Method and device for carrying out safety analysis on network behaviors
A security analysis and network technology, applied in the field of network security, can solve the problems of high false alarm rate, inability to fully detect abnormal traffic attacks, low performance of feature detection, etc., and achieve the effect of ensuring security and reliability, and a reliable network application environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] In the embodiment of the present invention, the network order construction technology based on the clustering algorithm, the network order chain construction technology based on the association analysis algorithm, and the black, white and gray list technology perform security analysis on network behavior, which overcomes the shortcomings of the methods in the above three directions, and can Defense against various network attacks.
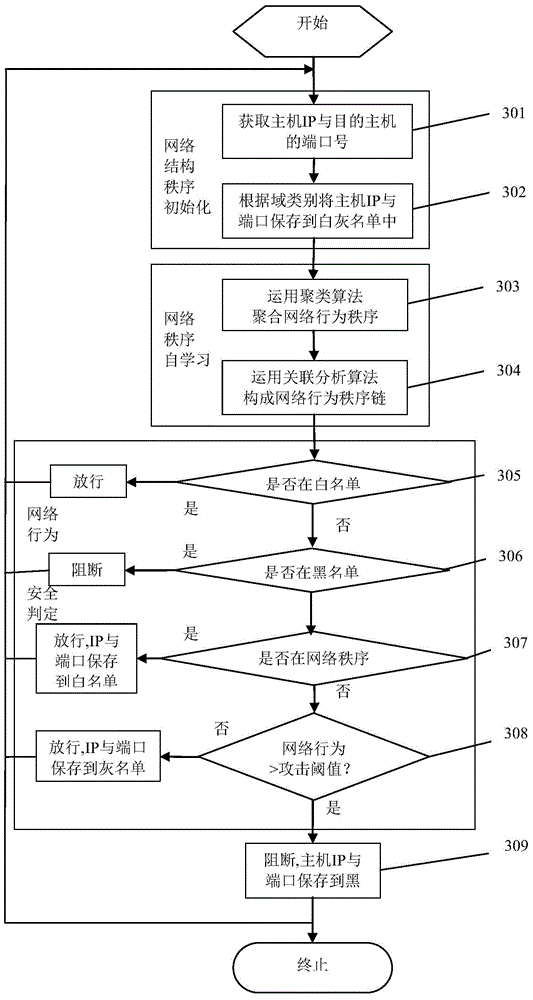
[0046] A schematic diagram of the implementation principle of a method for security analysis of network behavior provided by an embodiment of the present invention is as follows figure 1 As shown, the specific processing flow is as follows figure 2 As shown, the following processing steps are included:
[0047] Step S210: Setting initial whitelist, graylist and blacklist of network hosts.
[0048] In the initial stage of network structure order, the IP address and port number of each host in the secure trusted domain and the IP address an...
Embodiment 2
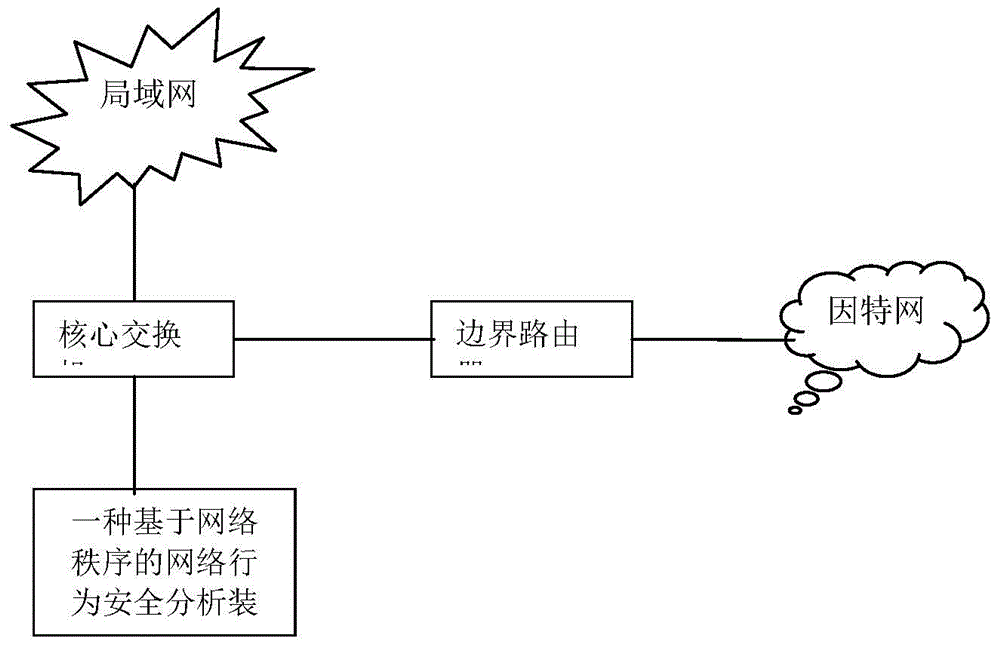
[0070] This embodiment provides a schematic diagram of an application scenario of a device for security analysis of network behavior, as shown in image 3 As shown, the Internet includes routers and core switches. Routers can transmit and route network traffic. LANs are connected to the Internet through core switches. LANs include aggregation layer and access layer switches, PCs, and mobile terminals. Terminals can be connected to Network, communicate and share information. The network behavior security analysis device based on the network order in the embodiment of the present invention is connected to the mirror port of the core switch, and is used to obtain network data packets, analyze network traffic behavior, and detect network attacks.
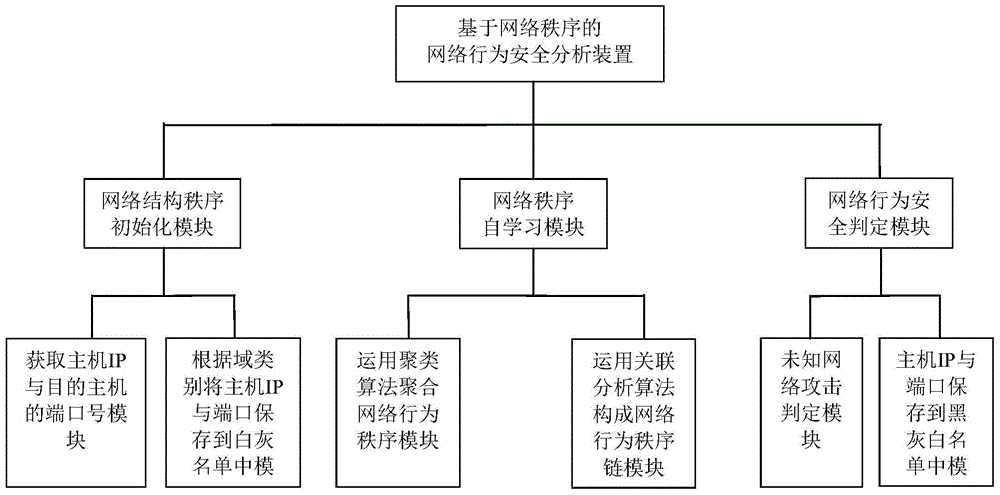
[0071] The specific implementation structure of the above-mentioned device for security analysis of network behavior is as follows: Figure 4 As shown, it can specifically include the following modules:
[0072] The network behavior o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com