Method for anonymous communication as well as registering method and access node adopted in same
A technology for accessing nodes and anonymous communication, which is applied in the field of communication and can solve problems such as the inability to determine the location identification of communication nodes and the inability to establish communication node connections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0085] figure 2 The overall implementation process of the method for realizing anonymous communication is shown, including:
[0086] 201: After the terminal applies for opening the anonymous communication service, save the information that the terminal has opened the anonymous communication service in the user attribute of the terminal in the authentication center, assuming that the access identifier of the terminal is AIDm, then use the AIDm to identify the user attribute of the terminal;
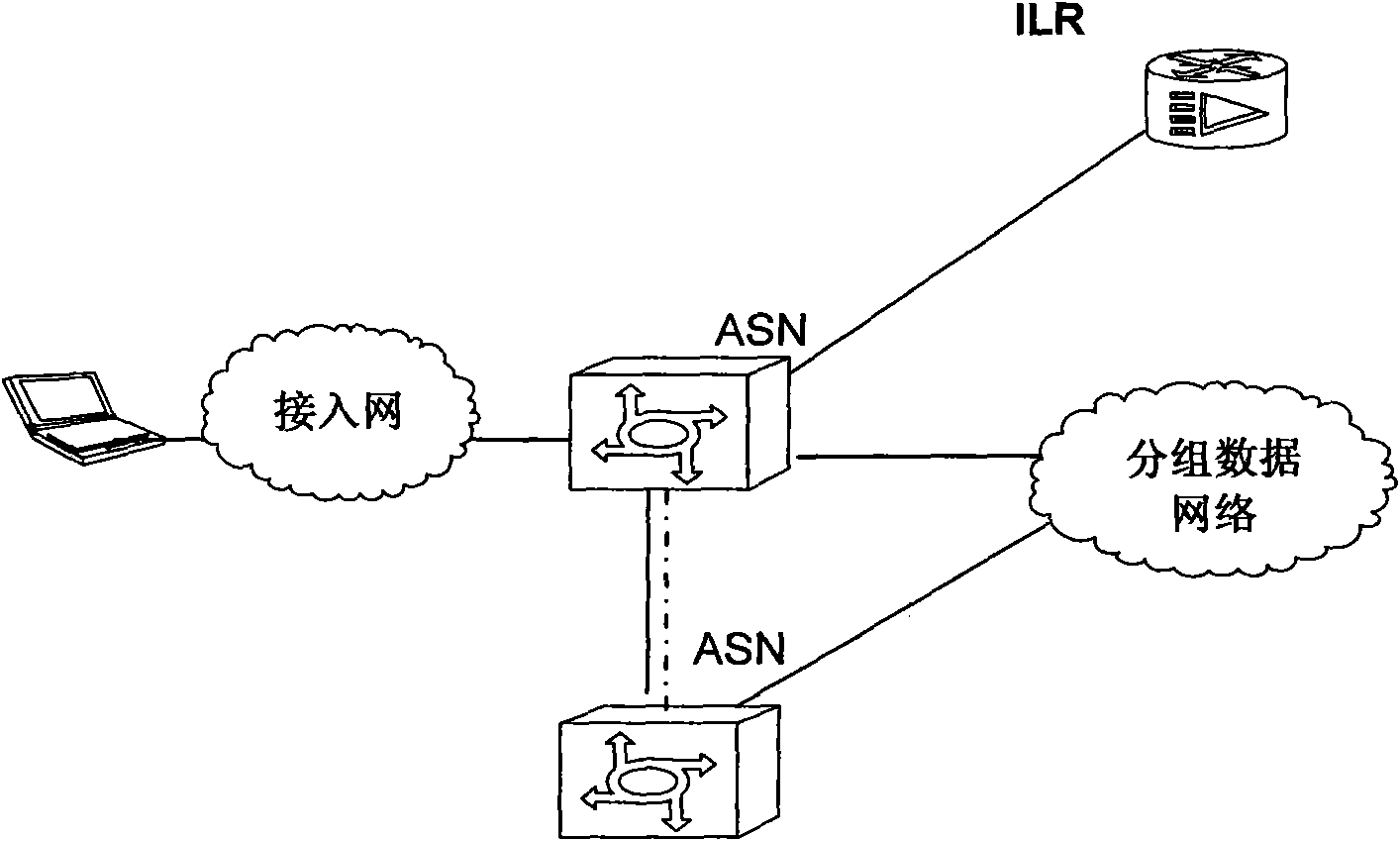
[0087] 202: The terminal accesses the network, and the accessed ASN (ASNm) allocates a RID (RIDm) for it, and the ASNm registers the mapping information with the ILR (ILRm) where the terminal belongs, and the ILRm stores the AIDm-RIDm mapping information of the terminal;
[0088] 203: The terminal applies for anonymous communication;
[0089] 204: The terminal initiates end-to-end anonymous communication with the communication peer;
[0090] 205: The terminal cancels the anonymous communi...
