Method and device for controlling hyper text transport protocol (HTTP) traffic
A control method and flow technology, applied in the field of network security, can solve the problems of unsatisfactory application effect, inability to distinguish normal web service access HTTP traffic and abnormal HTTP traffic, etc., and achieve better defense effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
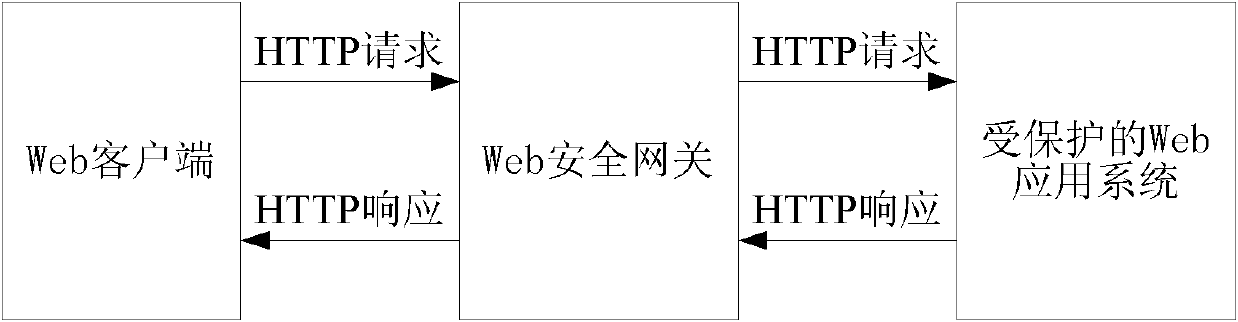
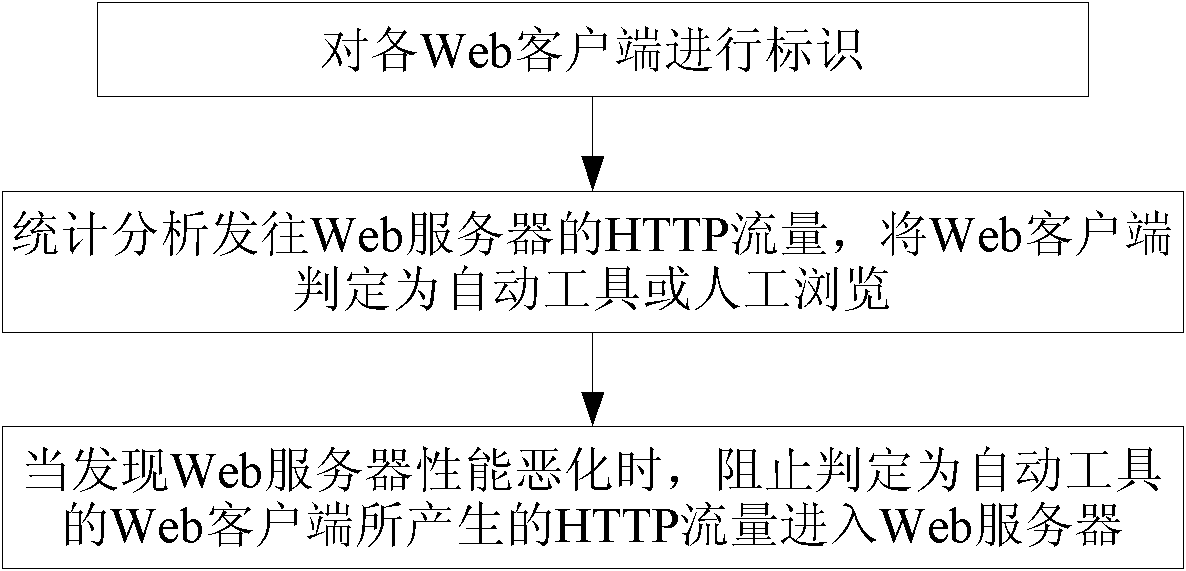
[0049] Embodiment 1, a method for controlling HTTP traffic, which can be but not limited to be used on a web security gateway, including:
[0050] According to the HTTP traffic sent to the Web server by the Web client, it is determined that the Web client is an automatic tool or manual browsing;
[0051] Only the HTTP traffic generated by the Web client determined to be manually browsed is allowed to enter the Web server.
