Service authorization method, equipment and system
A technology for authorizing equipment and services, applied in transmission systems, user identity/authority verification, electrical components, etc., to achieve flexible and changeable communication methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0046] (The process of applying for offline authorization business)
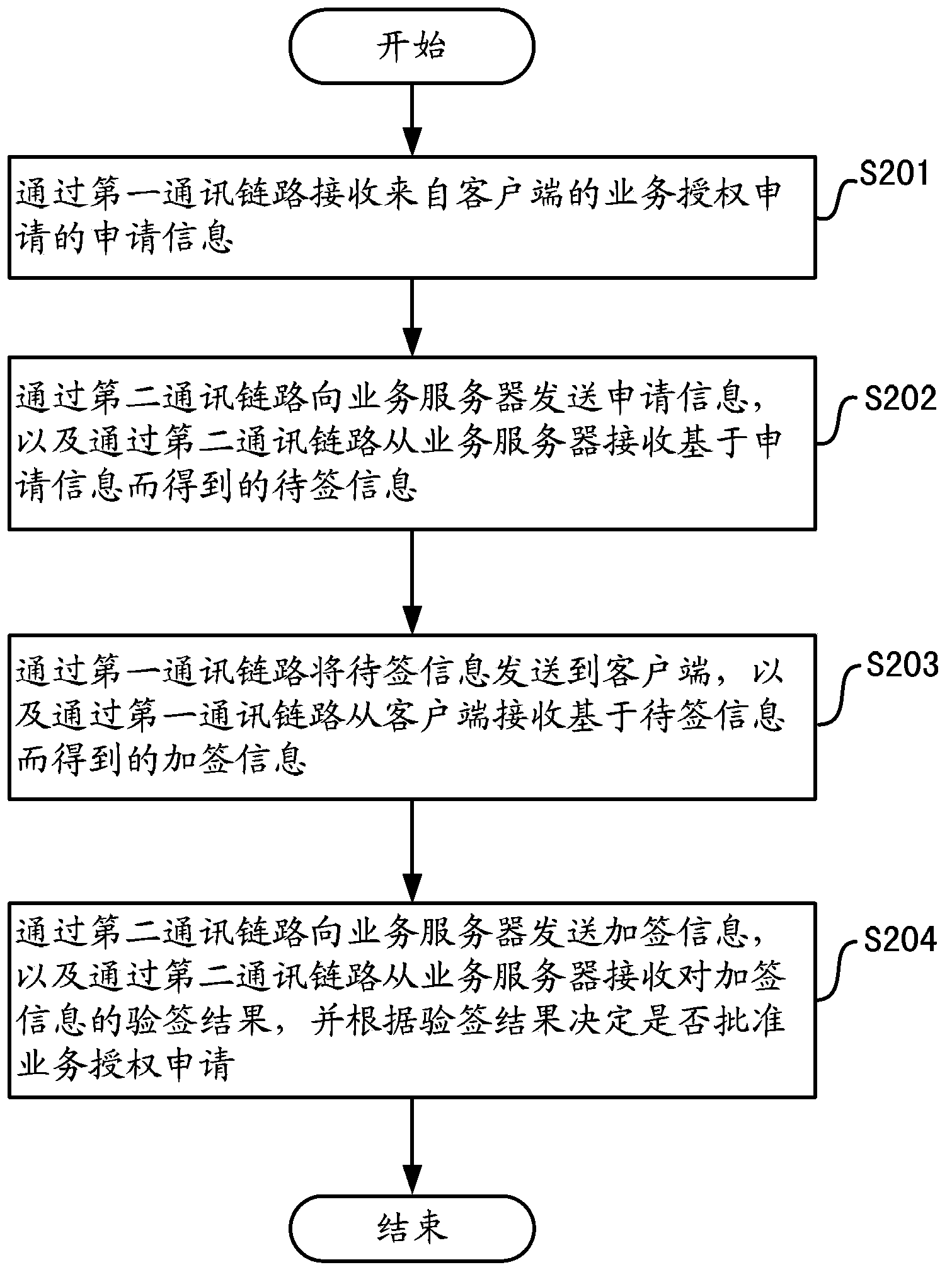
[0047] Such as Figure 2A As shown, in step S201, the application information of the service authorization application from the client is received through the first communication link. In other words, an application for an offline authorization service is issued from the client, and application information related to the application is sent to the authorization core device through a near-field communication link such as a sound wave.