Embodiment 2
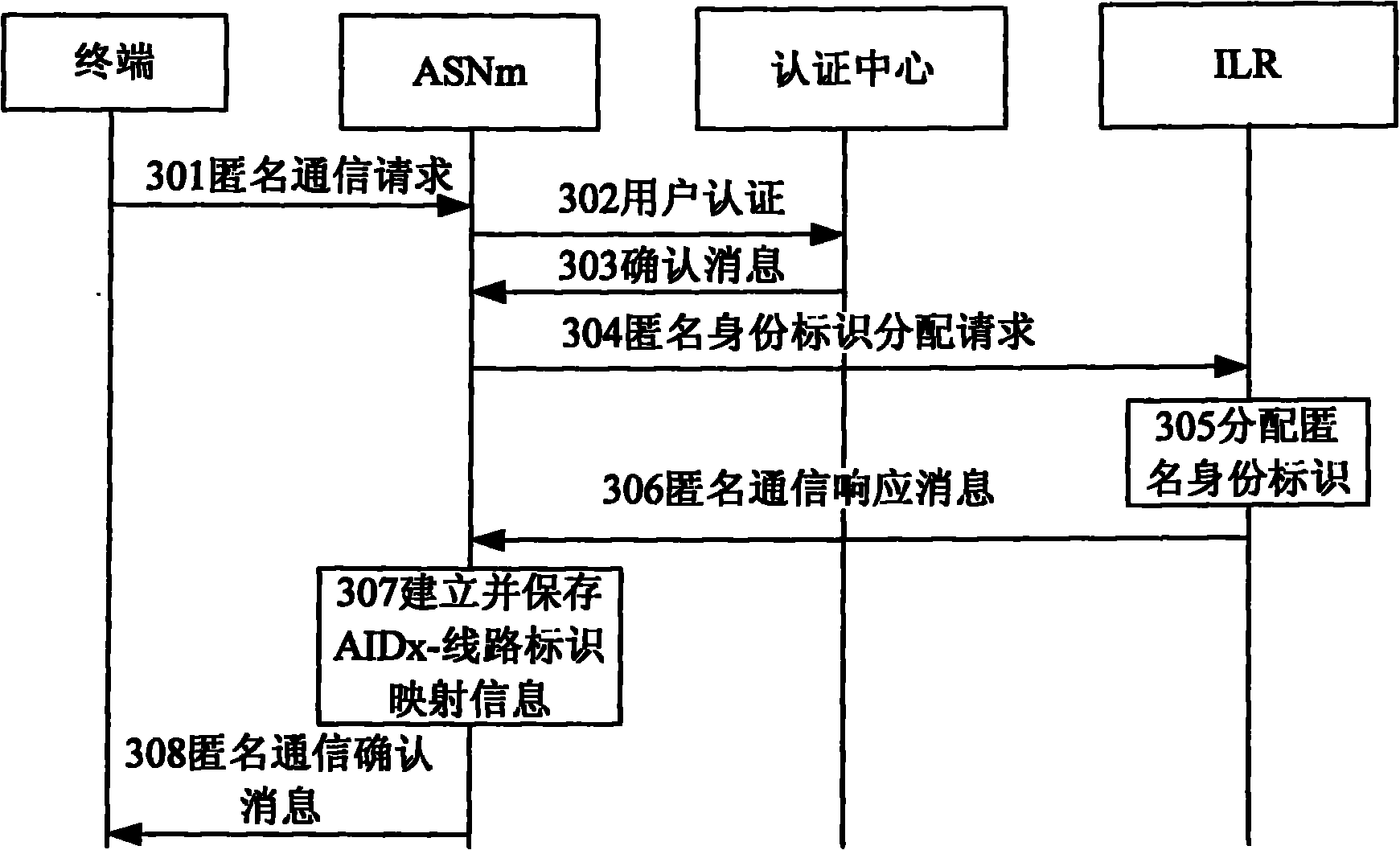
[0092] image 3 Shown is a detailed description of the above step 203, which step includes:
[0093] 301: The terminal sends an anonymous communication request to ASNm, and the request carries the identity identifier AIDm;
[0094] 302: ASNm confirms to the authentication center whether the terminal has the authority for anonymous communication services;
[0095] 303: The authentication center queries the user attributes of the terminal, and if the terminal has the authority for anonymous communication services, sends a confirmation message to ASNm;
[0096] The steps 302-303 are optional steps according to operational needs.
[0097] 304: After receiving the confirmation message, ASNm sends an anonymous identity identifier allocation request to ILRm;
[0098] 305: After ILRm receives the anonymous identity allocation request from ASNm, it allocates an anonymous identity for the terminal, saves the terminal's anonymous identity in the terminal's record, and can add AIDx to ...
Embodiment 3
[0105] Figure 4 Shown is the equivalent alternative of the above-mentioned embodiment 2, the difference is that the following method uses ASN to complete the distribution process of the anonymous identity identifier AIDx, including:
[0106] 401: After receiving the confirmation message from the authentication center, ASNm assigns AIDx to the terminal, and binds the terminal's AIDx with the terminal's line ID to form AIDx-line ID mapping information, which is stored in the terminal's data area and records that the terminal is anonymous communication status;
[0107] 402: ASNm initiates the AIDm-AIDx registration process to ILRm, and ILRm adds AIDx to the AIDm-RIDm mapping information of the terminal saved locally to save the AIDm-AIDx-RIDm mapping information, or saves the AIDm-AIDx mapping information separately;
[0108] 403: The ASNm sends an anonymous communication confirmation message to the terminal, carrying the anonymous identity identifier AIDx assigned to the termi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com