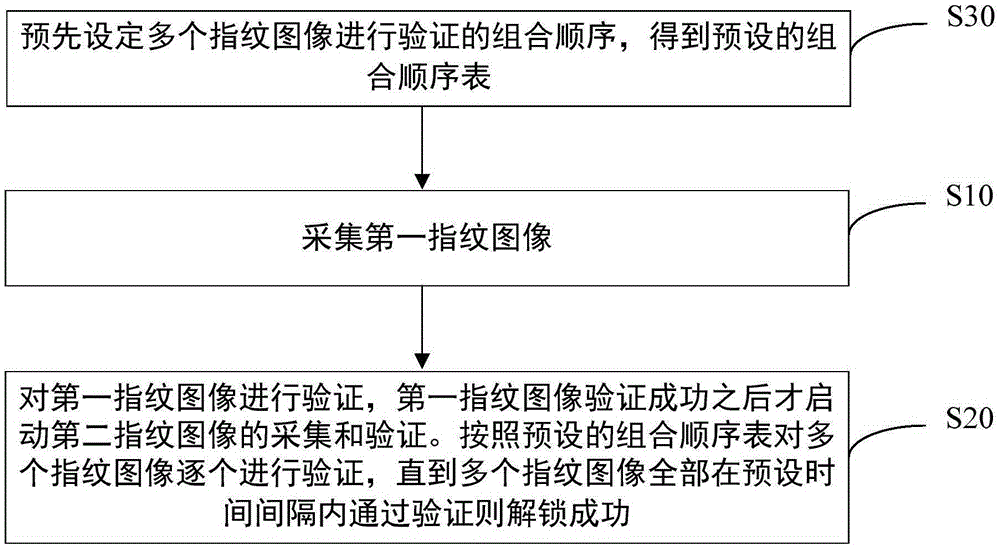
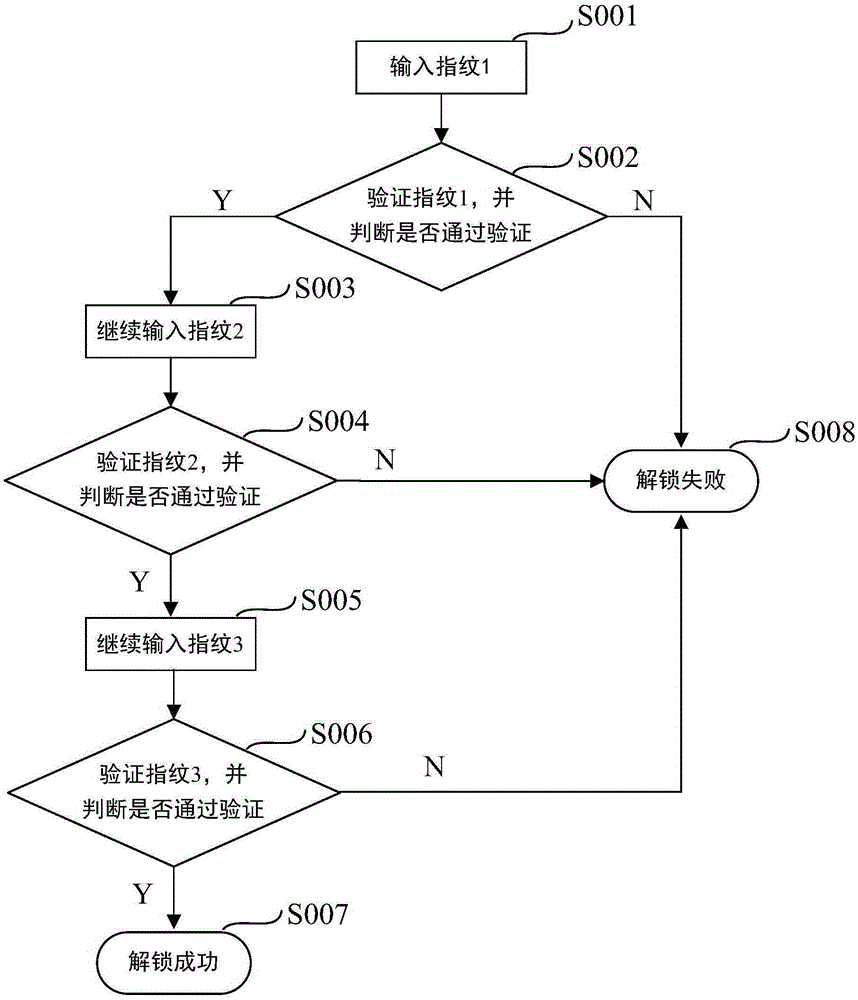
[0047] Step S10: Collect a first fingerprint image.
[0048] Step S20: the first fingerprint image is verified, and the collection and verification of the second fingerprint image is started after the first fingerprint image is successfully verified.
[0049] The multiple fingerprint images are verified one by one according to the preset combination sequence table, until the multiple fingerprint images are all verified within the preset time interval, the unlocking is successful. The preset time interval is a preset time interval that allows two adjacent The maximum time required for fingerprint image verification.
[0050] In this method, collecting multiple fingerprint images is based on one fingerprint collector or multiple fingerprint collectors. The fingerprint collector in this embodiment may use a fingerprint senso...
Embodiment 2
[0077] In the first scenario, the user is one person, that is, multiple captured images come from different fingers of the same person. The device based on the multi-fingerprint cross-adding / unlocking application system is equipped with a fingerprint sensor, and the user performs multiple operations on the fingerprint sensor. (E.g. 10) Finger fingerprint information is registered and saved as template fingerprint information, using cross-type setting to lock and protect. Specifically, taking the registration of three finger fingerprint information as an example for description, the three finger fingerprint information codes registered by the user on the fingerprint sensor are set as a, b, and c. The password is set by cross-type random permutation and combination, namely abc, acb, bac, bca, cab, cba.
[0078] When the device password is set to abc, if you need to access or operate the device, the decryption procedure is as follows: first verify fingerprint information a, verify f...
Embodiment 3
[0080] In the second scenario, the user is multiple people, that is, multiple captured images are from the fingers of the same multiple people, and a device based on the multi-fingerprint cross-adding / unlocking application system is used to configure the fingerprint sensor. People with different identities (such as: A and B) Register the fingerprint information on the fingerprint sensor and save it as template fingerprint information, and use the cross-type setting to lock and protect. Specifically, A and B have the right to access or operate the device. A and B respectively register fingerprint information codes as A and B on the fingerprint sensor of the electronic device. The password of the device can be set to AB or BA. In particular, when there are more than 2 people registering fingerprint information, their registered fingerprint codes are A, B, C..., and the password of the device can be set by cross-random arrangement and combination, namely ABC, ACB, BAC, BCA , CAB, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com