A Deep Packet Inspection Method Based on Finite Automata
A technology of in-depth message detection and finite automata, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of large and long detection circuits and difficulty in making logic circuits, so as to improve the working speed and data Throughput rate, optimized logic structure, and area-saving effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
[0024] The present invention is based on the depth message detection method of FA, comprises the following steps:
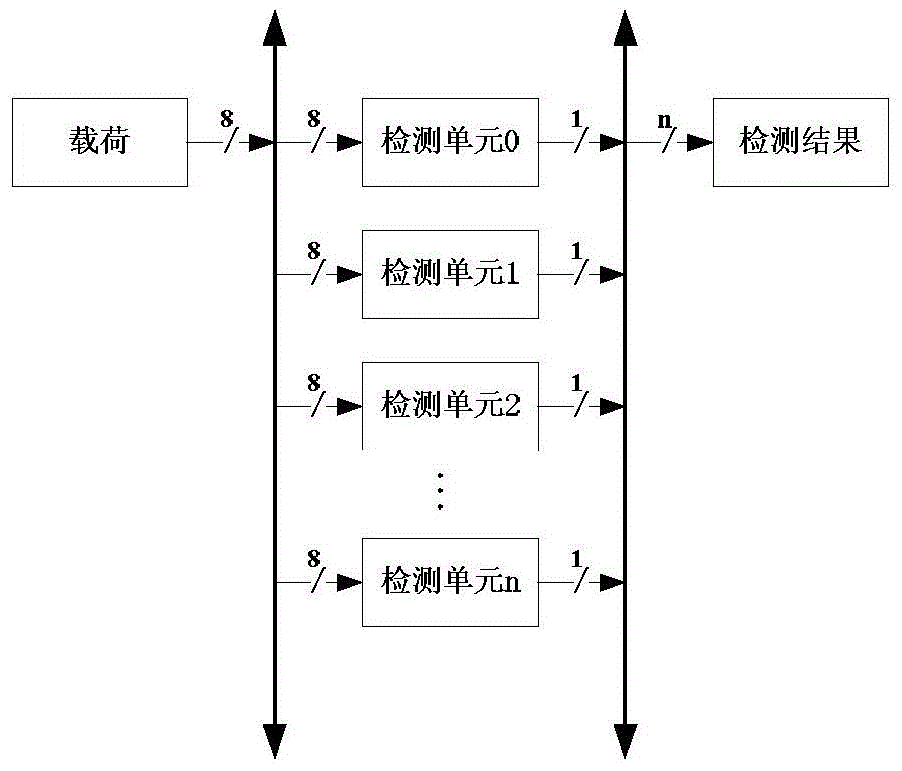
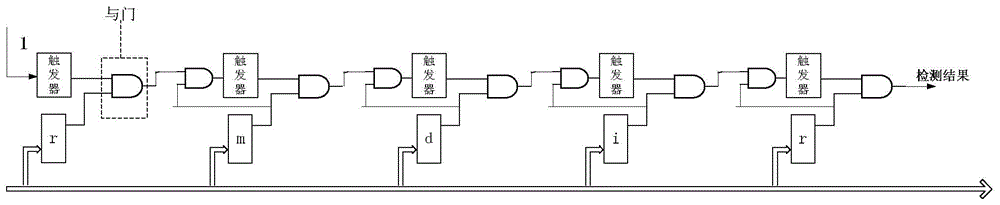
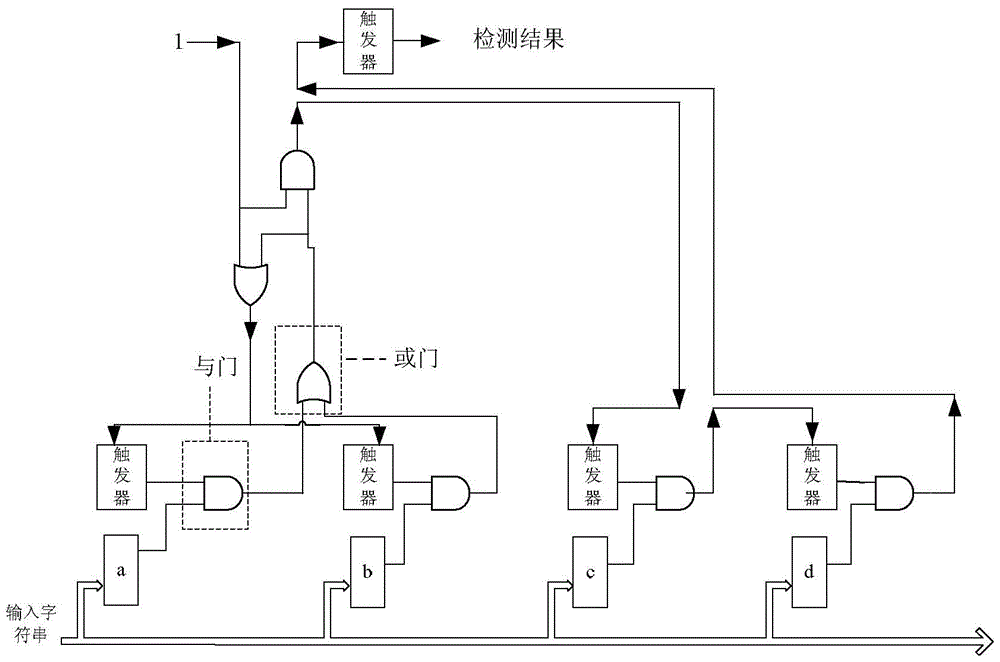
[0025] S1. In the initialization phase of system power-on, the CPU writes all default configurations into the third-level memory by issuing instructions, and each level can have multiple memories. Among them, the first-level memory stores the first two characters of all violating character strings, the second-level memory stores the characters included in all violating character strings, and the third-level memory stores the corresponding value and the corresponding value of the violating string after hash calculation. Offending collection number.
[0026] In this example, if Figure 4 As shown, the first-level memory uses 26 letter cross indexes as address items, so there are currently 676 addresses. In subsequent versions, ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com