Safety equipment, multi-application system and safety method for ubiquitous networks
A security device and security technology, applied in the transmission system, climate change adaptation, electrical components, etc., can solve problems such as single access mode, lack of security guarantee, and failure to consider the characteristics and advantages of multi-network integration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
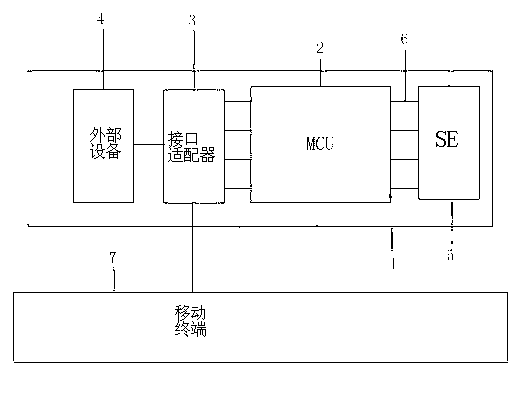
[0027] Embodiment 1: A security device for ubiquitous network, such as figure 1As shown, it includes that the device may at least include a casing 1 of PC plastic or silicone material, a main control chip AU6438BS as MCU 2, an interface adapter 3 and corresponding external equipment 4; MCU 2 is connected to 30-pin, 8-pin interface adapter 3, and send and receive instructions on the bus 6 to control the corresponding external device 4 through the interface adapter 3; it is characterized in that the external device 4 includes at least a security module MicroSD financial IC card SE 5, also includes a transceiver, an amplifier , antenna, iPhone mobile phone or Android mobile phone 7 docked with the interface adapter 3; the SE 5 is used to store keys, digital certificates, biometric identification information, personal privacy information, and contract service information, and the contract service information includes The network priority method, security method, transaction method...
Embodiment 2
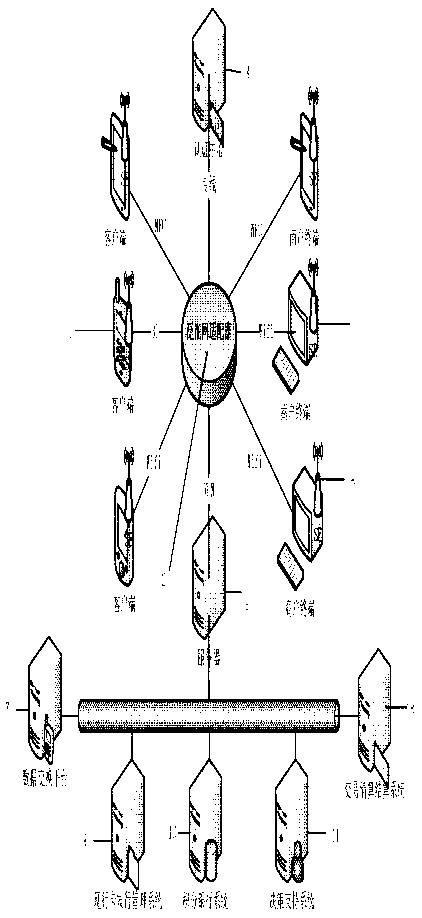
[0028] Embodiment 2: A multi-application system using ubiquitous network-oriented security equipment, such as figure 2 As shown, it at least includes a client 1, a ubiquitous network adapter 2, a merchant terminal 3, an authentication center 4, a server 5 and a security device SE 6; it is characterized in that the security device 6 includes at least a PC plastic shell, A main control chip AU6438BS is used as an MCU, a 30-pin, 8-pin interface adapter and an iphone correspondingly connected to it, the MCU is connected to the interface adapter through a bus, and the external device includes at least one MicroSD financial IC card security Module SE, the SE is an IC card with an on-chip operating system, the IC card stores keys, digital certificates, biometric identification information, personal privacy information, and contract service information, and the contract service information includes ubiquitous Network optimization methods, security methods, and transaction methods for...
Embodiment 3
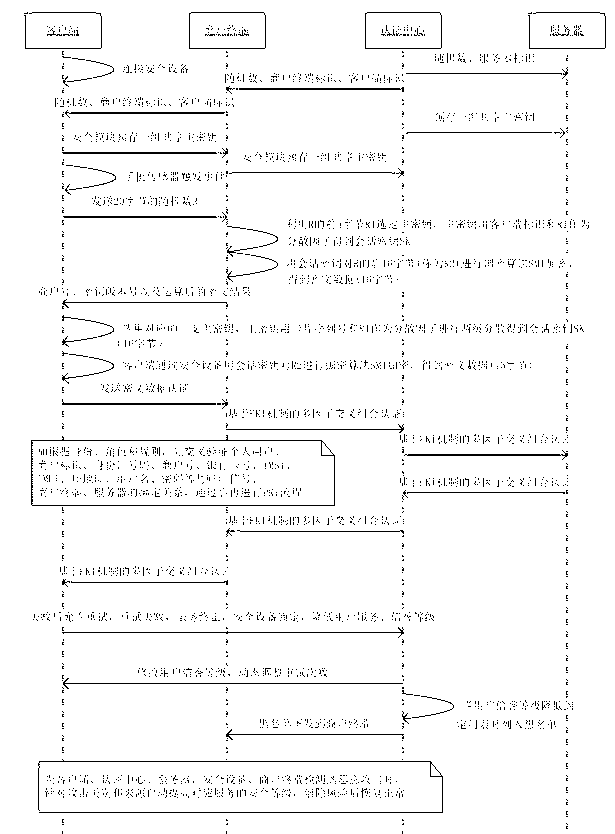
[0030] Embodiment 3: A security method using a multi-application system for ubiquitous network security equipment, such as image 3 As shown, it is characterized in that it includes at least the following steps:
[0031] ①Individual users and merchants sign up for services. According to the server information, the authentication center uses multiple people to input passwords, server IDs and keys, authentication center keys, and at least two factors of the random numbers generated to randomly generate system keys. Security-level keys, using the merchant terminal identifier, client identifier, and random numbers generated, according to the contract information and combined with the merchant terminal's own security equipment such as POS, personal user security equipment such as MicroSD financial smart card identification, such as smart cards serial number, generate a master key, pre-set a set of master keys shared by both parties on the merchant terminal POS and the security modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com