Network intrusion detection method
A network intrusion detection and network technology, applied in the field of network security, can solve the problem that the matching mode of the signature database can no longer fully achieve the purpose of interception, and achieve the effect of improving the speed, reducing the false alarm rate and ensuring fast response.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The method of the present invention will be described in further detail below in conjunction with the accompanying drawings.
[0039] The method for network intrusion detection of the present invention comprises the following specific steps:
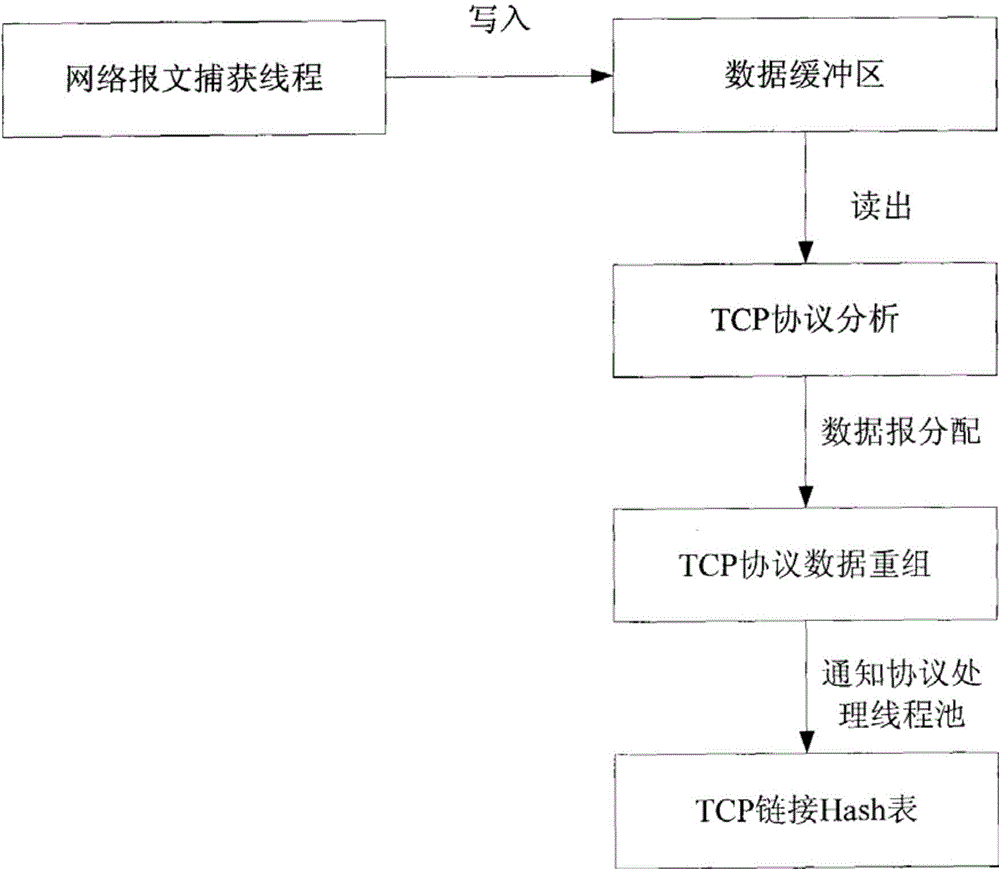
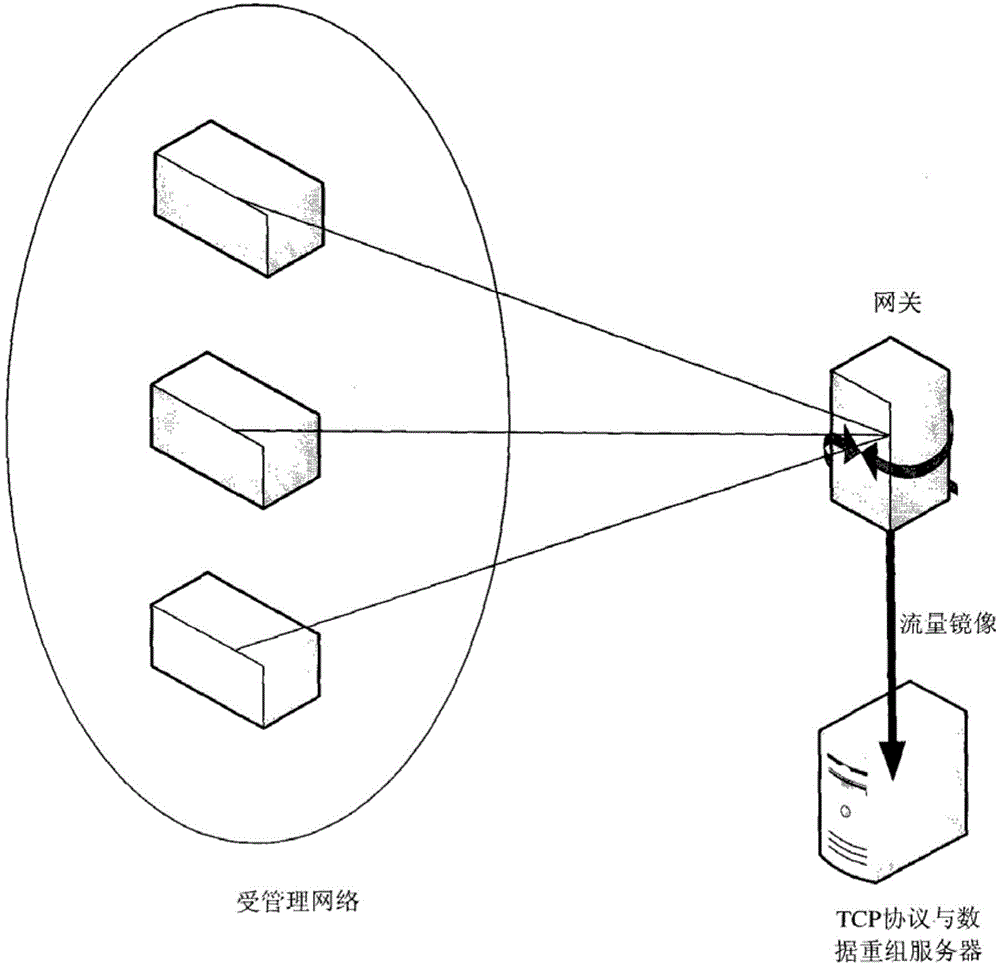
[0040] The first step is to capture the data packets in the network;
