Unicast secret communication method and multicast secret communication method based on identity
A technology for confidential communication and identity information, applied in key distribution, it can solve problems such as complex key management, and achieve the effect of simple key management and ensuring privacy and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
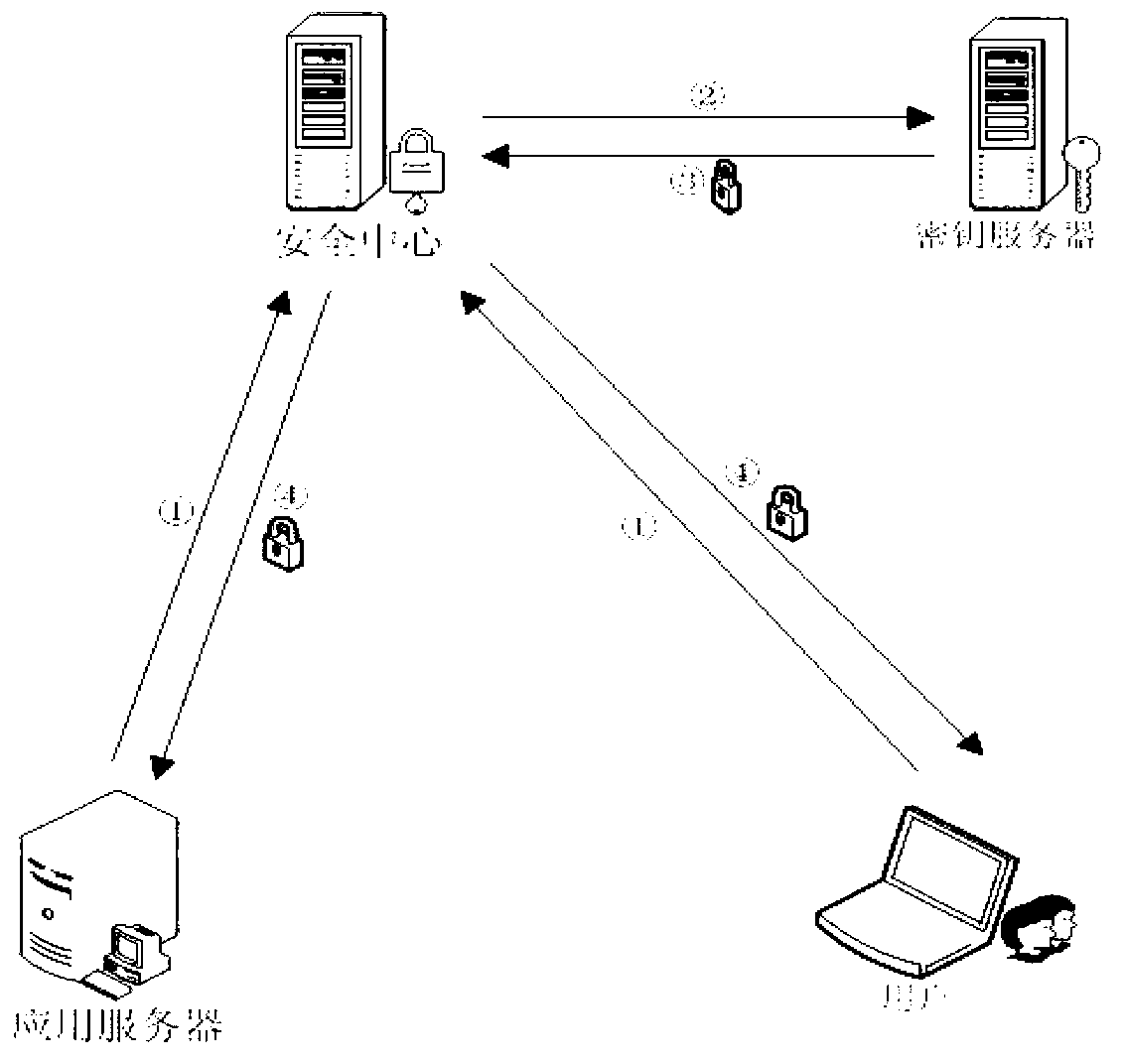
[0024] The invention proposes an identity-based unicast secure communication method and a multicast secure communication method, and uses identity-based passwords to ensure the privacy and security of legal user operations. Different from the traditional PKI / CA technical mechanism, in the identity-based cryptographic system, the user's public identity information (such as e-mail address, IP address, name, etc.) is used as the public key part of the user's public key / private key pair. Private keys are generated by a trusted third party called a Private Key Generator (PKG). An identity-based cryptosystem such as figure 1 As shown, it consists of a security center and user groups. The security center provides key management services to users. Users use secure cryptographic algorithms to implement cryptographic operations and processing such as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com