System and method for detecting access control strategy collision in collaborative environment
An access control policy and conflict detection technology, applied in transmission systems, digital transmission systems, instruments, etc., can solve autonomous domain access control policy conflicts, reduce the security of computer network systems, and do not consider the semantic heterogeneity of access control policies, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
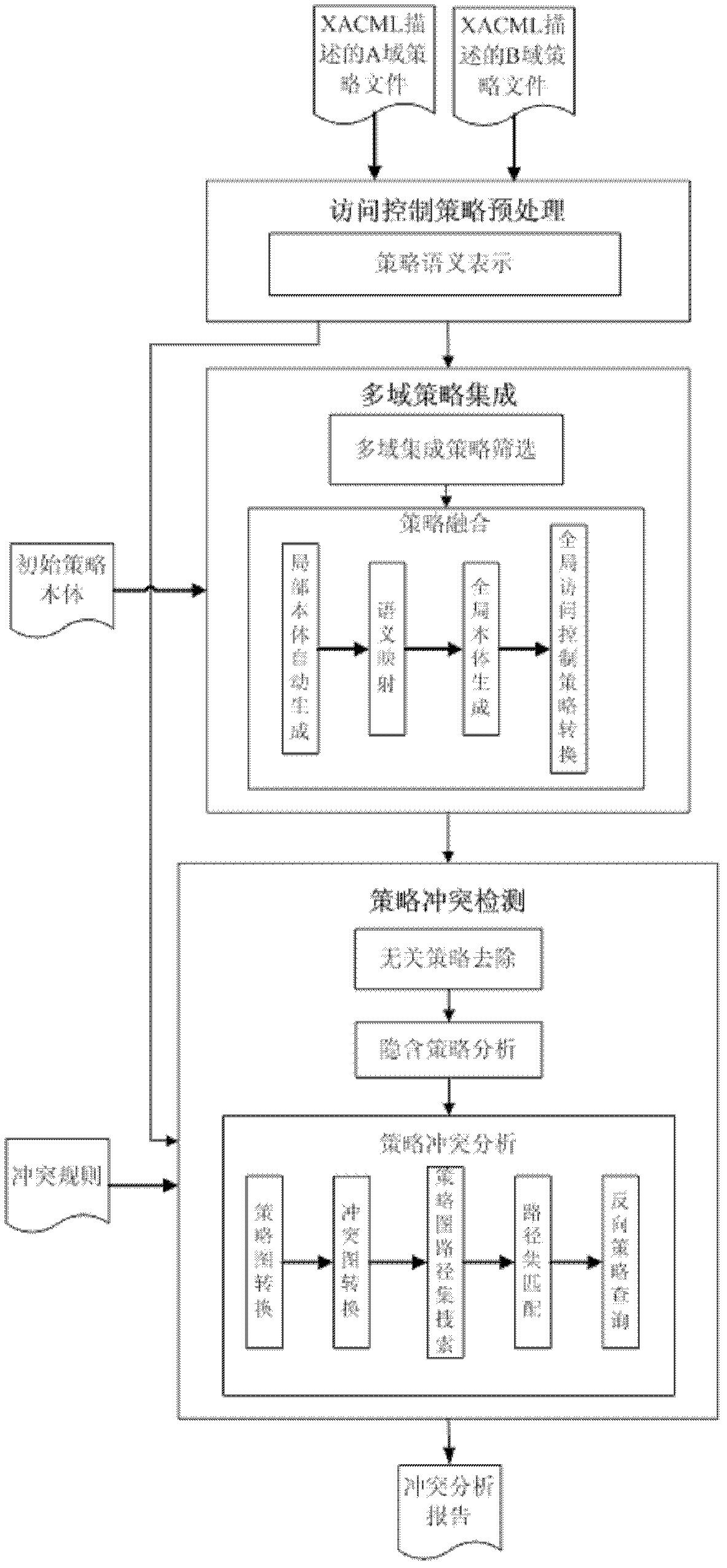
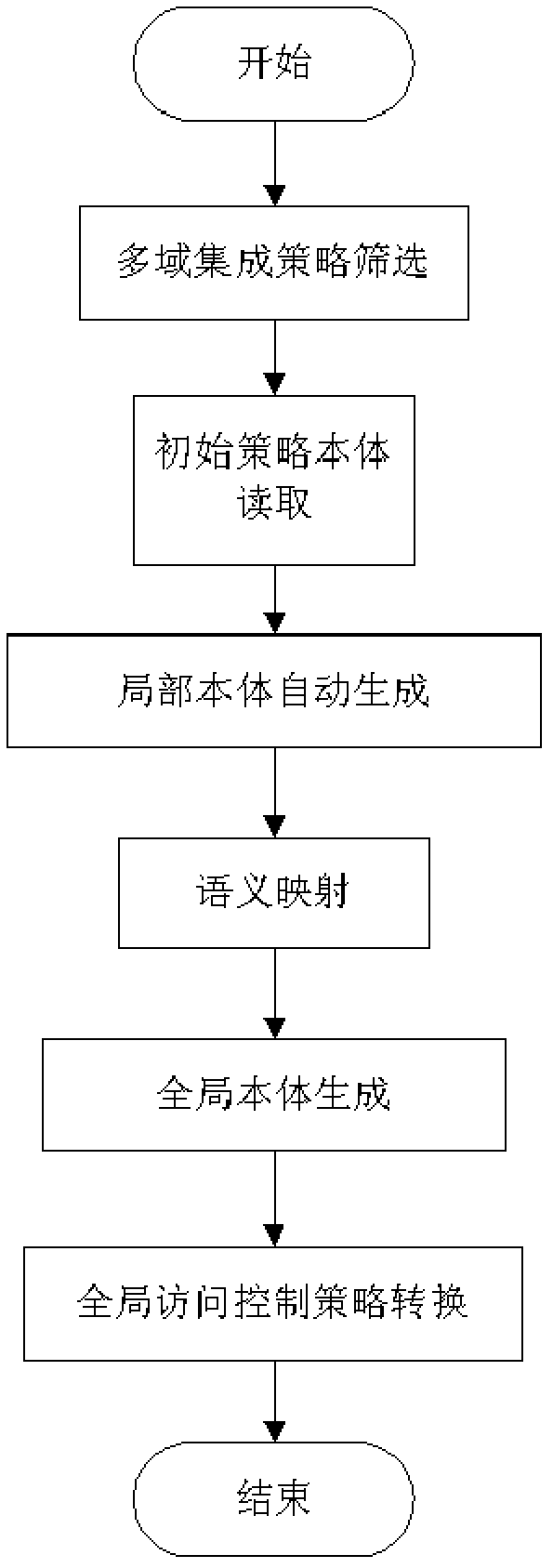
[0037] Such as figure 1 As shown, the access control policy conflict detection system in the collaborative environment of the present invention is composed of an access control policy preprocessing module, a multi-domain policy integration module and a policy conflict detection module.
