Safe wireless access method and safe wireless access device
A wireless access and wireless access point technology, applied in security devices, wireless communications, electrical components, etc., can solve problems such as loss, cracking, and password leakage, and achieve the effect of facilitating the access process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
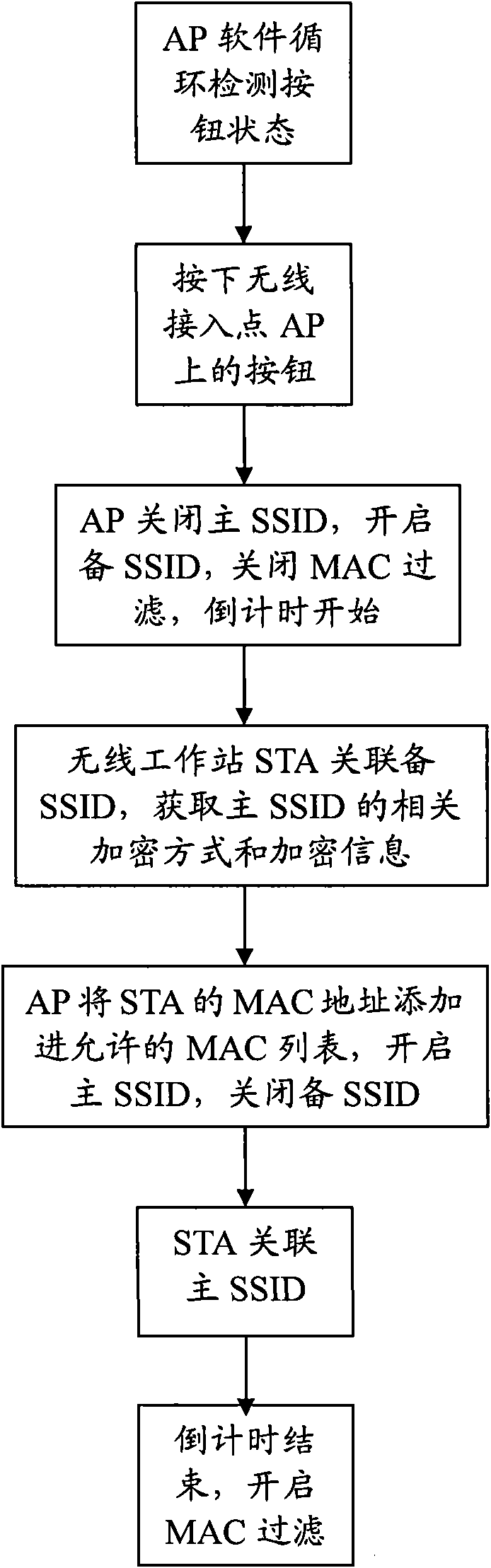
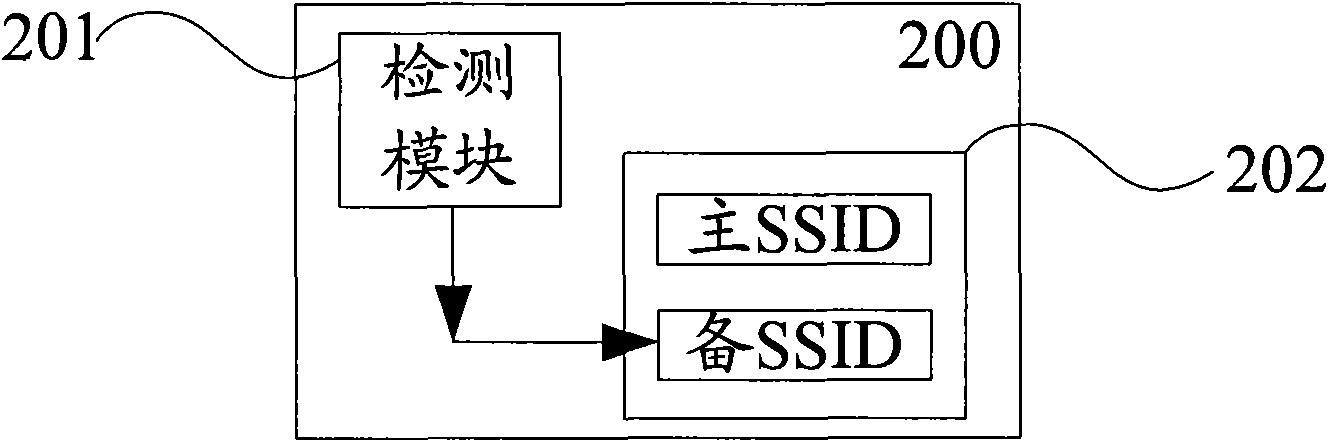
[0020] The wireless access point AP (Access Point) detects whether the hardware button is pressed at any time. Once the user presses the hardware button, after the software detects the action, the wireless access point AP (Access Point) starts immediately and starts for a fixed time. Countdown (for example, within two minutes after pressing the button), before the countdown ends, the wireless access point AP (AccessPoint) allows the wireless station STA (Station) to access, after the fixed time ends, the software rejects the wireless station STA (Station) Access, even if you have the corre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com