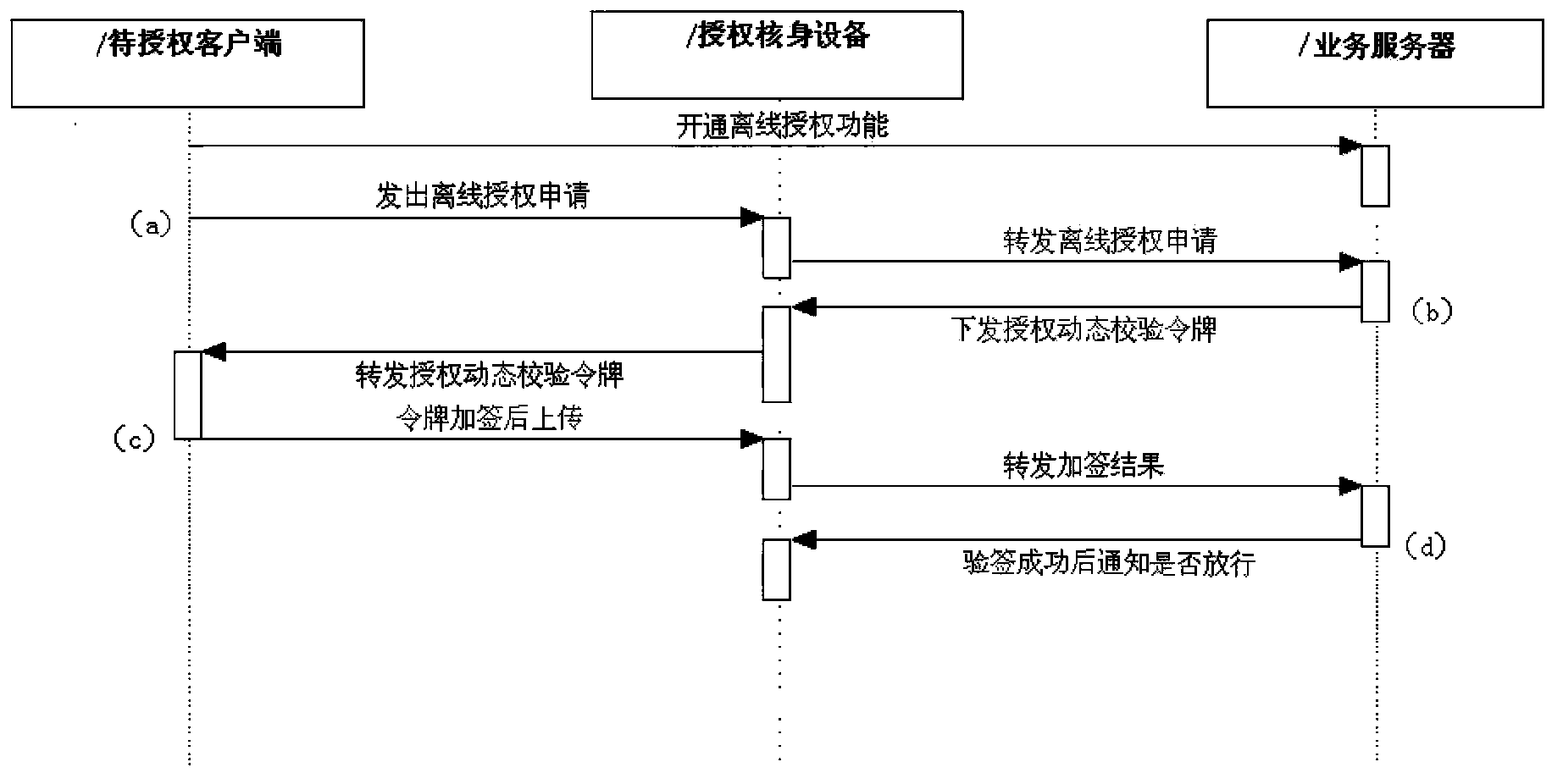
[0048] Specifically, step S201 includes such as figure 1 Issuing Offline Authorization Requests is shown in this section.
[0049] [Issue Offline Authorization Request]
[0050] In security scenarios such as identity confirmation and authorization, whenever the client generates an offline authorization application, it will generate a unique business serial number to be authorized, and send the waiting list to the real-time online authorized verification device through a nea...
Embodiment approach 2
[0070] In Embodiment 1, the procedure of service authorization of a common authorization level that does not require high security is described. When high security requirements are required, offline service authorization with a higher authorization level can be realized by setting an offline authorization password.