[0038] The whole implementation process is as follows:
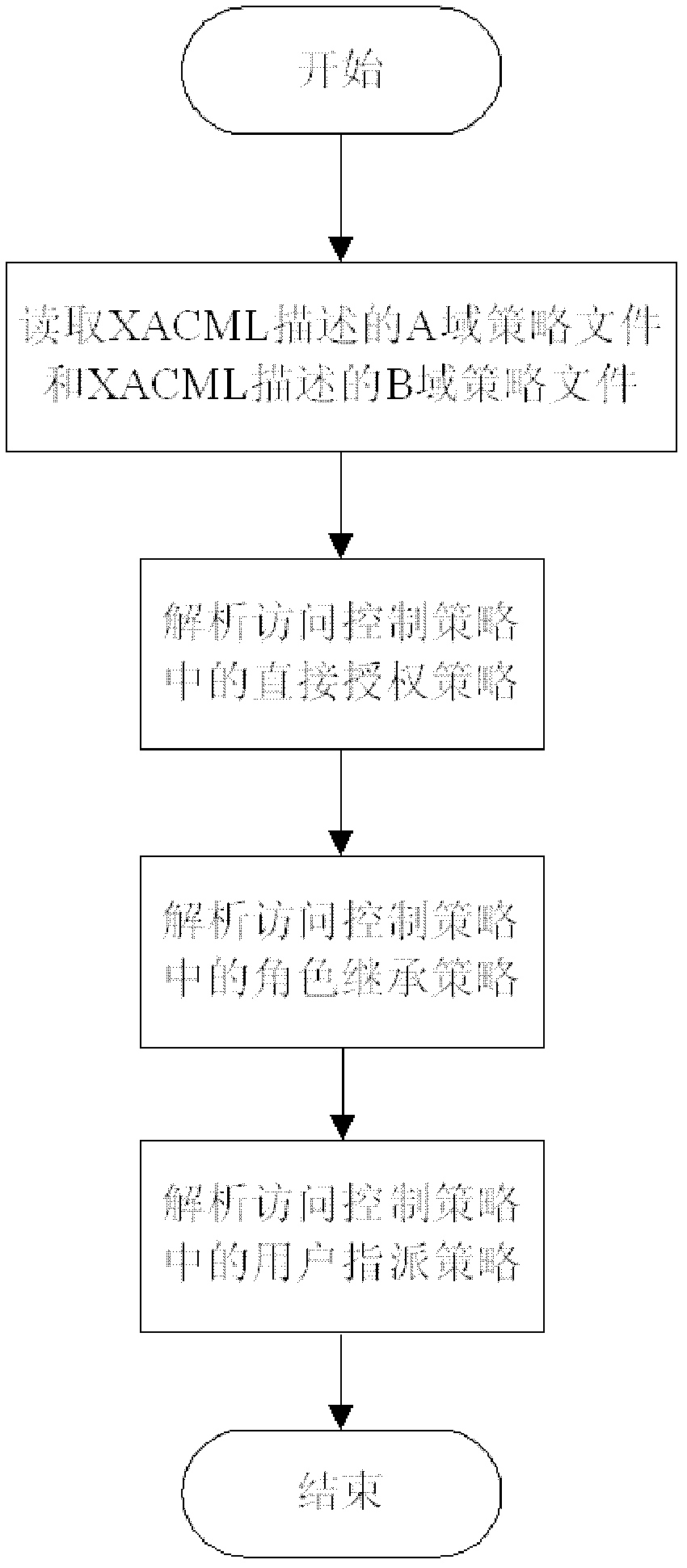
[0039]Access control policy preprocessing module: use the policy files of the two domains described by XACML, that is, the access control policies in the A domain policy file described by XACML and the B domain policy file described by XACML to perform syntax and semantic analysis. While parsing, add a serial number to each access control strategy as the unique identifier of the access control strategy, form an ordered set of access control strategies after parsing, and send the ordered set of access control strategies to the multi-domain policy integration module; The domain is the basic unit of the collaborative environment, that is, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com