Active trapping method based on behavior capturing
A behavioral and trapping technology, applied in electrical components, transmission systems, platform integrity maintenance, etc., can solve problems such as lack of pertinence, incomplete data, and unknown attacks cannot provide effective protection, so as to improve the level of network security, The effect of preventing malicious code intrusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
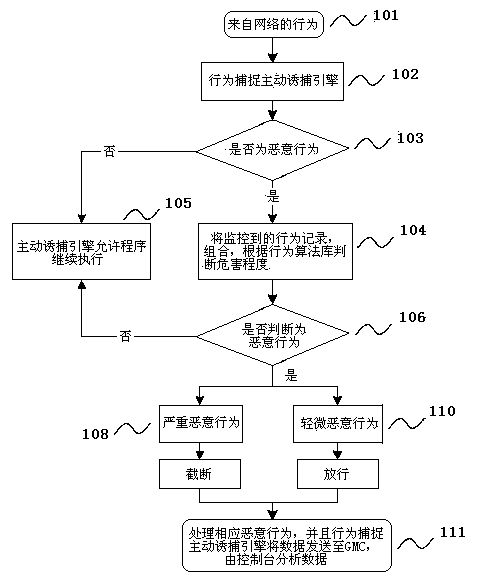
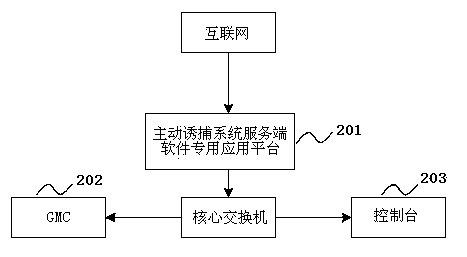
[0023] The embodiment of the present invention provides a method and system for active trapping based on behavior capture to solve the defects of the data capture technology adopted by the existing honeypot system, and is mainly used for PC terminals, servers, and workstations on the network to actively, efficiently, System-level security defense.
[0024] In order to make the object, technical solution, and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
[0025] Some malicious behaviors defended by the present invention include: process creation, thread creation, file operation, network operation, registry operation, stack operation, thread injection, advanced persistent threat attack (APT attack), and user account operation, etc. There are three main ways to obtain program behavior through hook technology, intercepting the system service distribution table ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com