Circuit, chip and method for defending against energy attack on grouping algorithm
A technology of energy and circuits, applied in the field of information security, can solve the problem of high hardware cost of MASK technology, and achieve good defense effect and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
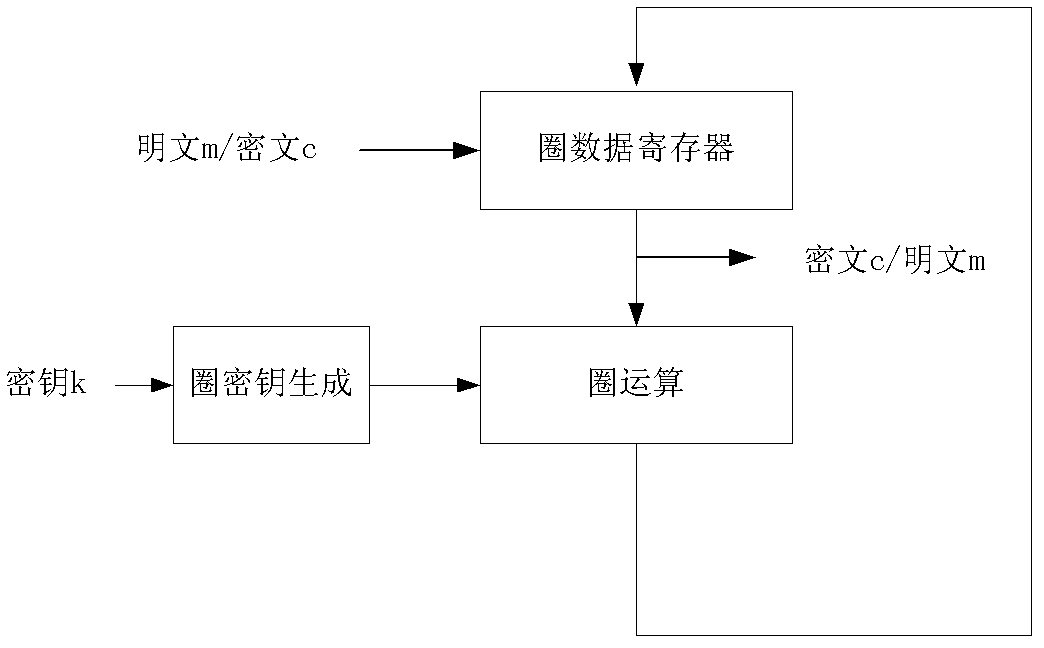
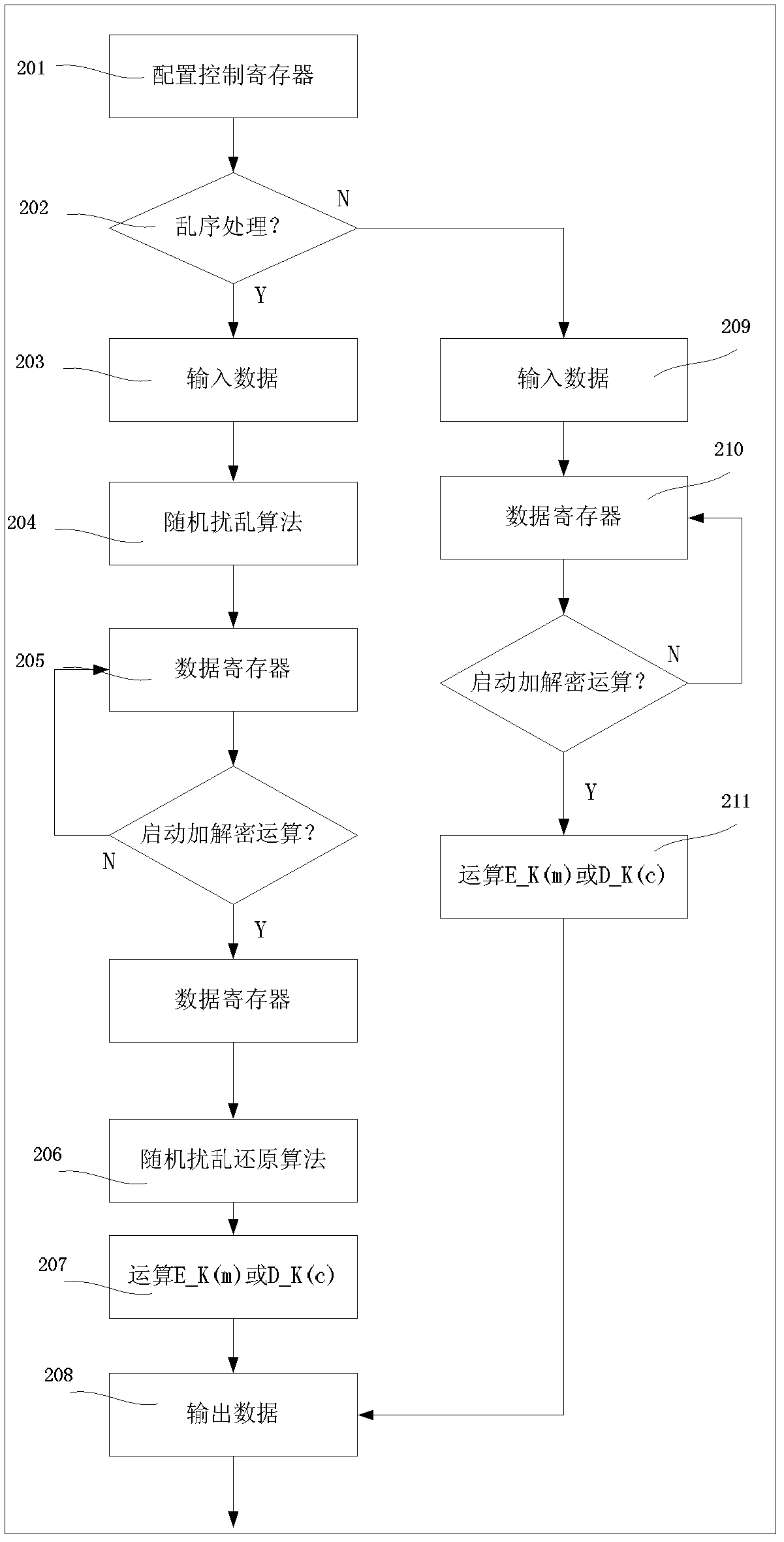
[0029] This technology performs jamming protection on the following two parts.
[0030] Scramble the data input to the register. Disturb the plaintext or key when it is input, for example, use the random number mask method to cover the plaintext or key, and prevent the attacker from obtaining the plaintext or key information through register attack or Hamming distance attack.
[0031] Disturbance protection is performed on the circle operation result in the circle data register. Prevent attackers from obtaining circle operation result information through register attack or Hamming distance attack.
[0032] Such as figure 2 As shown, a circuit for defending against grouping algorithm energy attacks, which includes: a circle operation module, a circle key generation module, a data random disturbance restoration unit, a circle data random disturbance restoration unit and a MUX2_1 module; the data random disturbance restoration unit , the MUX2_1 module, the circle data random ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com