[0071] Below, refer to figure 1 , Figure 2A and Figure 2B To illustrate the use of offline authorization passwords. In this embodiment, differences from Embodiment 1 will be described in detail, and the same points as Embodiment 1 will be omitted. For the points in the second embodiment that are the same as those in the first embodiment, the same reference numerals as those in the first embodiment are used.
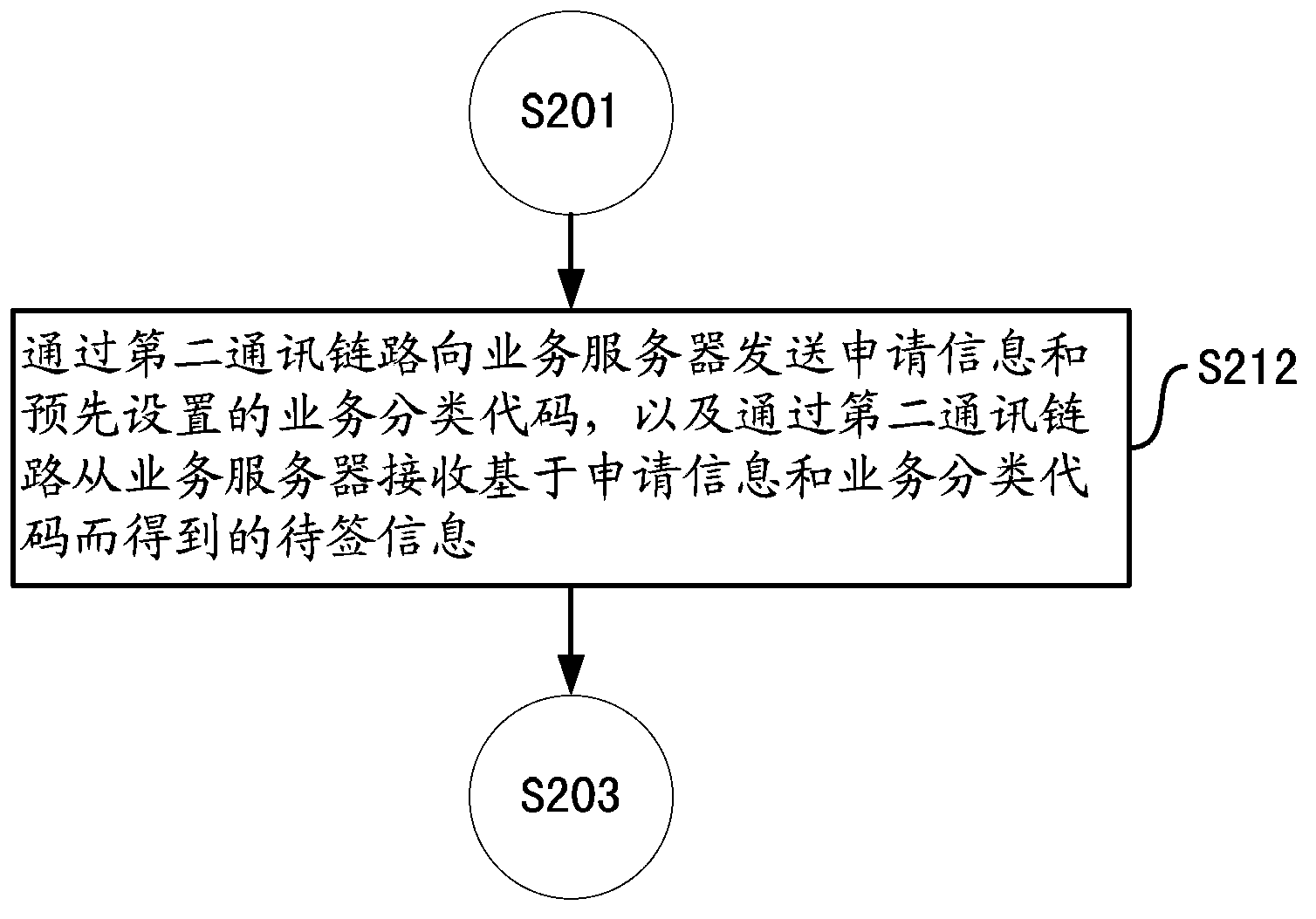
[0072] Figure 2B It is a schematic flow chart of a high authorization level service authorization method according to an embodiment of the present application. Specifically, in Embodiment 2, using Figure 2B In step S212 to replace Figure 2A Step ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com