Network anomaly traffic monitoring method and device
A traffic monitoring and network anomaly technology, applied in the field of information security, can solve the problems of no confidence in the output results, low false detection rate, no low false detection rate, etc., and achieve output with result confidence, low false detection rate and false detection rate. The effect of high detection rate and low false detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
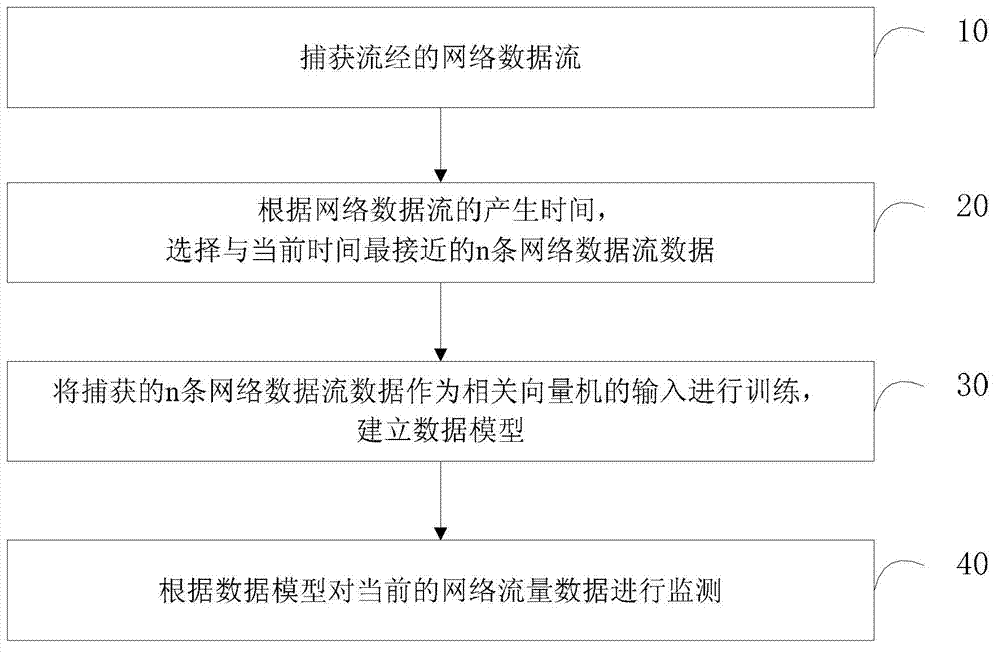
[0063] see figure 1 , which is a flow chart of the principles of the method for monitoring abnormal network traffic provided in this embodiment, specifically as follows:
[0064] Step 10, capturing the passing network data flow.
[0065] In this embodiment, for the monitoring of network abnormal traffic, it is first necessary to capture the unknown traffic in the network, and the captured network data flow data needs to be input into the relevant vector machine for training on the one hand, so as to establish a historical data model, and judge through the data model Whether the subsequent network data flow is abnormal. On the other hand, it is also necessary to continuously capture the current passing network data flow in order to predict the abnormality of network traffic in real time.
[0066] Step 20, according to the generation time of the network data stream, select n pieces of network data stream data closest to the current time.
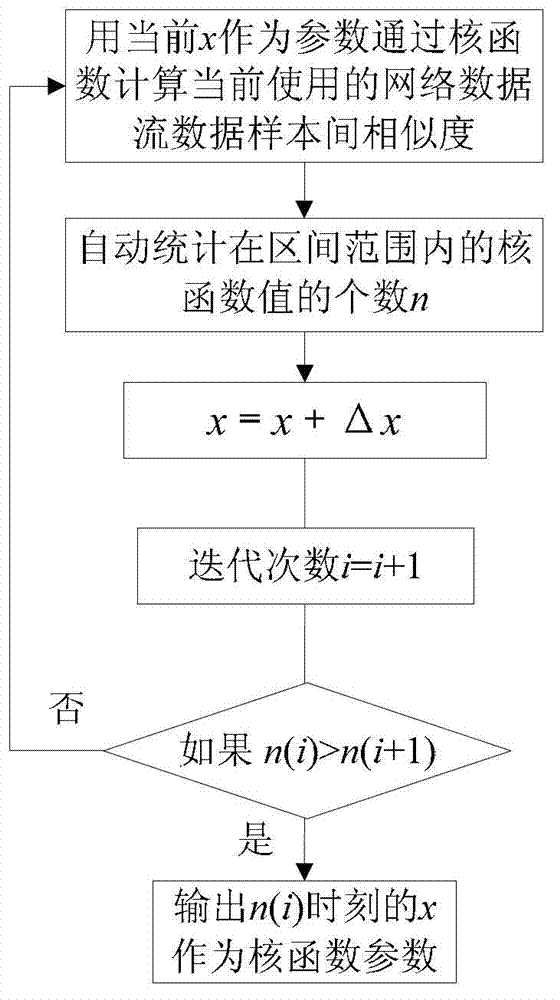
[0067] Here, how to select appropria...
Embodiment 2
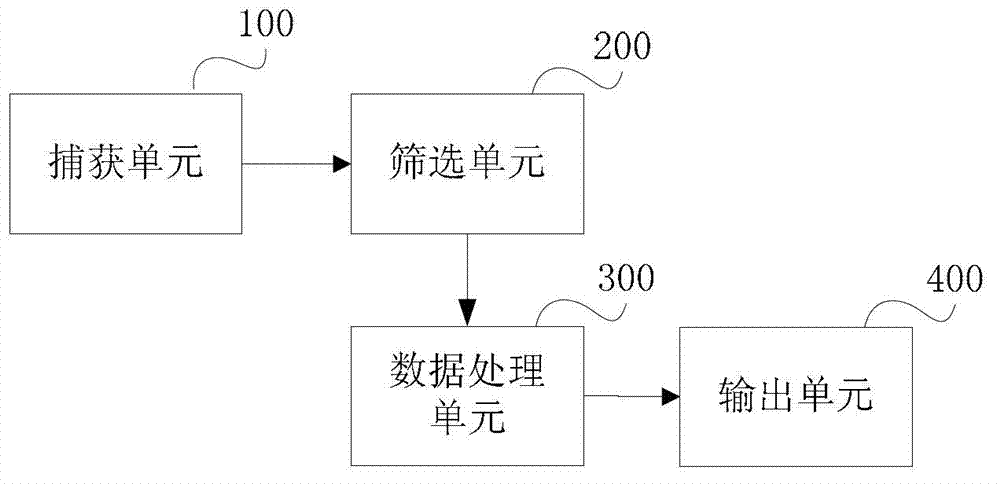
[0103] see image 3 , the embodiment of the present invention provides a network abnormal traffic monitoring device, the device includes a capture unit 100, a screening unit 200, a data processing unit 300 and an output unit 400, specifically as follows:
[0104] A capturing unit 100, configured to capture network data streams passing through;
[0105] The screening unit 200 is used to select n pieces of network data stream data closest to the current time according to the generation time of the network data stream; n is determined according to the computing power of the device;
[0106] The data processing unit 300 is used to train the captured network data flow data as the input of the correlation vector machine, and establish a data model;
[0107] The output unit 400 is configured to monitor current network traffic data according to the data model.
[0108] Preferably, the above device further includes a denoising unit 500, configured to perform denoising processing on t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com