Color character encoding method and decoding method
A technology of encoding method and decoding method, which is applied to record carriers, instruments, computer parts, etc. used by machines, can solve the problems of low security of anti-counterfeiting code technology and affect the appearance of products, and achieves good concealment and production methods. Novel and improve the effect of anti-counterfeiting code technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
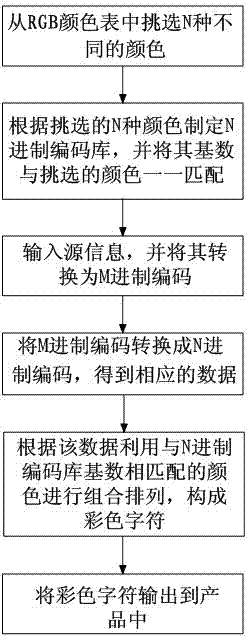
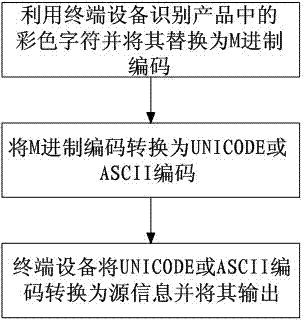
[0043] The present invention is a technical solution for combining the anti-counterfeiting code and color to output and decode the anti-counterfeiting code, such as figure 1 As shown, the encoding process is as follows:
[0044] (1) Select N different colors from the RGB color table, and N is a natural number greater than or equal to 2. For the convenience of identification, the N colors here can give priority to colors with greater contrast, such as black and white;
[0045] (2) Formulate an N-ary encoding library based on the selected N colors, and match the selected N colors with the bases of the N-ary encoding library one by one. Here, it specifically refers to the number of colors selected by the server system N establishes a binary encoding library equal to its value, that is, an N-ary encoding library. The N-ary encoding library follows the conversion rules of the binary system, and its bases are 0, 1, 2... (N-1), and the selected color N 0 , N 1 , N 2 ...N n-1 Mat...
Embodiment 2
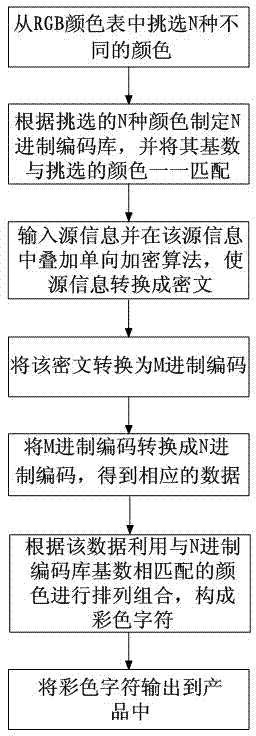
[0064] Such as image 3 , 4 As shown, the difference from Embodiment 1 is that Embodiment 1 is the encoding and output of non-encrypted source information. In this embodiment, one-way encryption is superimposed on the source information before it is converted into M-ary encoding. algorithm (such as MD5 one-way encryption algorithm or two-way MD5 one-way encryption algorithm), and when decoding, after converting the M-ary code into UNICODE or ASCII code, it is also decrypted with a one-way decryption algorithm, and then The source information is converted, and the encoding and output of the entire source information are in the state of encryption and decryption. This embodiment takes the secondary MD5 one-way encryption algorithm as an example to illustrate the encryption and decryption process of this embodiment:
[0065] Take binary and ternary conversion as an example, that is, set M=2, N=3, select three colors of black, red, and blue, and then build a ternary encoding lib...
Embodiment 3
[0069] Such as Figure 5 , 6As shown, the difference from Embodiment 1 is that Embodiment 1 is the encoding and output of non-encrypted source information. In this embodiment, a simple encryption algorithm is superimposed on the source information before it is converted into M-ary encoding. (such as dictionary conversion encryption algorithm, N-ary displacement encryption algorithm, N-ary digit transformation encryption algorithm, character displacement encryption algorithm, logic or transformation encryption algorithm, logic and transformation encryption algorithm, logic XOR transformation encryption algorithm or four mixed operation transformation Encryption algorithm), and when decoding, after converting the M-ary code into UNICODE or ASCII code, it is also decrypted with a simple decryption algorithm. This embodiment takes the character displacement encryption algorithm as an example to illustrate the encryption and decryption process of this embodiment:
[0070] Take bi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com