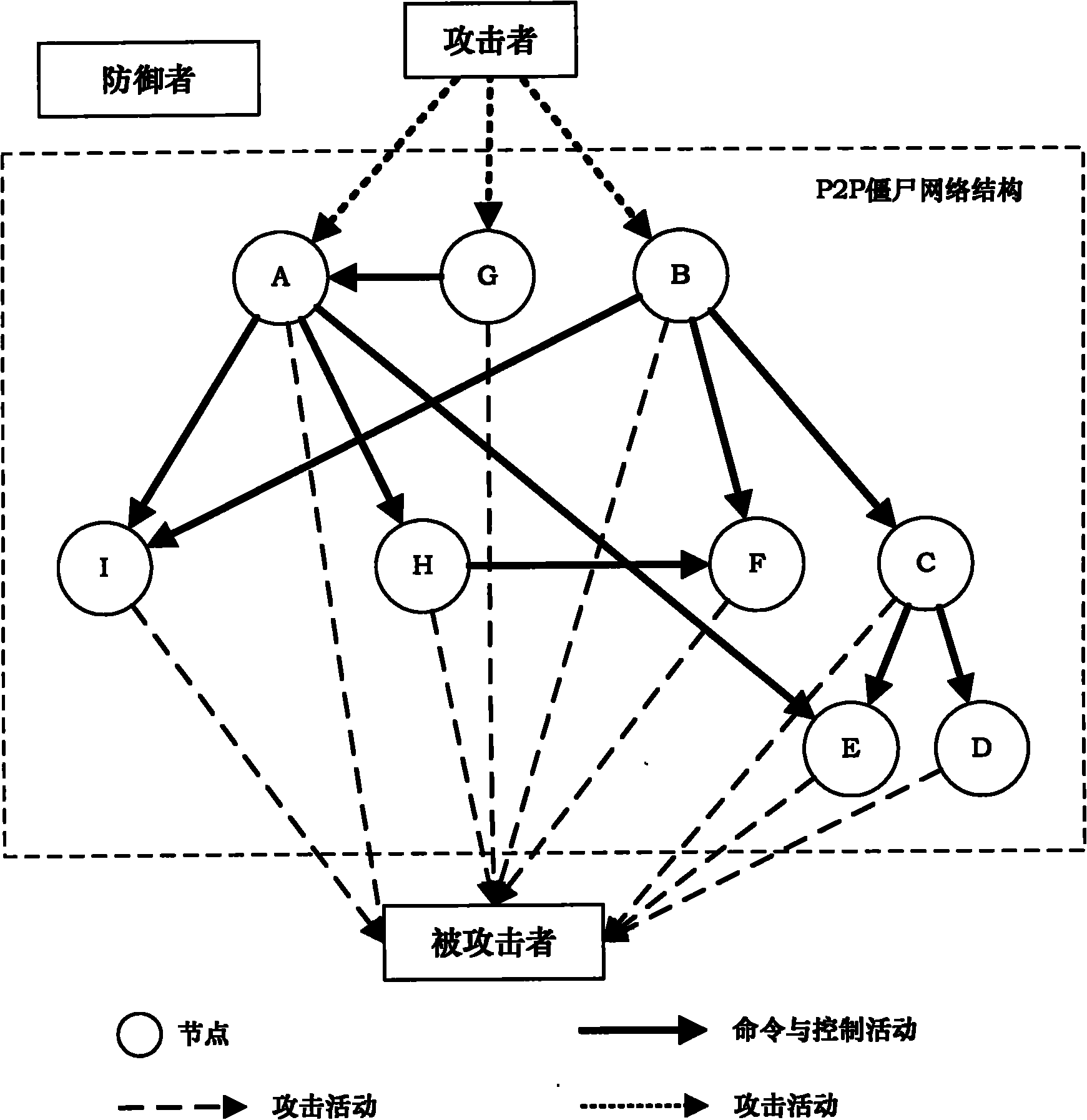
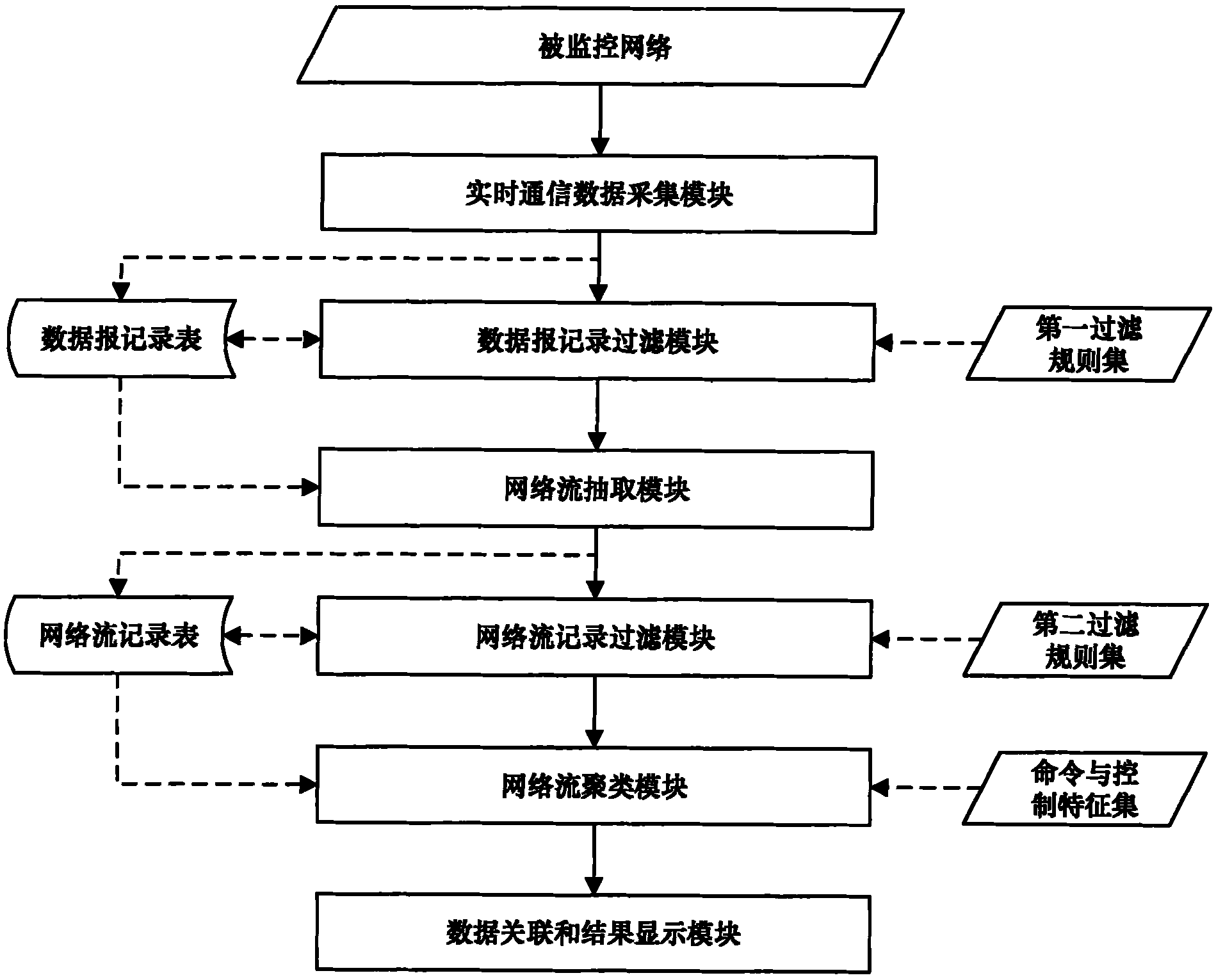
Method for detecting P2P botnet structure based on network flow clustering
A network structure and network flow technology, applied in the field of P2P botnet structure detection based on network flow clustering, can solve the problems that P2P botnets are not easy to detect and discover
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0023] A kind of method of detecting P2P botnet structure based on network flow clustering of the present invention, this method comprises following detection steps:
[0024] Step 1: Collect real-time communication data
[0025] The first aspect of the real-time communication data acquisition module obtains the IP datagram IPD of the monitored network from the monitored network, and extracts the key field KF from the IP datagram IPD;
[0026] The key field KF includes source IP address SIP, destination IP address DIP, source port number SPT, destination port number DPT, IP header length IHL, IP datagram total length ITL, TCP / UDP header length THL , IP datagram protocol field type PTL; according to the set expression form in mathematics, it is KF={SIP, DIP, SPT, DPT, IHL, ITL, THL, PTL}.
[0027] In the present invention, when the PTL is the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com