A bluetooth earphone with voice encryption function and voice encryption method thereof
A voice encryption, Bluetooth headset technology, applied in transducer circuits, near-field transmission systems using transceivers, sensors, etc., can solve the problems of lossy encoding and decoding algorithms, leakage of calls, and difficulties, and simplify operations. The use process, high time synchronization, good use convenience effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030]In order to enable those skilled in the art to better understand the technical solution of the present invention, and to make the above-mentioned purpose, features and advantages of the present invention more obvious and understandable, the product of the present invention will be further described in detail below in conjunction with the embodiments and accompanying drawings illustrate.
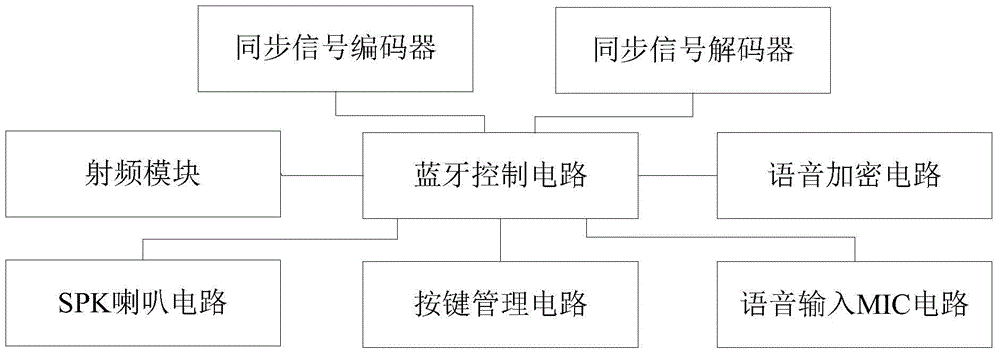
[0031] Such as figure 1 Shown, a kind of bluetooth earphone with voice encryption function, comprises bluetooth control circuit, synchronous signal encoder, synchronous signal decoder, voice encryption circuit and key management circuit, described synchronous signal encoder, synchronous signal decoder, voice encryption The circuit and the button management circuit are all connected with the bluetooth control circuit.
[0032] The Bluetooth earphone also includes a SPK speaker circuit and a voice input MIC circuit, and the SPK speaker circuit and the voice input MIC circuit are connecte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com