Mobile information system based privacy protection and encryption method
A privacy protection and mobile information technology, applied in the field of privacy protection encryption, can solve problems such as the content of unidentifiable information, and achieve the effect of solving the speed of plaintext encryption and decryption, solving key distribution, and ensuring authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to make the above-mentioned functions, processes and advantages of the present invention more obvious and easy to understand, the related technologies involved in the present invention will be introduced in detail one by one below.
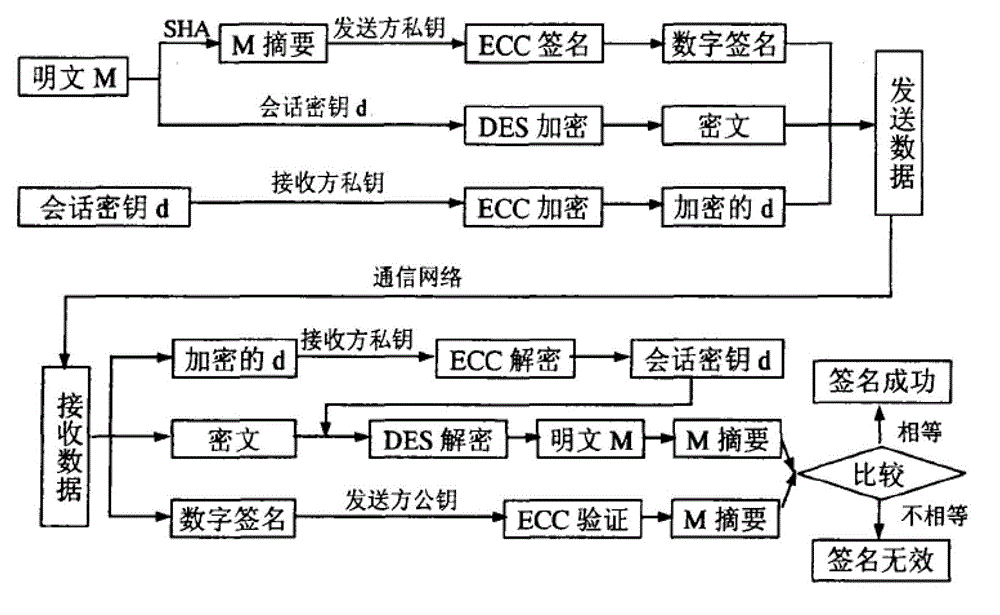
[0037] In the privacy protection encryption method of the mobile information system in this embodiment, the source needs to do three tasks, including digital digest generation, plaintext encryption and session key encryption. The destination also includes three tasks, which are session key decryption, ciphertext decryption and digital signature verification. The specific working process is as follows:
[0038] (1) The sender uses the SHA function to form a digital digest of the plaintext M, and uses the sender's private key and the ECC digital signature algorithm to sign and generate a digital signature.
[0039] (2) The sender uses the session key d to perform DES encryption of plaintext to generate ciphertext.
[0040] (3) The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com