Method for protecting account security based on asynchronous dynamic password technology
A dynamic password and technology technology, applied in platform integrity maintenance, user identity/authority verification, electrical components, etc., can solve problems such as lack of confidentiality, inability to prevent, and inability to prevent fraudulent attacks by criminals, to reduce computing pressure , the calculation formula is simple, and the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
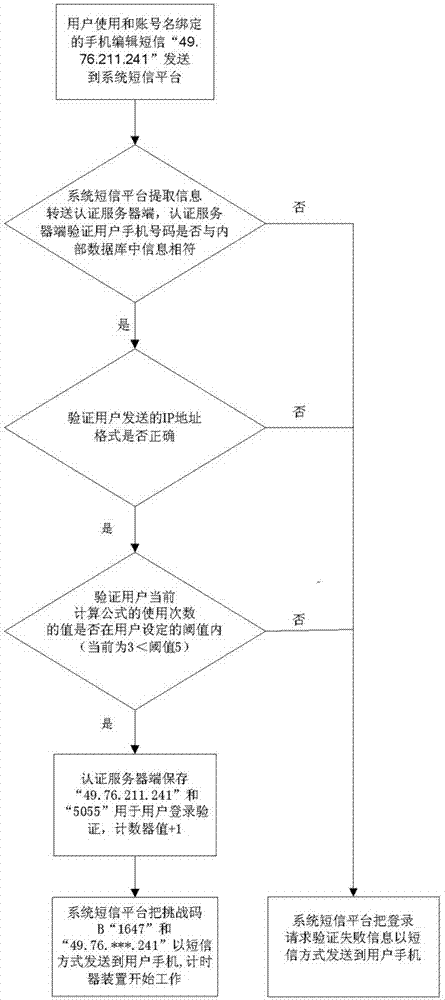
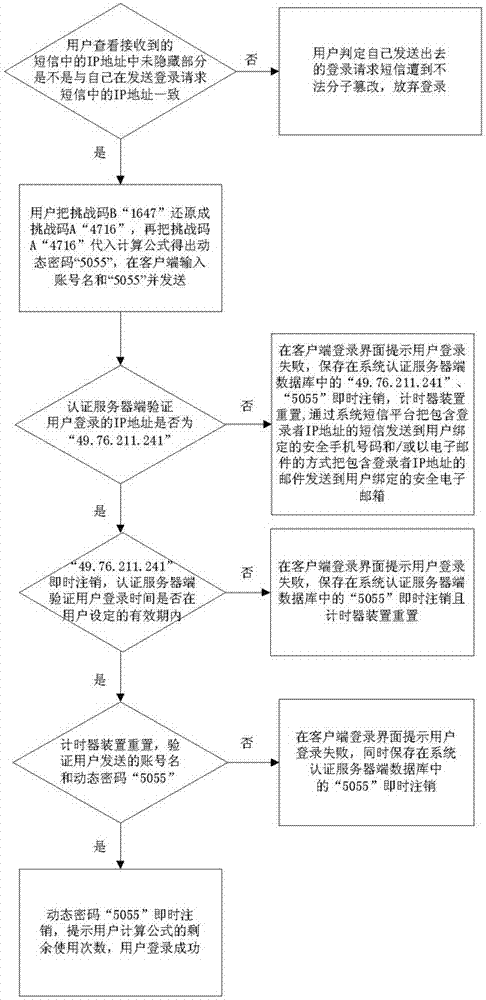
[0046] (1) Registration: The user submits binding information to the service provider. The binding information includes the user's account name, a mobile phone number, the encryption method of the challenge code, the validity period of the dynamic password, the calculation formula of the dynamic password and the use of the calculation formula The threshold of the number of times, a secure email address and / or another secure mobile phone number, the encryption method of the challenge code, the validity period of the dynamic password, the calculation formula of the dynamic password and the threshold of the use times of the calculation formula are jointly agreed by the user and the service provider. And it can be retrieved or modified through the secure email address and / or another secure mobile phone number, the management workstation verifies the account name, mobile phone number, secure email address and / or another secure mobile phone number submitted by the user, and calculates...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com