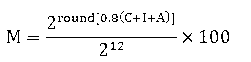Safety margin risk quantification method
A quantitative method and security domain technology, applied in the fields of platform integrity maintenance, transmission system, electrical components, etc., can solve problems such as inconvenient risk level division, inaccurate risk quantification results, and limit of risk quantification value, so as to achieve convenient risk assessment results The effect of contrast
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
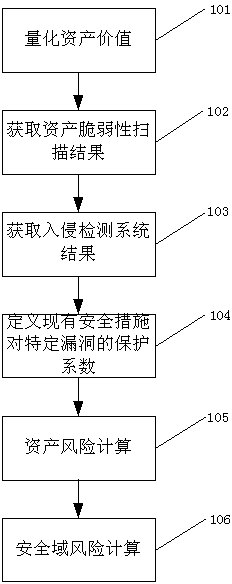
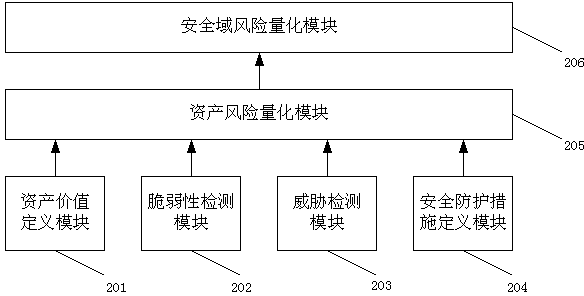
[0027] This embodiment is a security domain risk quantification process, such as figure 1 shown, including the following steps:
[0028] Step 101: Quantify the value of the asset into a specific value between 0-100 according to the confidentiality, integrity, and usability scores of the asset. (For the definition and calculation method of the confidentiality, integrity and availability of assets, please refer to the National Standard of the People's Republic of China "GBT 20984-2007 Information Security Technology Information Security Risk Assessment Specification").
[0029] Step 102: Obtain vulnerability information on assets by means of vulnerability scanning or by importing detection results from other vulnerability scanning devices.
[0030] Step 103: Obtain attack alarm events for assets through intrusion detection or by importing detection results from other intrusion detection devices.
[0031] Step 104: According to the configuration of the existing security equipme...
Embodiment 2
[0035] This embodiment is a specific method for asset value quantification, including the following process:
[0036] (1) Rating asset confidentiality C, integrity I and availability A respectively, and each attribute is divided into 5 grades: irrelevant, ordinary, medium, high, and extremely high; each grade uses a score of 1-5 express.
[0037] (2) Use the following methods to quantify the asset value:
[0038]
[0039] Among them: M - quantitative value of asset value;
[0040] round()——a rounding rounding function;
[0041] C, I, A - asset confidentiality, integrity, availability scores.
Embodiment 3
[0043] This embodiment is a calculation method for the possibility of asset security damage, and the calculation process is:
[0044]
[0045] Among them: T——possibility of damage to asset security;
[0046] Evt——quantified value of attack behavior threat level;
[0047] f()——attack-asset correlation judgment function;
[0048] s()——The protection factor of existing security measures against vulnerabilities.
[0049] The calculation process of each factor in the calculation formula is described below.
[0050] First, according to the degree of harm caused by the attack behavior and the difficulty of implementing the attack behavior, the threat level of the attack behavior is divided into five levels, as shown in Table 1:
[0051] ,
[0052] Then use the following method to quantify the threat level of attack behavior:
[0053]
[0054] Among them: Evt——quantified value of attack behavior threat level;
[0055] level——The attack behavior threat level....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com