A character terminal telnet protocol security access system and method
A character terminal and protocol security technology, applied in transmission systems, electrical components, etc., can solve problems such as support difficulties, upgrade systems, troubles, etc., and achieve the effect of guaranteeing equipment investment and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
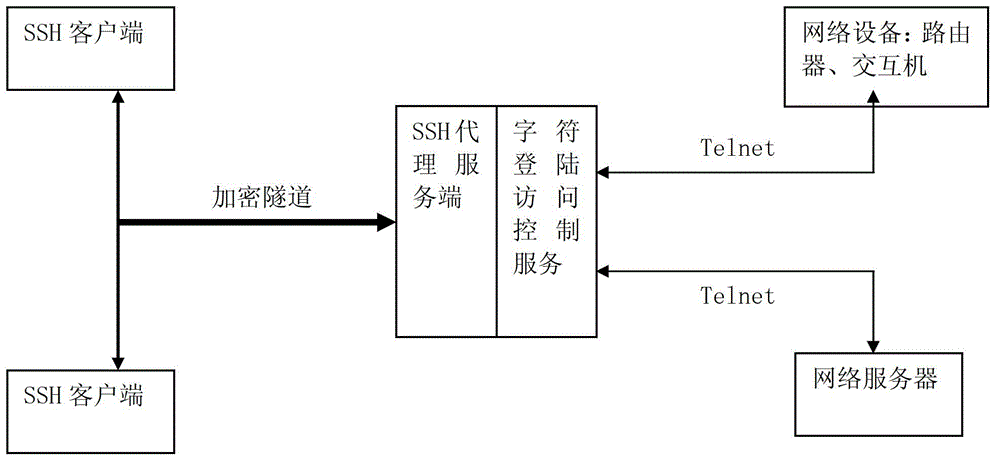
[0026] This embodiment provides a character terminal Telnet protocol security access system, connecting such as figure 1 As shown, the system of this embodiment is integrated in the "network security access system".
[0027] The network security access system needs to assign two addresses, one address is used for direct access from the external network, and the other is used for internal network access. The network security access system integrates the SSH proxy server and character login access control server.
[0028] SSH proxy server: used for the client to log in to the SSH connection of the intranet, verify the identity, and select the device to be accessed;
[0029] Character login access control server: It is used to connect to the selected access device (such as: unix server, switch) with the specified TELNET login protocol, and convert the data between encryption and non-encryption, and at the same time perform command keyword Monitor and block commands if necessary....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com