A method and device for distributing tunnel connection requests
A connection request and tunnel connection technology, applied in the field of data communication, can solve problems such as unfavorable large-scale commercial applications and incompatibility with standard methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
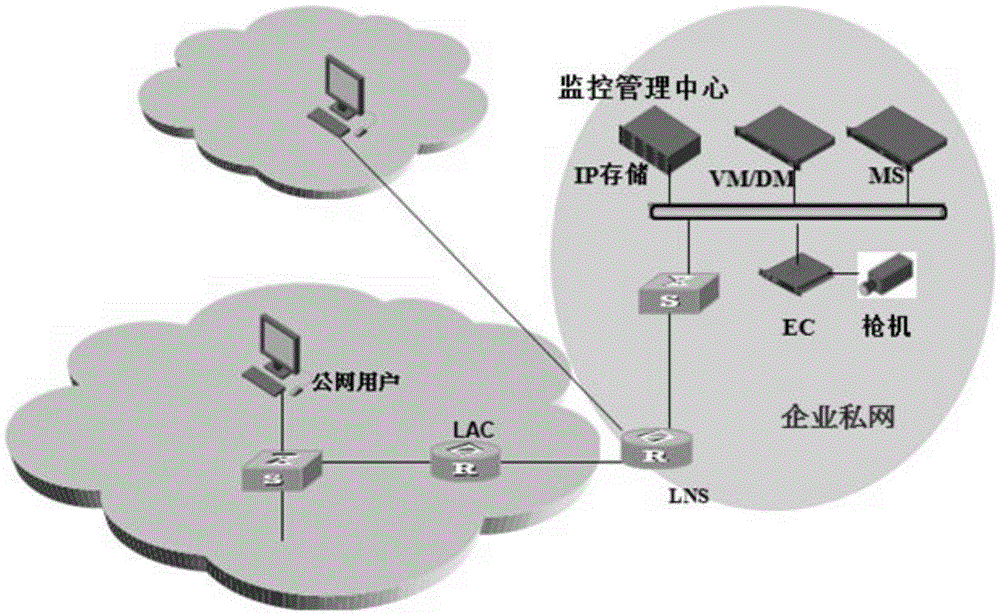
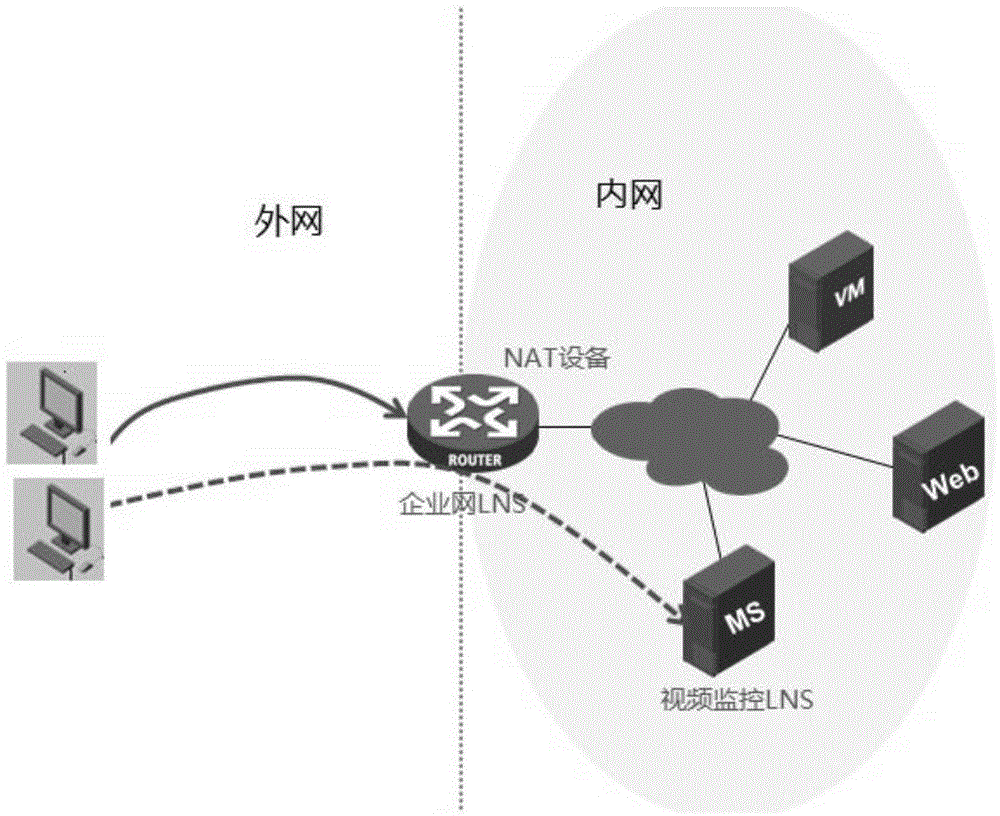
[0017] The present invention performs special processing in the authentication stage of the L2TP connection request, and under the premise of basically guaranteeing the user experience, intelligently identifies the user's L2TP connection request, and distributes the user's L2TP connection request to different service network front-end LNS servers for processing . The detailed implementation in the preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings.
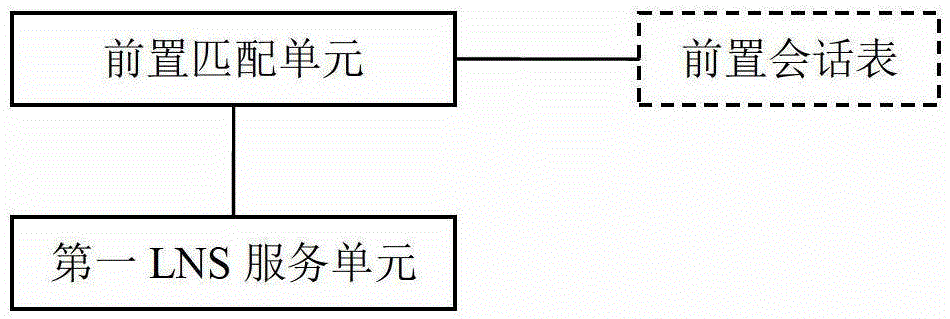
[0018] Please refer to figure 2 , image 3 as well as Figure 4 , The present invention provides a device for distributing tunnel connection requests. In a preferred embodiment, the present invention is realized by using a computer program, the device runs on the NAT gateway, and includes a pre-matching unit and an LNS service unit. The following describes the processing flow of the device running on the NAT gateway and cooperating with the existing functions o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com