Key management method for integrated avionic system
An avionics system and key management technology, applied in the field of integrated avionics system key management, can solve the problems of lack of key management methods, inefficiency, etc., and achieve a safe and effective distributed key management method, high efficiency, high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
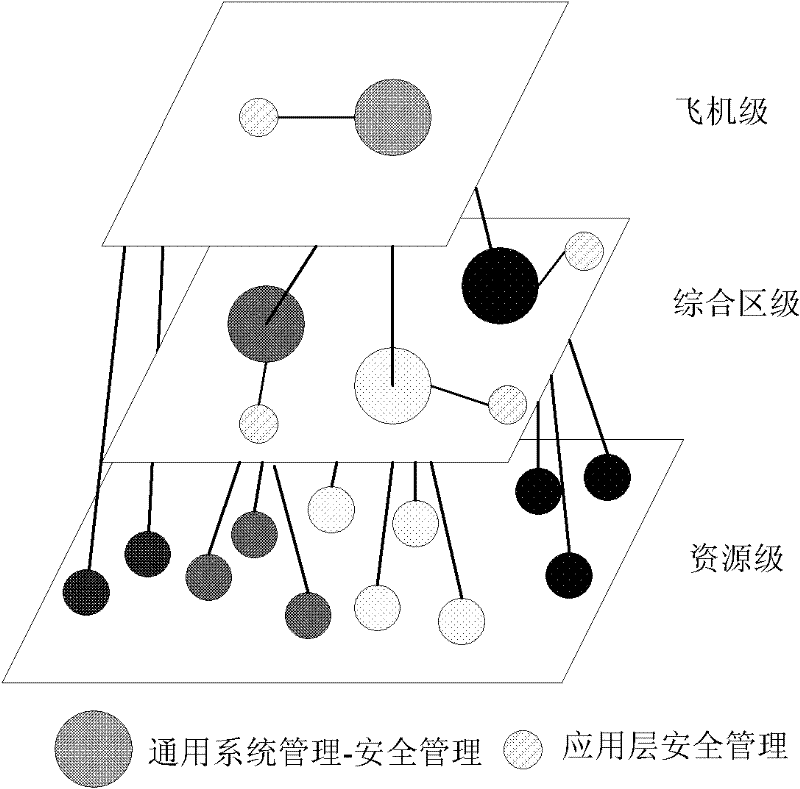
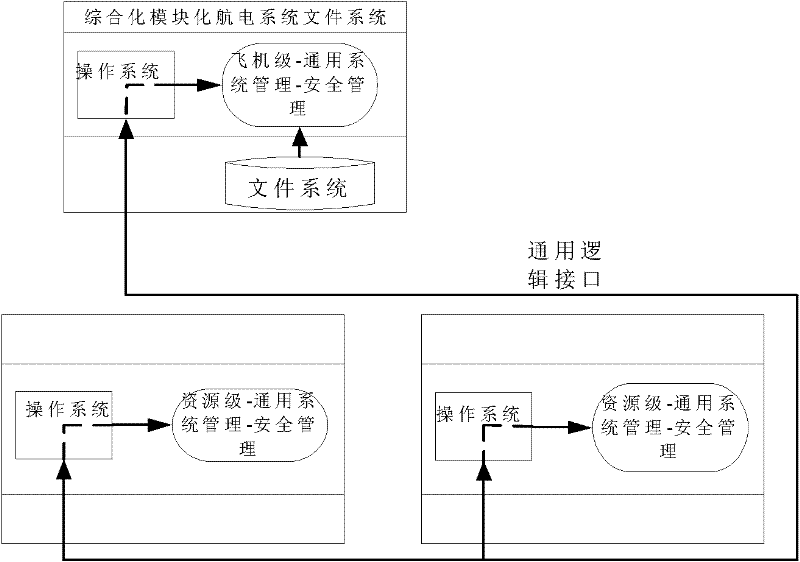
[0046] Key management deals with issues related to the entire process from key generation to final destruction, including key generation, storage, loading, distribution, and use. Key management is implemented as a functional component of the general system management security management GSM-SM in the integrated modular avionics system IMA, and it manages all keys in the system uniformly. The integrated avionics system key management method includes the following steps:
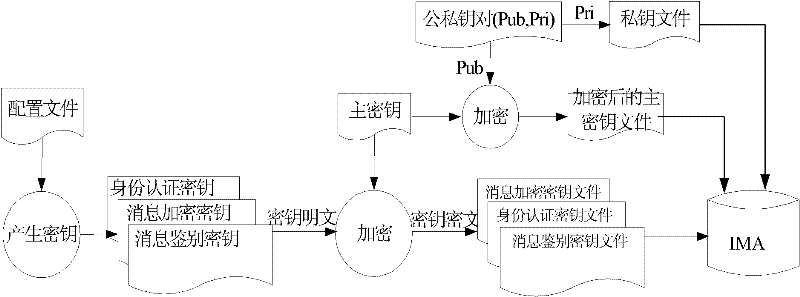
[0047] Such as figure 2 As shown, it is the flow chart of key production and key transmission,
[0048] 1] Key generation:
[0049] 1.1] Generate the keys required for system operation on the PC in advance, the keys include master key MEK, message encryption / decryption key, public-private key pair key, identity authentication key and message authentication key; The public-private key pair keys include public key Pub and private key Pri;
[0050] The specific generation is as follows:
[0051] In the earl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com