Mobile terminal data safety protection method and device
A mobile terminal and data security technology, applied in digital data protection, security devices, electrical digital data processing, etc., can solve the problems of high energy consumption, unreliable security, and single function, so as to save electric energy, prolong protection time, The effect of increasing safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
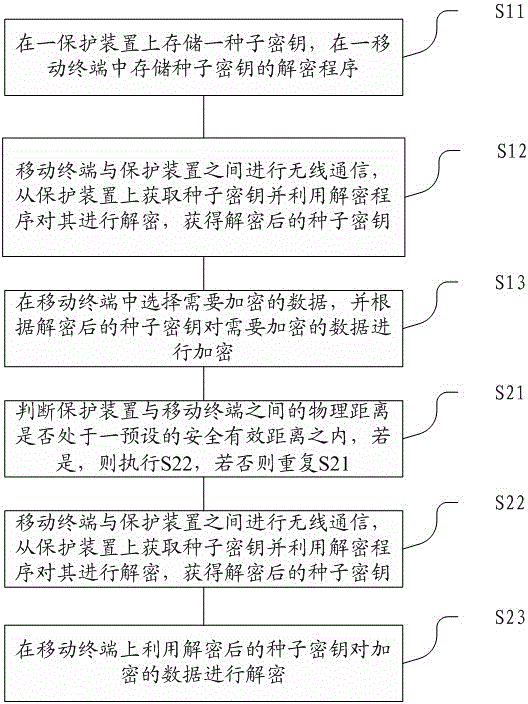
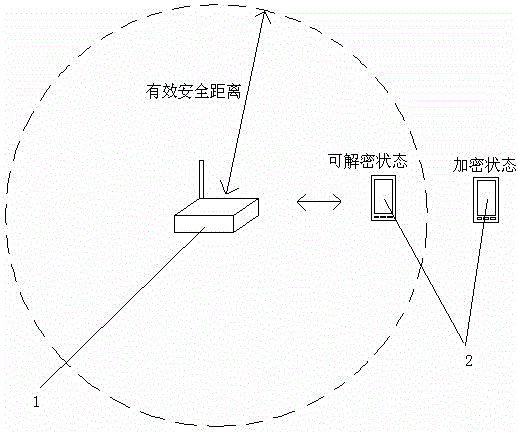
[0126] Considering that the user is often outdoors, the protection device should be easy to carry and not easy to lose, and at the same time, taking into account the outdoor communication problem between the two, in this embodiment, the protection device 1 can be a device with Bluetooth function; the mobile terminal 2 and the protection device 1 use Bluetooth 4.0 BAS, IAS Profile protocol for intermittent communication of data information. The reason for adopting intermittent communication is that a large amount of electric energy can be saved, so as to increase the protection time of the protection device for the mobile terminal.
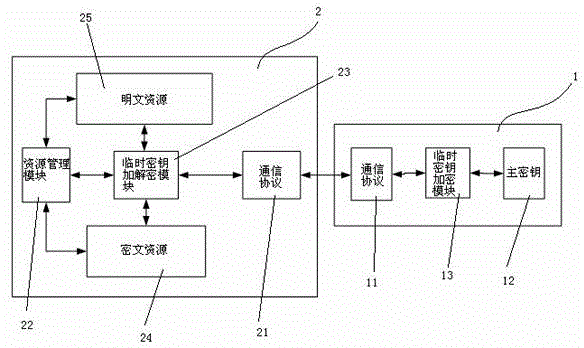
[0127] The mobile terminal 2 first opens the Bluetooth connection to search, and selects the corresponding protection device 2 to establish the Bluetooth connection. The mobile terminal 2 sets a master key of a specified length, and transmits the original output of the master key to the protection device 2 in the form of a data packet, ordering it ...
Embodiment 2
[0142] Considering that when working indoors, the protection device 1 can use a wireless router that supplies power indoors for a long time. The advantage of this protection device is that the wireless network covers a large area and can protect multiple mobile terminals connected to the network at the same time. Since there must be a power supply in the room, the protection device 1 and the mobile terminal 2 can avoid the consideration of power saving, so the mobile terminal can maintain a continuous connection state with the protection device. Of course, an intermittent connection may still be used here, which is not limited in this embodiment.
[0143] The mobile terminal 2 first opens the wifi connection to search, and selects the corresponding protection device 2 to establish the wifi connection. The mobile terminal 2 sets a master key of a specified length, and transmits the original output of the master key to the protection device 2 in the form of a data packet, orderi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com