A network protocol analysis method for malicious code
A malicious code and analysis method technology, applied in the direction of electrical components, transmission systems, etc., can solve the problem of weak semantic understanding of protocol fields, etc., and achieve the effect of clear syntax division process, accurate division results, and clear and accurate division results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
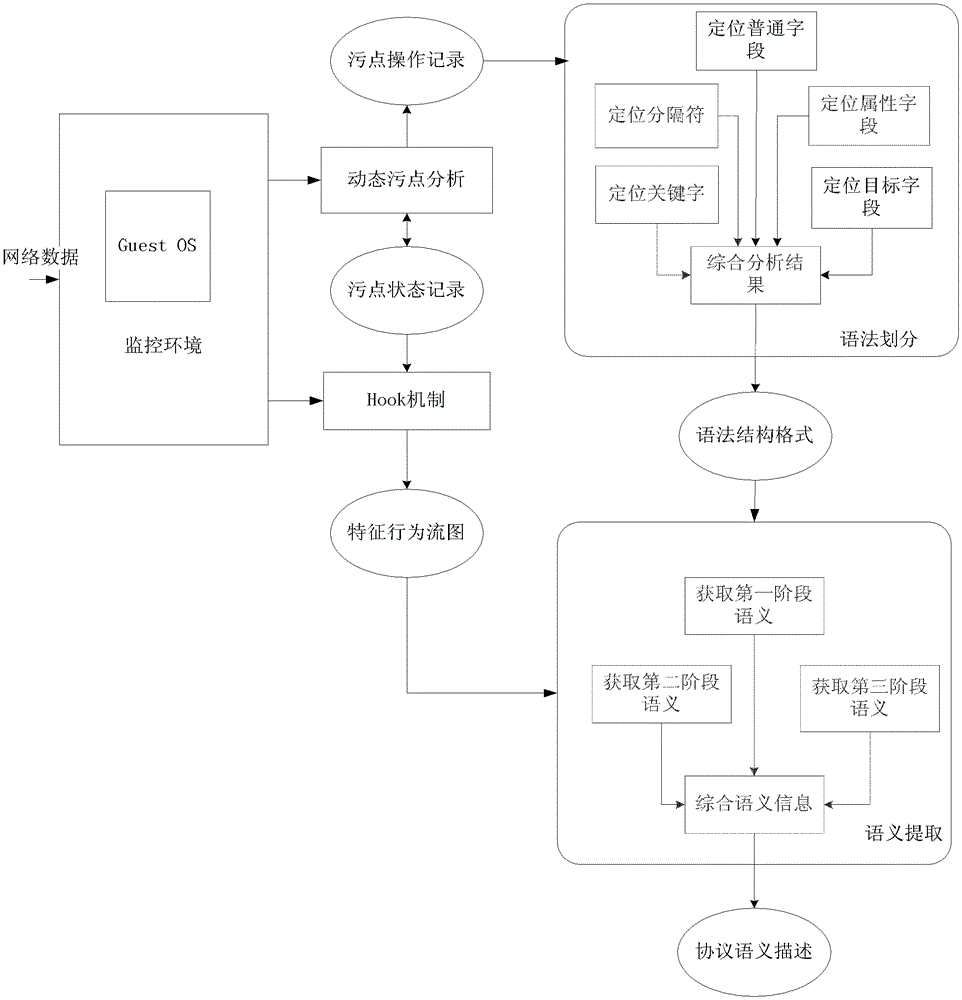
[0017] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
[0018] As shown in the figure, a malicious code network protocol analysis method based on dynamic taint analysis is implemented as follows:
[0019]1. Deploy the malicious code to be analyzed in the monitoring server, monitor its network operation, and use the received network data as the original taint source data; use the taint analysis engine to track and record all the taint operation instructions it has executed, and use The row organization of the "instruction-level taint propagation flow graph" is recorded. Each node in the graph corresponds to a taint instruction. The present invention records the stain information record of each stain byte in the stain operand. What is recorded in the taint record is one or more unsigned integers, which (they) are addresses of certain (certain) bytes in the original taint source. The taint information record...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com