Encryption system and encryption method based on TrustZone
An encryption method and encryption and decryption technology, applied in the field of mobile device encryption, can solve problems such as security risks and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The specific embodiments of the present invention are further explained in conjunction with the drawings.
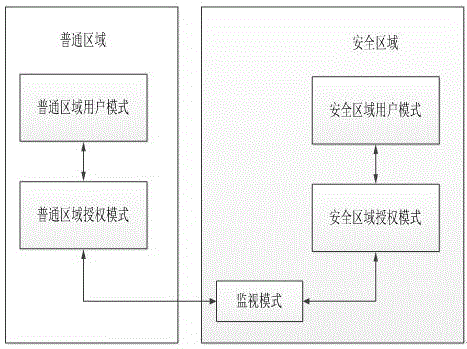
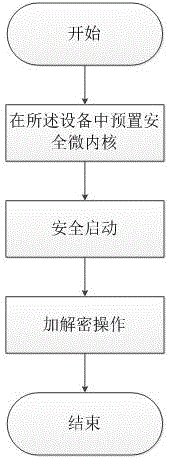
[0026] An encryption method based on TrustZone, which mainly uses an encryption system based on TrustZone, which is used to establish normal mode and safe mode. The safe microkernel is preset in the safe mode. The safe microkernel divides the safe zone memory into multiple task memories Space, mobile devices that support independent security applications running at the same time, including the driver layer calling submodule, API calling submodule, key return submodule, and key verification submodule;
[0027] The driver layer calling sub-module is used to call the mobile device driver layer interface through shared memory when the upper application needs to encrypt and decrypt;
[0028] The API call sub-module is used for the driver layer to call the security microkernel through TrustZoneAPI after receiving the call command from the upper layer, so that the mobile device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com