Authentication system realizing method supporting exclusive control of digital signature key
A digital signature and authentication system technology, applied in the field of information security, can solve problems such as not being able to meet the digital signature key, and achieve the effects of simple scheme, wide application range, and convenient operation and use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to make the objectives, technical solutions, and advantages of the present invention clearer, the following further describes the present invention in detail with reference to the accompanying drawings and embodiments.
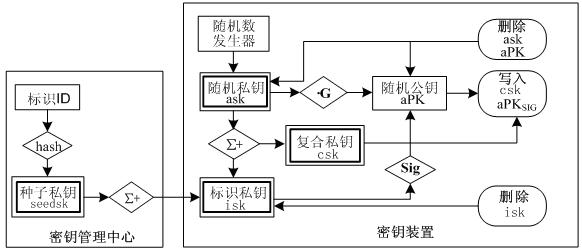
[0041] 1. Construct seed key and seed public key set
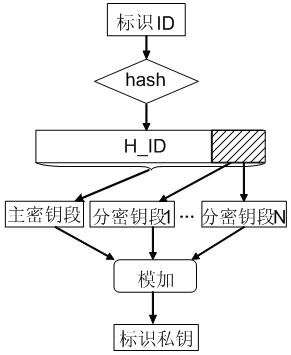
[0042] The seed key is the calculation base used by the CPK system to calculate the identification key. It is composed of the seed public key seedPK and the seed private key seedsk. The seed private key seedsk is secretly kept by the key management center KMC and used to generate the user identification private key isk: The seed public key seedPK can be made public and is used to calculate the user's identification public key iPK.
[0043] The seed public key set referred to in the present invention is composed of a set of two seed public keys, one of which is used to calculate the digital signature public key cPK, and the other is used to calculate the identification public key for key exchange. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com