Security and protection monitoring system and corresponding warning triggering method
A technology of security monitoring and alarm triggering, which is applied to anti-theft alarms, alarms, alarms that rely on interference with short-wavelength radiation, etc., can solve the problems of high probability of false alarms and false alarms, and achieve the goal of reducing the probability of false alarms Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
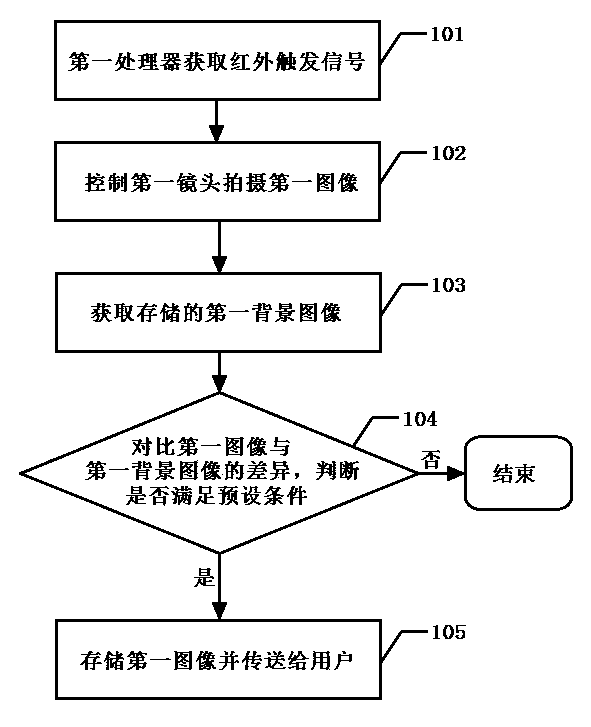
[0016] An implementation of the alarm trigger method of the security monitoring system of the present invention can be referred to figure 1 , including the steps:
[0017] 101. The first processor obtains an infrared trigger signal generated when the infrared sensor connected to the signal is triggered.
[0018] The so-called infrared sensor refers to a device capable of detecting infrared radiation in a monitoring area, such as a PIR, which can generate an infrared trigger signal when it is triggered by infrared radiation.
[0019] It is easy to understand that, based on different sensor configurations, the generated infrared trigger signal can be a digital signal or an analog signal, which can be directly transmitted to the appropriate interface of the first processor, or can be processed by conventional software / hardware Appropriate interface to the first processor, such as analog / digital conversion, amplification, shaping, filtering, etc.
[0020] 102. The first proces...
Embodiment 2
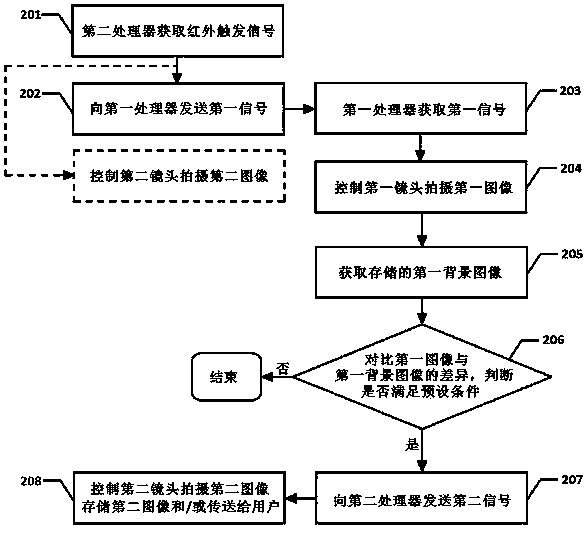
[0043] Another embodiment of the alarm triggering method of the security monitoring system of the present invention can be referred to figure 2 Compared with Embodiment 1, the main difference of this embodiment is that the first processor mainly performs image difference comparison operations, and the second processor is responsible for processing the trigger signal of the infrared sensor and performing specific alarm operations. The method includes the steps of:
[0044] 201. The second processor acquires an infrared trigger signal generated when the infrared sensor connected to the signal is triggered. For the specific content of this step, refer to the description related to step 101 in Embodiment 1.
[0045] 202. The second processor sends a first signal indicating that the infrared sensor is triggered to the first processor according to the acquired infrared trigger signal. Specifically, the first signal may be in any form that the first processor can understand, suc...
Embodiment 3
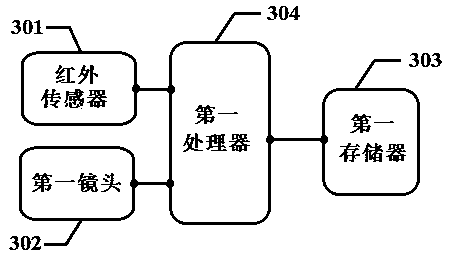
[0057] An implementation of the security monitoring system of the present invention can refer to image 3 , the security monitoring system of this embodiment can be used to implement the alarm triggering method involved in Embodiment 1. Structures include:
[0058] Infrared sensor 301, used to detect infrared radiation in the monitoring area, and generate an infrared trigger signal when triggered by infrared radiation;
[0059] The first lens 302 is used to capture images in the monitoring area;
[0060] The first memory 303 is used to store the first background image;
[0061] The first processor 304 is signal-connected with the infrared sensor 301, the first lens 302 and the first memory 303, and is used to run the program to perform the method comprising the following steps: acquiring the infrared trigger signal generated by the infrared sensor 301, and according to the acquired infrared The trigger signal controls the first lens 302 to take the first image, acquires the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com