User Behavior Pattern Mining System and Method
A pattern mining and behavioral technology, applied in special data processing applications, instruments, electrical digital data processing, etc., to achieve the effects of convenient configuration, safety assurance, and enhanced protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings in the form of embodiments.
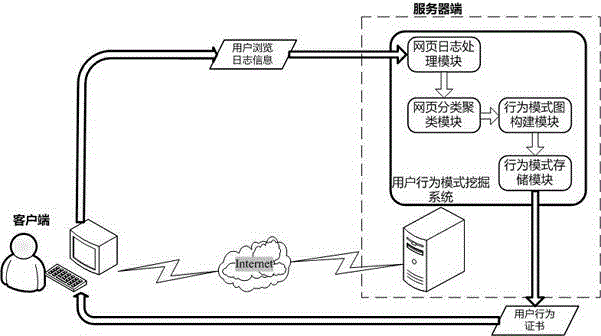
[0029] Such as figure 1 The architecture diagram of the user behavior pattern mining system is shown. The entire user behavior pattern mining system is deployed on the server side, accepts the user browsing log information submitted by the client, mines the user behavior pattern map, and generates a user behavior certificate for release to the client. terminal download.
[0030] User web page log processing module: In order to facilitate the maintenance and management of a large number of web page records formed by users accessing the Internet, the web page log information is stored in XML files. Therefore, when it is necessary to process and mine these web page log information, it is necessary to parse the XML file through data preprocessing to obtain these web page log information. At the same time, all the acce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com