[0052] That is to say, for the HTTP flow that is determined as the Web client that the automatic tool produces, prevent it from entering the described Web server, such as directly discarding the HTTP request, or not processing it until it is covered by a new HTTP request; if the result of the determination is If not sure, the leaky bucket algorithm known in the field of network service quality can be used to send the HTTP request to the Web server at a pre-agreed forwarding rate, and it can also be prevented from entering the Web server in practical applica...
Embodiment 2
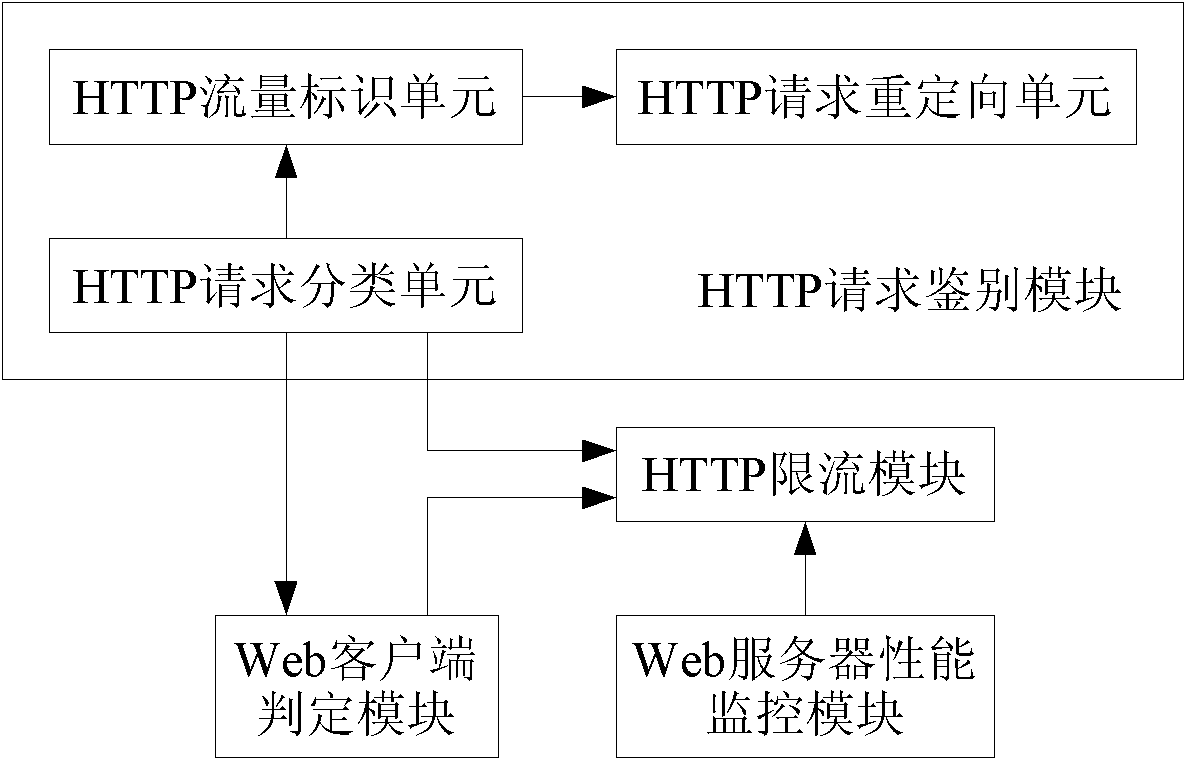
[0090] Embodiment 2, a device for controlling HTTP traffic, which can be used on a security gateway, such as image 3 shown, including:
[0091] Web client judging module: used to determine that the Web client is an automatic tool or manual browsing according to the HTTP traffic sent to the Web server by the Web client;
[0092] The HTTP current limiting module is used to only allow the HTTP flow generated by the Web client judged as manual browsing to enter the Web server.
[0093] In the present embodiment, the judgment result of described Web client judgment module can have three kinds: A) Web client is an automatic tool; B) Web client is manual browsing; C) current behavior is unknown; Described HTTP current limiting module according to The judgment result of described Web client judgment module determines the next action for HTTP request: if the judgment result of the Web client that sends this HTTP request is an automatic tool, then can but not limited to directly disca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com