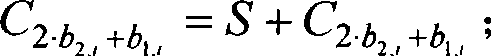Dot computation method capable of resisting simple current drain aggression
A calculation method and simple technology, applied in the field of secure execution of public key cryptography, can solve the problems of sacrificing efficiency and not being able to resist SPA attacks well, and achieve the effect of good security and calculation speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
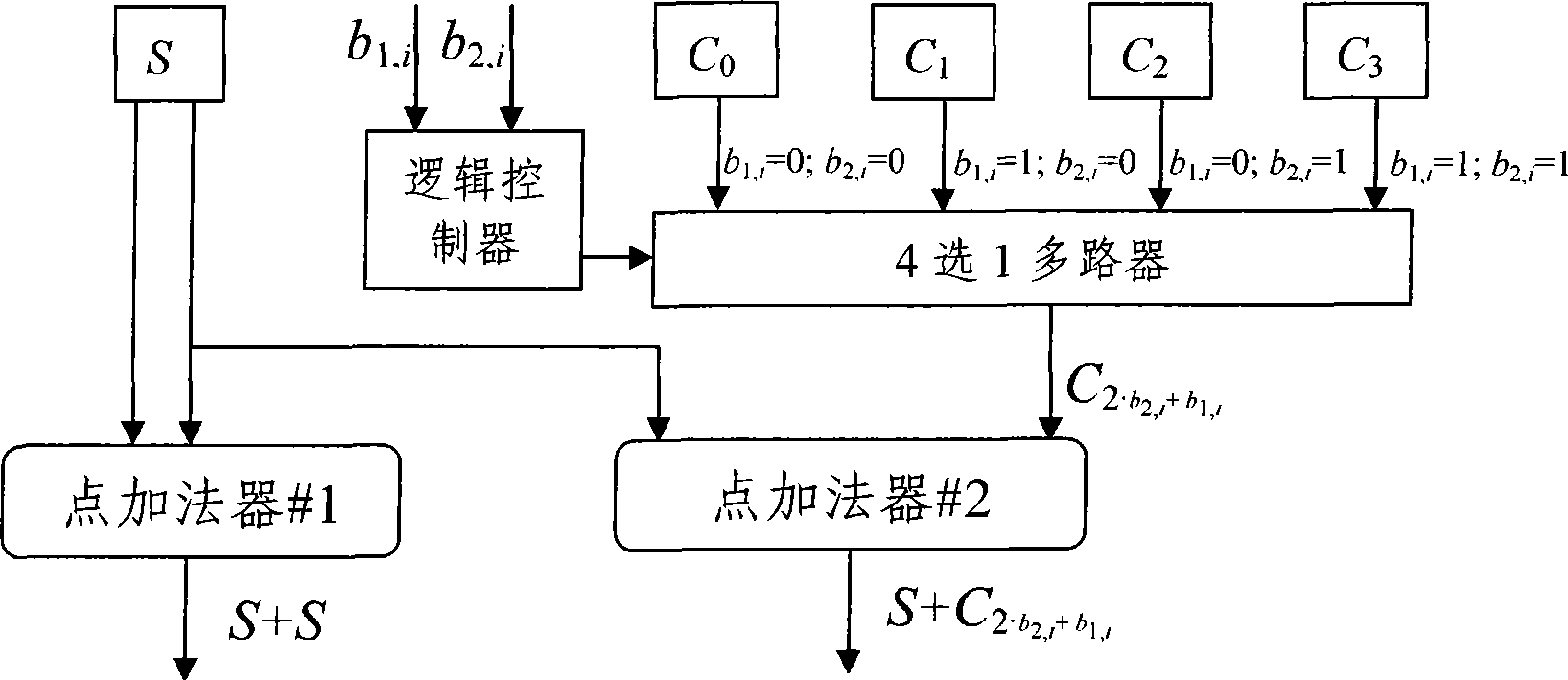
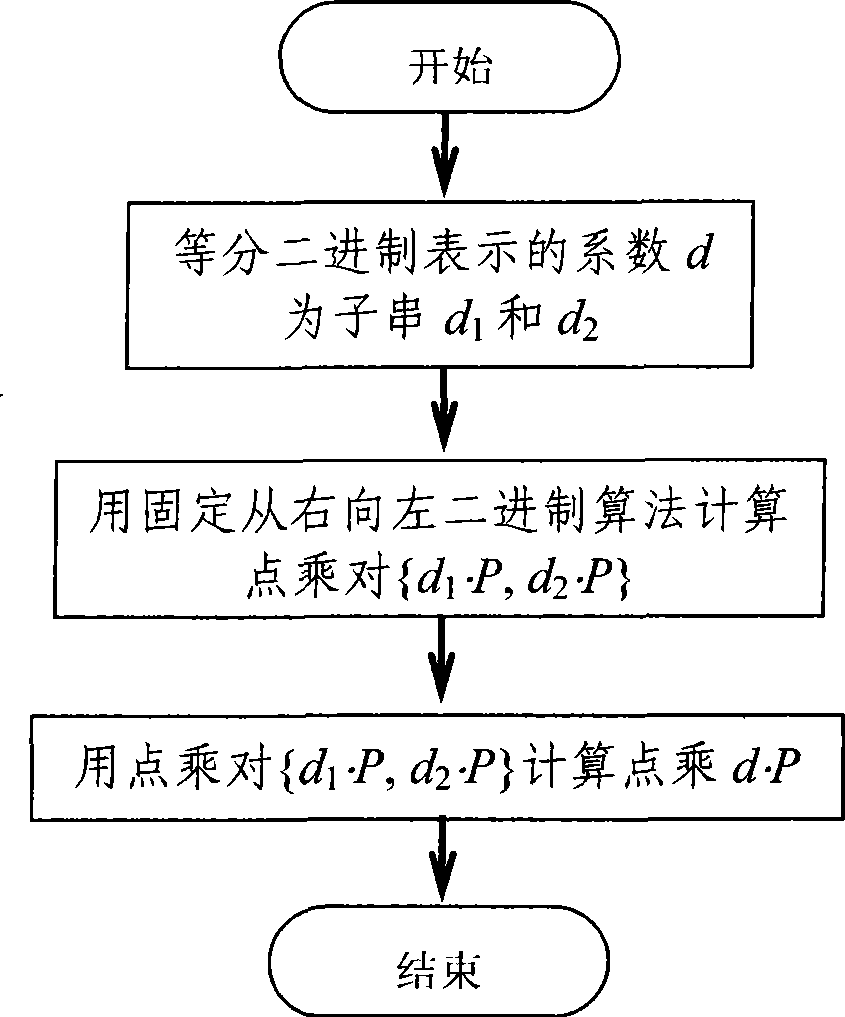
[0027] Before further describing the technical solution of the present invention, the symbols used in the present invention will be described first.
[0028] B 1 AND B 2 Represents the binary string B of equal length 1 and B 2 Logical AND operation is performed on a bit basis, for example, 01011011AND11001101=01001001.
[0029] NOT B means to perform a bitwise logical NOT operation on the binary string B, for example, NOT10101101=01010010.
[0030] B 1 ‖B 2 Represents the binary string B 1 and B 2 Perform connection operation, for example, 01011011∥11001101=0101101111001101.
[0031] P 1 +P 2 Denotes the point P on the elliptic curve point group 1 and P 2 Perform point addition operation, in special cases when P 1 =P 2 , it is point doubling operation, that is, 2·P 1 .
[0032] sq (m) (P) means to do m times of doubling operations on the point P on the elliptic curve point group, for example, sq (3) (P)=2·(2·(2·P))=2 3 ·P.
[0033] represents the smalles...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com