Software safety function component management method based on CC (the Common Criteria for Information Technology Security Evaluation)
A technology of security functions and functional components, applied in computer security devices, electronic digital data processing, instruments, etc., can solve problems such as difficulty in use by ordinary users, subjective bias, etc., and achieve the goal of reducing dependence, reducing possibilities, and improving security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
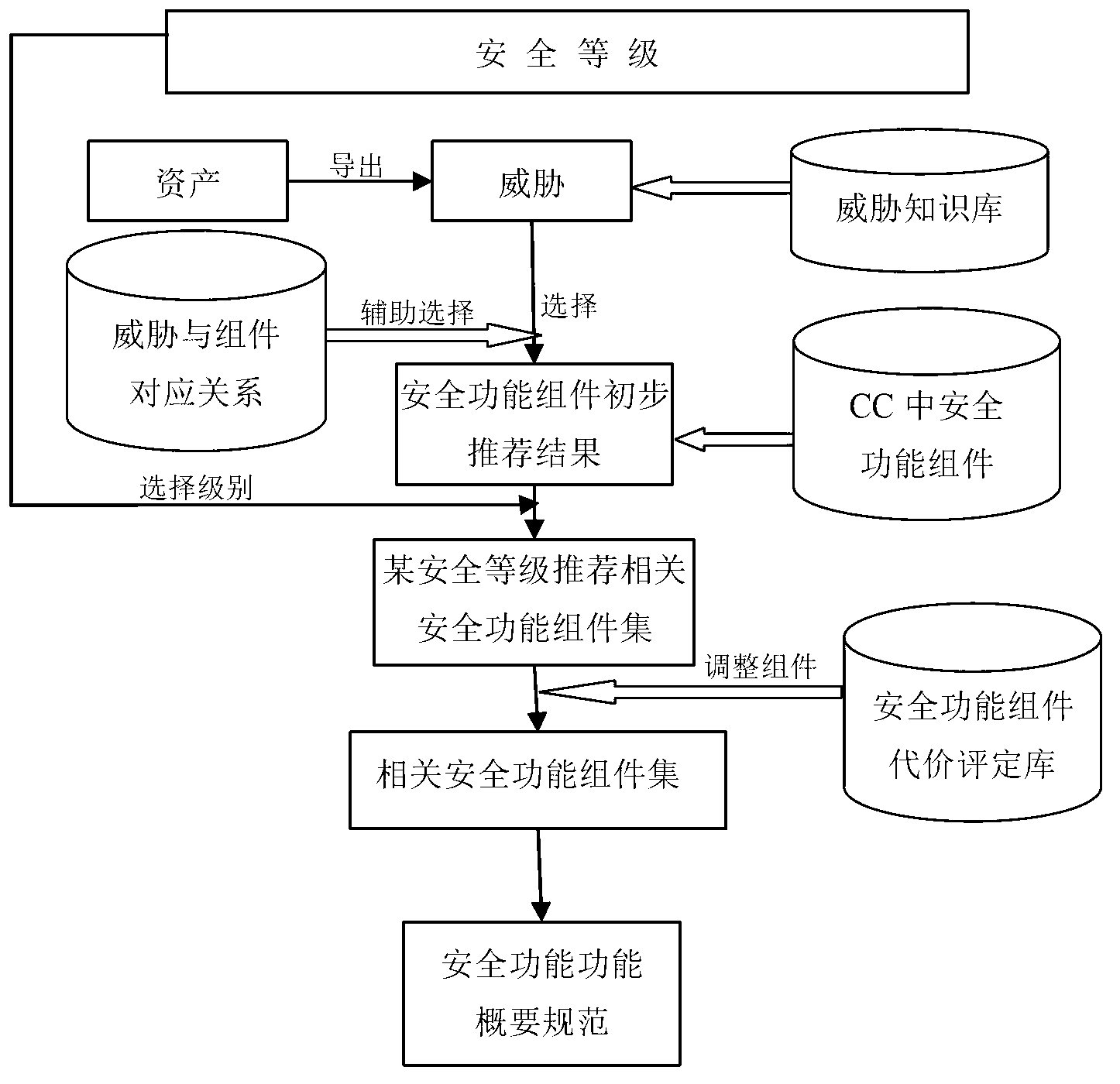
[0043] 1. The abstraction of threat knowledge
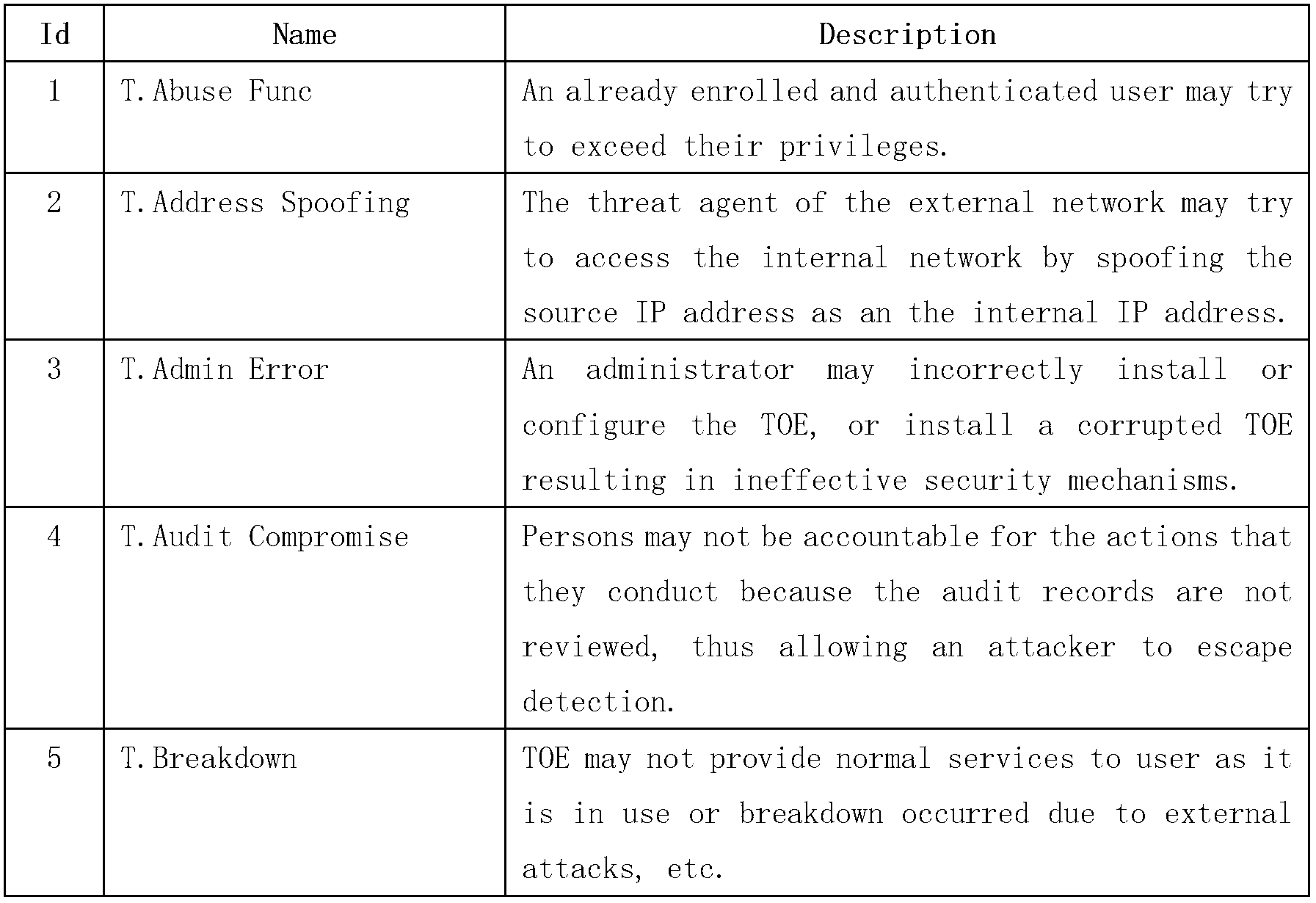
[0044] Referring to the threat knowledge in the evaluation documents in various fields under the CC standard system (including the protection profile document PP and the security target document ST), 22 threats are preliminarily abstracted according to the preconditions of the threat, the field of occurrence, and the severity of the consequences category. See Schedule 1.
[0045] Table 1 Abstract summary of threat information
[0046]
[0047]
[0048]
[0049] 2. Establish correspondence between threats and security function components
[0050] The total number of security function components is 251, so the correspondence between threats and security function components is one-to-many. As shown in Table 2 below, it shows the corresponding relationship between the level and the 11 safety function categories. According to the possible threats of this level, the corresponding security function components can be selecte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com