Method for detecting Trojan quickly based on heartbeat behavior analysis
A detection method and behavior analysis technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problem that small data packets cannot be effectively detected, and achieve high session reorganization efficiency and improved storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
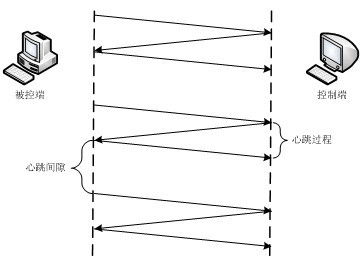
[0060] Embodiment one: the fast Trojan detection method based on heartbeat behavior analysis is:
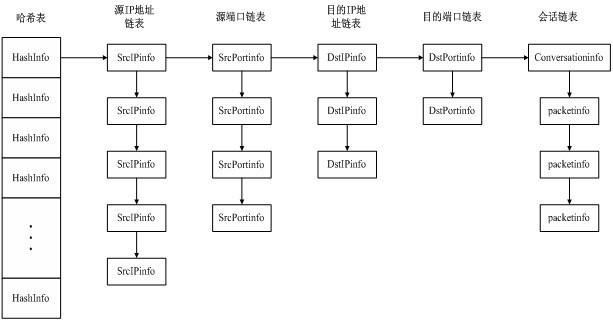
[0061] Organize the captured network data according to network sessions: use the IP address and port of the monitoring object as the source IP address and source port. The data packet is divided into sessions according to the equivalent quadruple, that is, each session is uniquely identified by the equivalent quadruple (at this time, each session linked list contains a bidirectional data flow), and the session linked list is selected as the data structure for storing the session. The reason for choosing the session linked list as the data structure for recording the session is: since the network communication is a dynamic process, the data packets in the session will continue to increase as the communication progresses, and the data structure used to save the session will also change dynamically accordingly. . In the process of building the session linked list, it is necessary t...
Embodiment 2
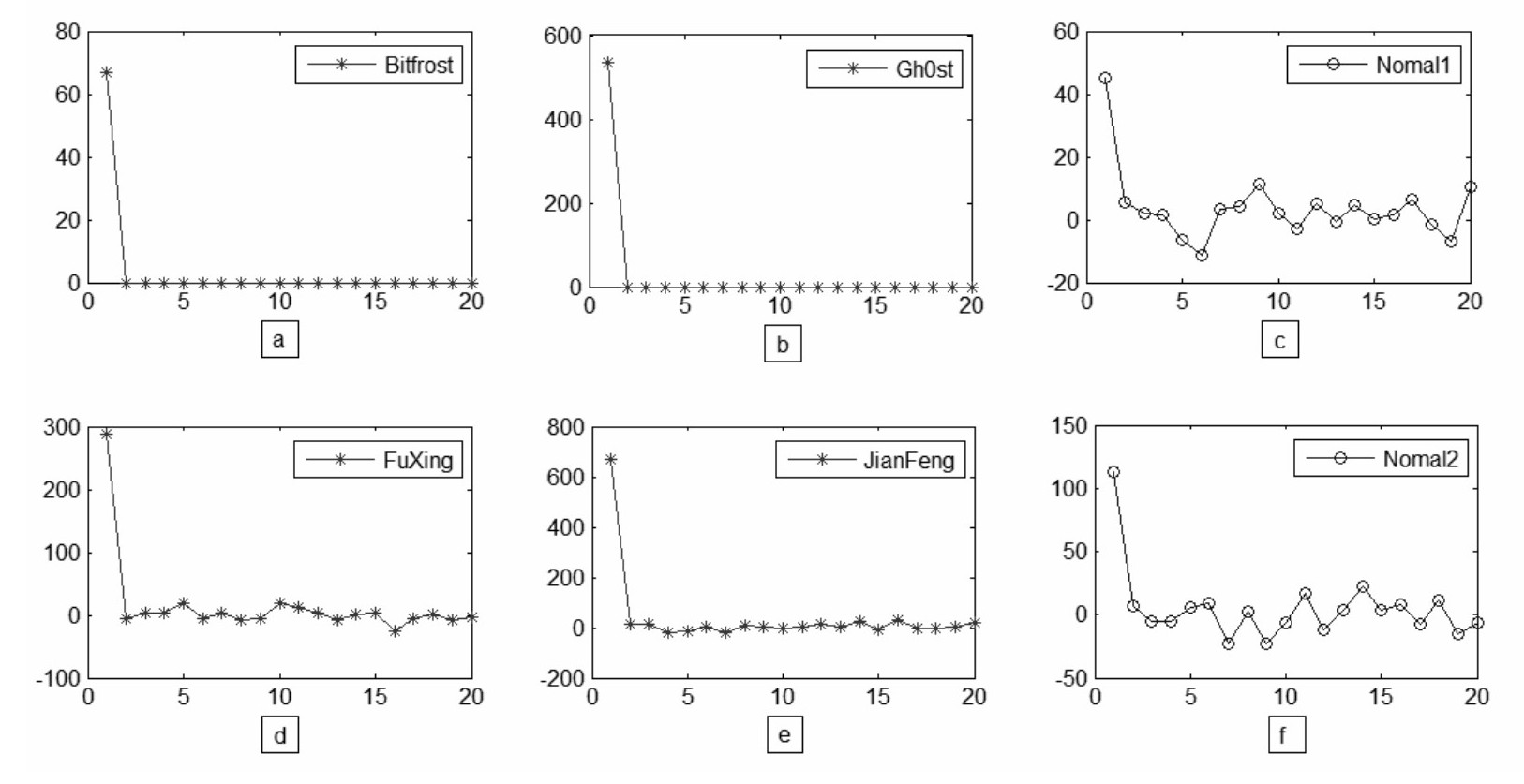
[0092] Embodiment 2: The similarities between this embodiment and Embodiment 1 will not be repeated, and the difference is: due to the high computational complexity of DFT transform, it can also be based on the essential construction of the secondary haar wavelet decomposition with relatively low computational complexity. Low statistics to detect Trojan heartbeat behavior. Still remember that X represents the time interval sampling set of unidirectional data flow packets, so that is the transformed feature vector. Pick
[0093] t i = x i - x i - 1 2 ;
[0094] w i = t i - t i ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com