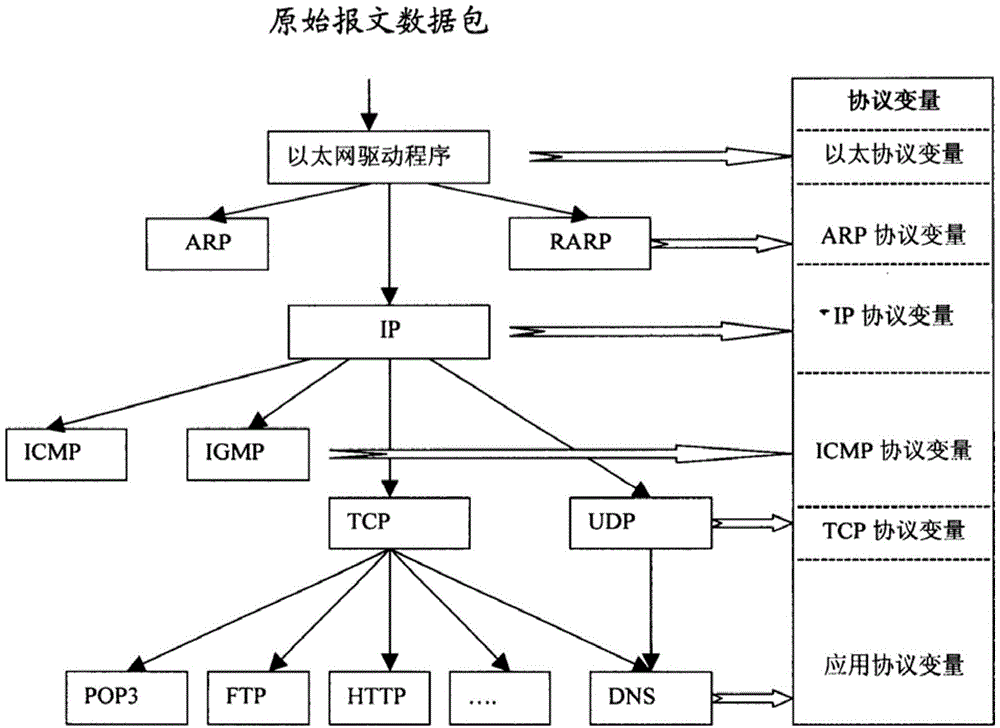
[0041] In the second step, the captured data packets are analyzed by the whole protocol stack to obtain the protocol variables, that is, the data of each protocol layer of the original message data packets;
[0042] In the third step, the regular expression rule set is compiled into a DFA state transition table through a deterministic finite state machine, and the DFA state transition table is compressed;
[0043] The fourth step is to write the data analyzed in the second step into the compressed DFA state transition table for matching;
[0044] The fifth step is to output the matching result.
[0045] The specific implementation process of the second step ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com