User unified authentication method in cloud computing environment
A cloud computing environment and authentication method technology, applied in user identity/authority verification, transmission systems, electrical components, etc., can solve problems that cannot meet user security needs, achieve convenient maintenance, improve security, and reduce password leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
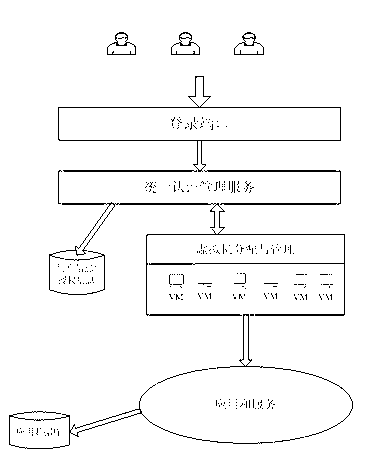
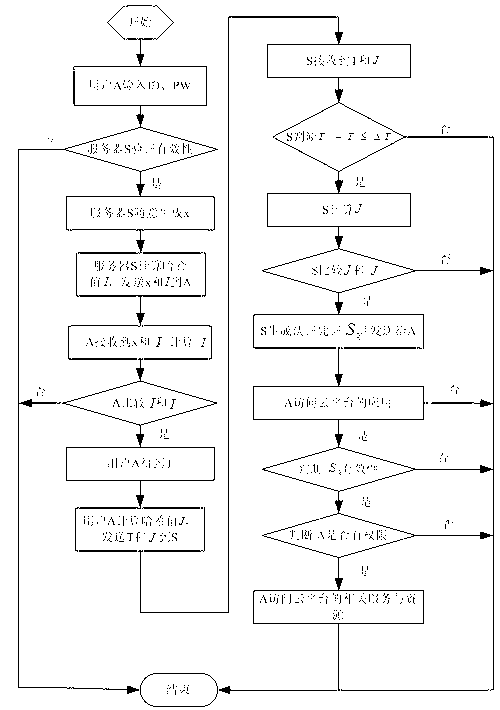
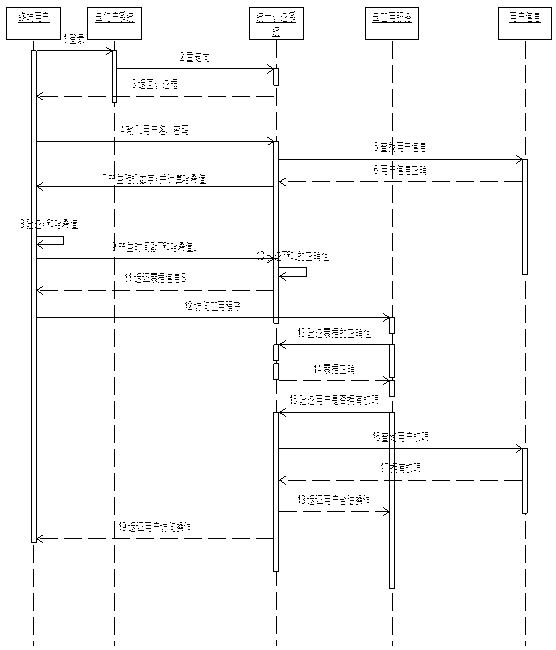
[0028] Cloud computing offers many advantages over traditional models, such as information sharing in a virtual environment, dynamic scalability, virtualization of software, platforms, and storage, and so on. However, in addition to the many benefits that cloud computing has brought to people, many problems have arisen, such as: performance issues, fault tolerance, interoperability, data migration and conversion from legacy systems, etc. The main problem is security, such as virtualization Security, application security, identity management, access control and authentication, and the management of identity authentication and access control are the core requirements of cloud computing. Therefore, the above security issues prompt us to propose a reliable and strong identity authentication for cloud environments Framework diagram to ensure that only authenticated users can enter the cloud environment. To this end, we propose a unified user authentication architecture based on clo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com