Out-of-band authorization safety reinforcement method for cloud computing platform
A cloud computing platform and cloud platform technology, applied in the field of cloud computing security, can solve problems such as access to core data, program operation and customer sensitive information security problems have not been well resolved, gain control over program operation, etc., to achieve defense The effect of illegal access, hacker defense, high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be described in detail below with reference to the accompanying drawings.
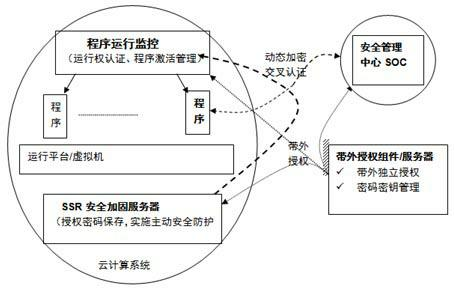
[0019] A cloud computing platform out-of-band authorization security reinforcement method of the present invention is composed of a complete application system based on the present invention, which generally includes a security reinforcement server SSR, an out-of-band authorization component (or system), a cloud computing platform program operation monitoring component, and an external security system. There are four parts in the management center, the detailed working process can be found in figure 2 .
[0020] If there is no external security management center, a high-intensity security protection system can also be formed from other program parts, but the level (or reliability) of security protection is reduced.
[0021] Using the active defense technology based on out-of-band encryption authorization and security hardening server SSR, the program on the cloud com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com