Online bank security protection method
A technology for security protection and online banking, which is applied to key distribution, can solve the problem of low security of online banking login, and achieve the effects of eliminating malicious operations, ensuring reliability, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
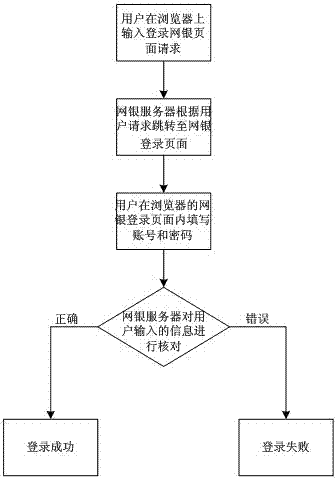
[0046] Such as figure 1 As shown, the traditional online banking login method is that the online banking server is always open to the outside world. Any user can process the funds in the corresponding account as long as they enter the correct login information at any point in time. It is precisely because the online banking server is always open to the outside world. Therefore, in the prior art, online banking users are encouraged to set more complex passwords and use K treasure, U-shield, etc. The above online banking security protection methods can only improve the security of online banking to a limited extent, and cannot fundamentally solve the security problem of online banking .
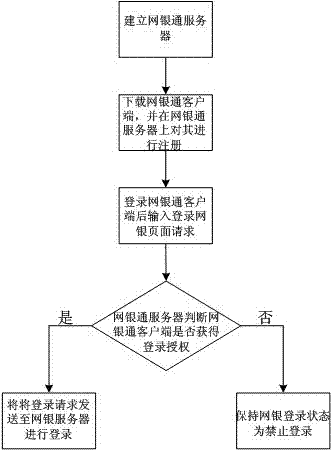
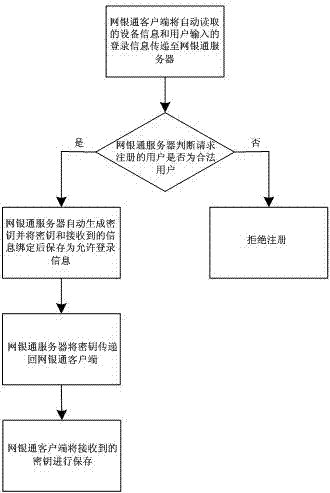
[0047] Such as figure 2 As shown, based on the above-mentioned defects, the present invention abandons the online banking login method in the prior art that only treats symptoms but not the root cause, and establishes an online banking server that supervises the prohibited login status and al...
Embodiment 2
[0062] Such as Figure 6 As shown, the difference between this embodiment and Embodiment 1 is that the online banking login operation steps after obtaining the login authorization are as follows: When the user accesses the online banking login page, the user enters the online banking login account number and password in the browser, and the login The request is sent to the Internet Banking Server to verify whether the user is allowed to log in, so as to further ensure the legitimacy of the logged-in user, and when it is judged that the user who requested to log in is a verified user who is allowed to log in, it will reply that the online banking login has been authorized successfully, and log in here After the request is satisfied, the login information is sent to the online banking server for login authentication, and the online banking server deletes the allowed login user from the allowed login list, and refuses to log in if the user is not allowed to log in.
Embodiment 3
[0064] Such as Figure 7 As shown, the difference between this embodiment and Embodiment 1 is that the online banking login operation steps after obtaining the login authorization are as follows: When the user accesses the online banking login page, the user enters the online banking login account number and password in the browser of the user terminal and Submit a login request, and after receiving the login request, the online banking server sends the login request to the NetBank server to verify whether the user is a user allowed to log in, and when it is determined that the user requesting login is a verified user allowed to log in, the online banking server will directly perform regular login Authentication, the NetBank server deletes the allowed login user from the allowed login list to prevent others from using the gap to log in again, and refuses to log in if the user is not allowed to log in.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com