Method for detecting DNS (Domain Name-implementation and Specification) tunnel data based on DNS protocol standard
A technology of DNS tunneling and protocol data, which is applied in the field of computer networks and can solve the problems of being unable to cope with DNS tunnel penetration, users being unable to resolve domain names, and threatening internal network security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be further described in detail below in conjunction with the accompanying drawings.
[0017] System network deployment method:
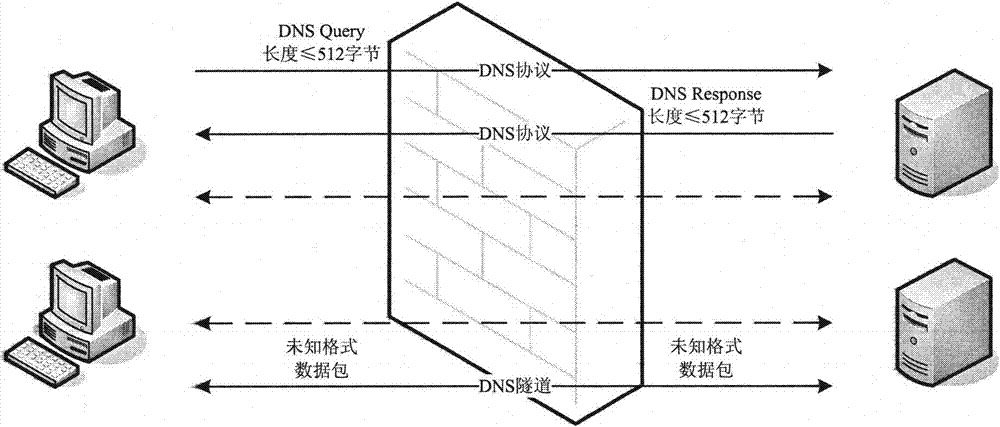
[0018] see figure 1 , the system of the present invention is usually deployed at the egress gateway where the local area network is connected to the Internet, and captures the data packets of the specified port from the network. The port is generally UDP53, and other ports can be specified or added if necessary.
[0019] Packet detection method:
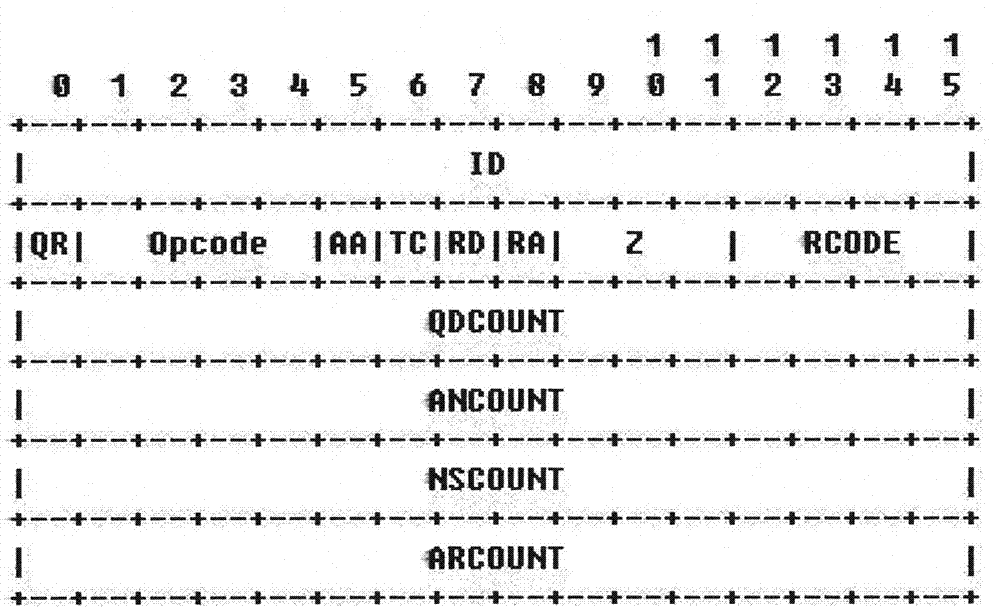
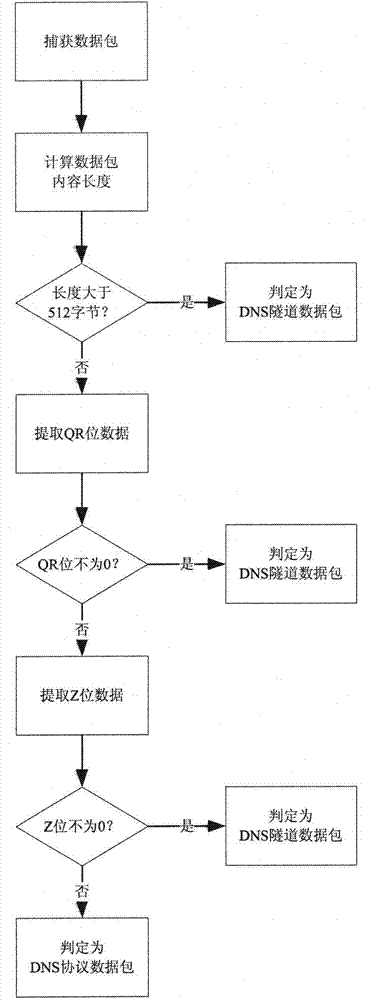
[0020] The detection standard is to determine whether the data packets passing through the port conform to the DNS protocol. As long as the data packets do not conform to the RFC1035 document description, they can be judged as DNS tunnel data packets, otherwise they are DNS protocol data packets.
[0021] RFC1035 stipulates that the content length of DNS data packets shall not exceed 512 bytes. If the content length of the data packet is greater than 512 bytes, the data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com