Anti-phishing method based on multi-factor comprehensive assessment method
A comprehensive evaluation, multi-factor technology, applied in special data processing applications, instruments, electrical and digital data processing, etc., can solve problems such as high false alarm rate, single method, insufficient power, etc., to achieve high accuracy and comprehensive effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The above and other technical features and advantages of the present invention will be described in more detail below in conjunction with the accompanying drawings.
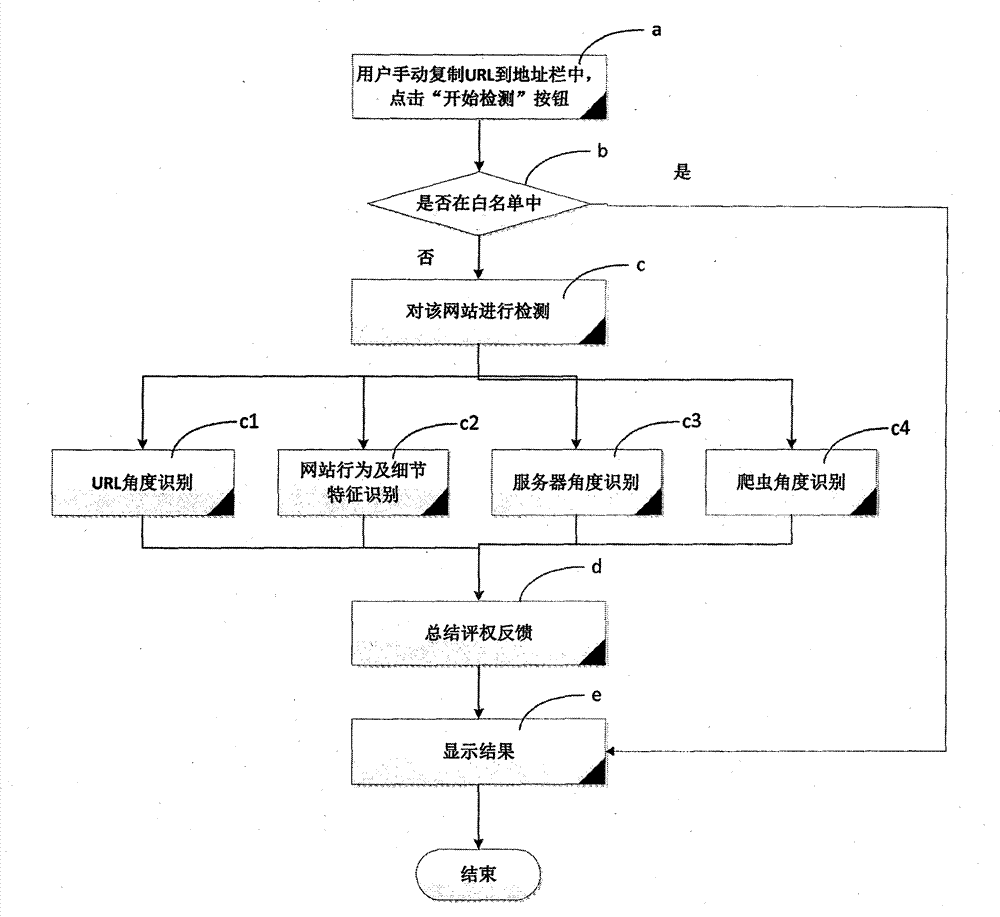
[0050] see figure 1 As shown, it is a flowchart of the anti-phishing method based on the multi-factor comprehensive evaluation method of the present invention, wherein:
[0051] Step a, establish a black and white list library of URLs, and process the target URL to determine whether the processed URL is in the black / white list, if it is in the list library, execute step d, and directly feed back the result to the user; if not list library, then execute step b to perform subsequent detection of the website.
[0052] In step b, during the detection process, the URL angle recognition is performed first, because the execution speed of this part is relatively fast, and there is no need to set up a special thread for wasting overhead; after that, three threads are used to detect the remaining three asp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com