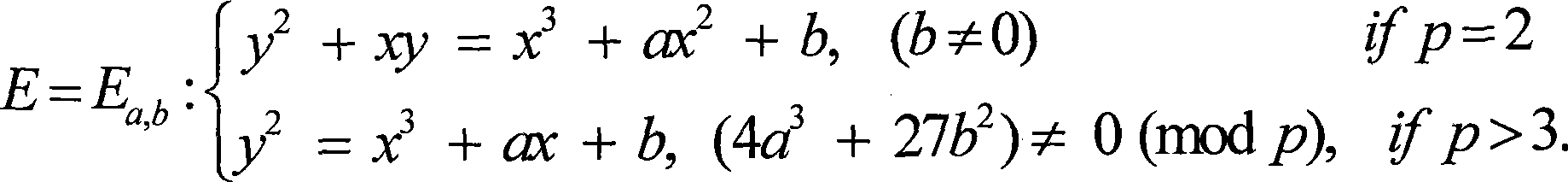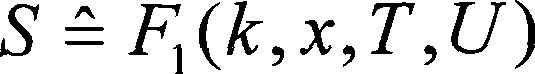Security protection method for electric document digital signing based on elliptical curve
An elliptic curve and digital signature technology, applied in the field of information security, can solve the problems of integrity verification document authenticity, signature non-repudiation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0078] The signer first selects and publishes the mapping function η in the signature algorithm 0 (T, U) = 1, η 1 (T, U) = T+U, η 2 (T, U) = TU, η 3 (T, U) = T ∨ U, η 4 ( T , U ) = T ⊕ U , n 5 (T, U) = T∧U, η 6 (T, U)=T+U, π(R)=R; in this way, a specific signature algorithm is formulated.
[0079] Signature algorithm:
[0080] In order to sign the electronic document M, the signer randomly selects an integer k in the interval [1, q-1],
[0081] Calculate the point R on the elliptic curve = (x 1 , Y 1 )=kG, calculate T=π(R)=R;
[0082] Calculate the Hash value U=H(M) of the message;
[0083] Then the signature of the message M is (T, S), where
[0084] S = ^ [ kη ...
Embodiment 2
[0095] The signer first selects and publishes the mapping function η in the signature algorithm 0 (T, U) = 1, η 1 (T, U) = T, η 2 (T, U) = T-U, η 3 (T, U) = U, η 4 (T, U) = T+U, η 5 (T, U) = 0, η 6 (T, U)=T-2U, π(R)=R; in this way, a signature algorithm is specifically determined.
[0096] In order to sign the electronic document M, the signer randomly selects an integer k in the interval [1, q-1],
[0097] Calculate the point R on the elliptic curve = (x 1 , Y 1 )=kG, calculate T=π(R)=R;
[0098] Calculate the Hash value U=H(M) of the message; then the signature of the message M is (T, S), where
[0099] S = ^ [ kη 4 ( T , U ) + ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com