Detection defense method for distributed reject service and network appliance
A distributed denial and service detection technology, applied in data exchange networks, error prevention, digital transmission systems, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
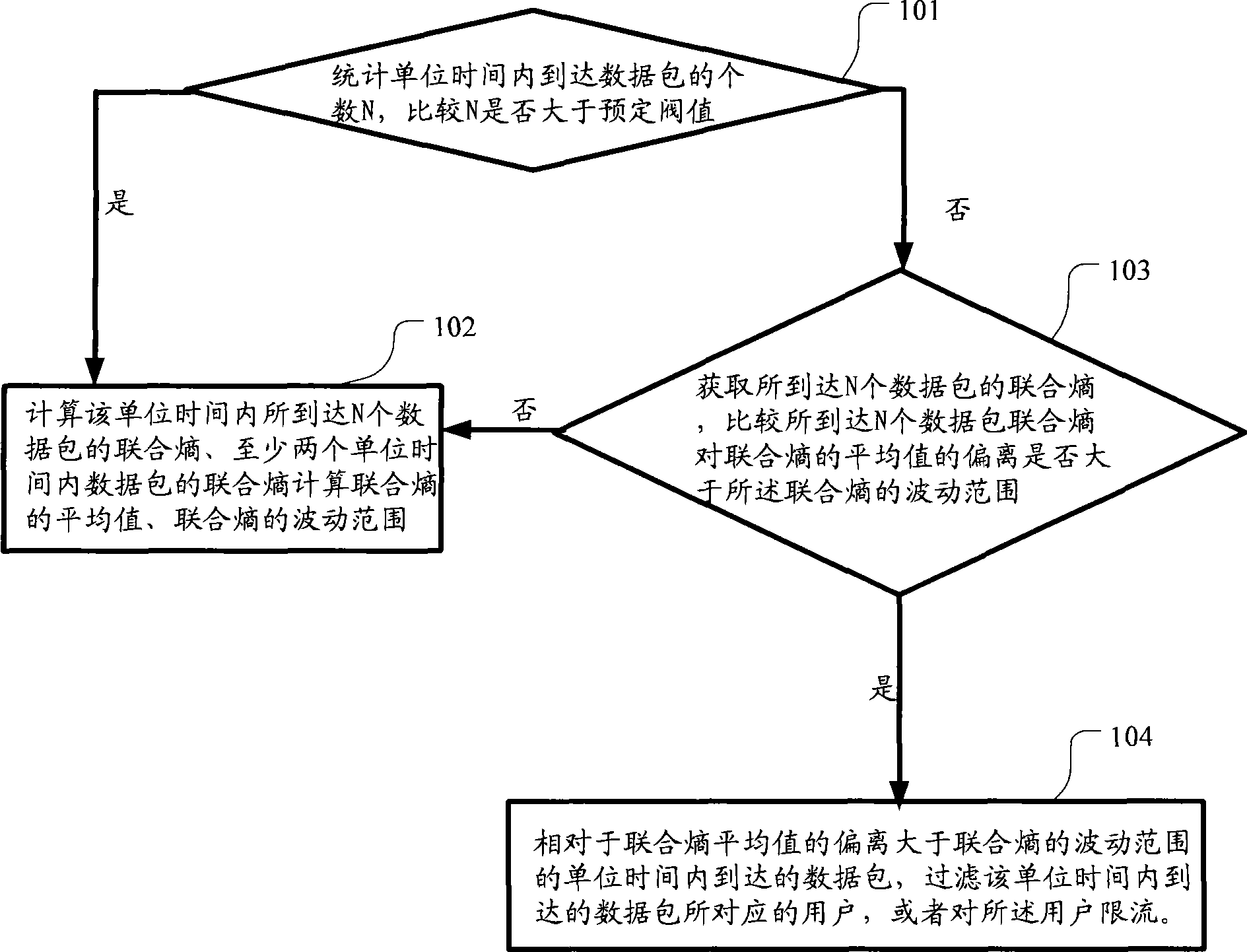
[0047] Embodiment 2, counting the number N of arriving data packets per unit time, and comparing the number N of arriving data packets per unit time with the preset threshold Then collect the source IP address of data packet, the number of hops of data packet, the size of data packet, calculate the joint entropy of these N data packets according to the size of source IP address, the number of hops of data packet, data packet, this moment joint Entropy is: H ( X , Y , Z ) = - Σ i = 1 n P ( x i , y i , z i ) log P ( ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com