Third-party authentication security protection system and third-party authentication security protection method based on online security protection of electronic evidence
An electronic evidence, third-party technology, used in transmission systems, electrical components, user identity/authority verification, etc. , it is impossible to ensure the objectivity and authenticity of electronic evidence, etc., to achieve the effect of ensuring continuous security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
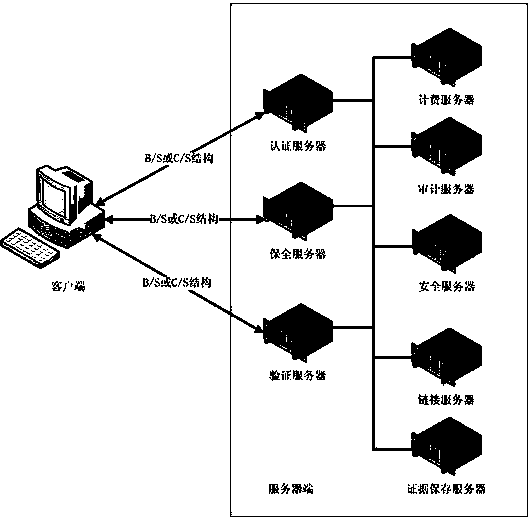
[0027] figure 1 Provided is the third-party authentication preservation system based on electronic evidence online preservation according to the present invention, from figure 1 It can be seen that the system is divided into client and server, and the client communicates with the server through the Internet.
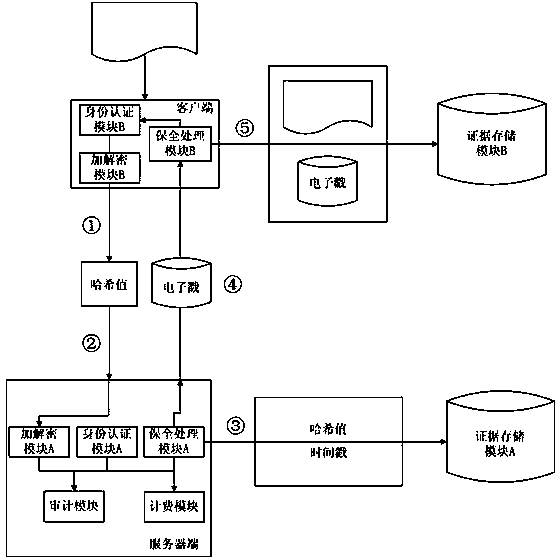
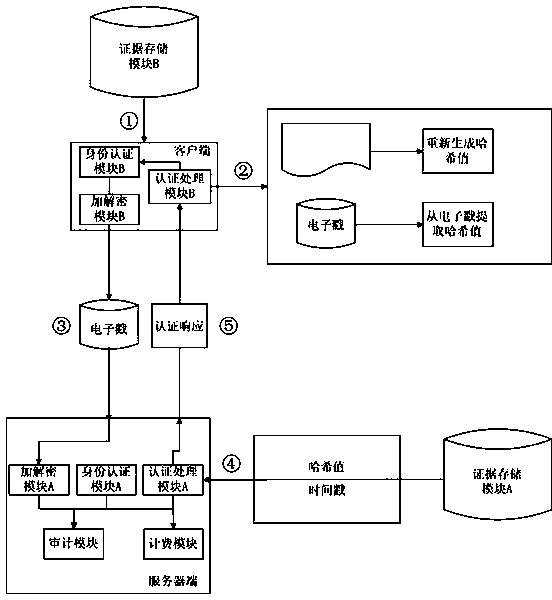
[0028] The client terminal of the present invention includes: an identity authentication module B, an encryption and decryption module B, a security processing module B, an evidence storage module B, and an authentication module B. All modules of the client are integrated and installed in such as figure 1 on the client computer shown, where:
[0029] The identity authentication module B generates an identifier that uniquely identifies the user according to the user name / password, digital certificate, biometric feature, etc. When the user logs in, the identity authentication module B initiates an identity authentication request to the server according to the identifier;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com