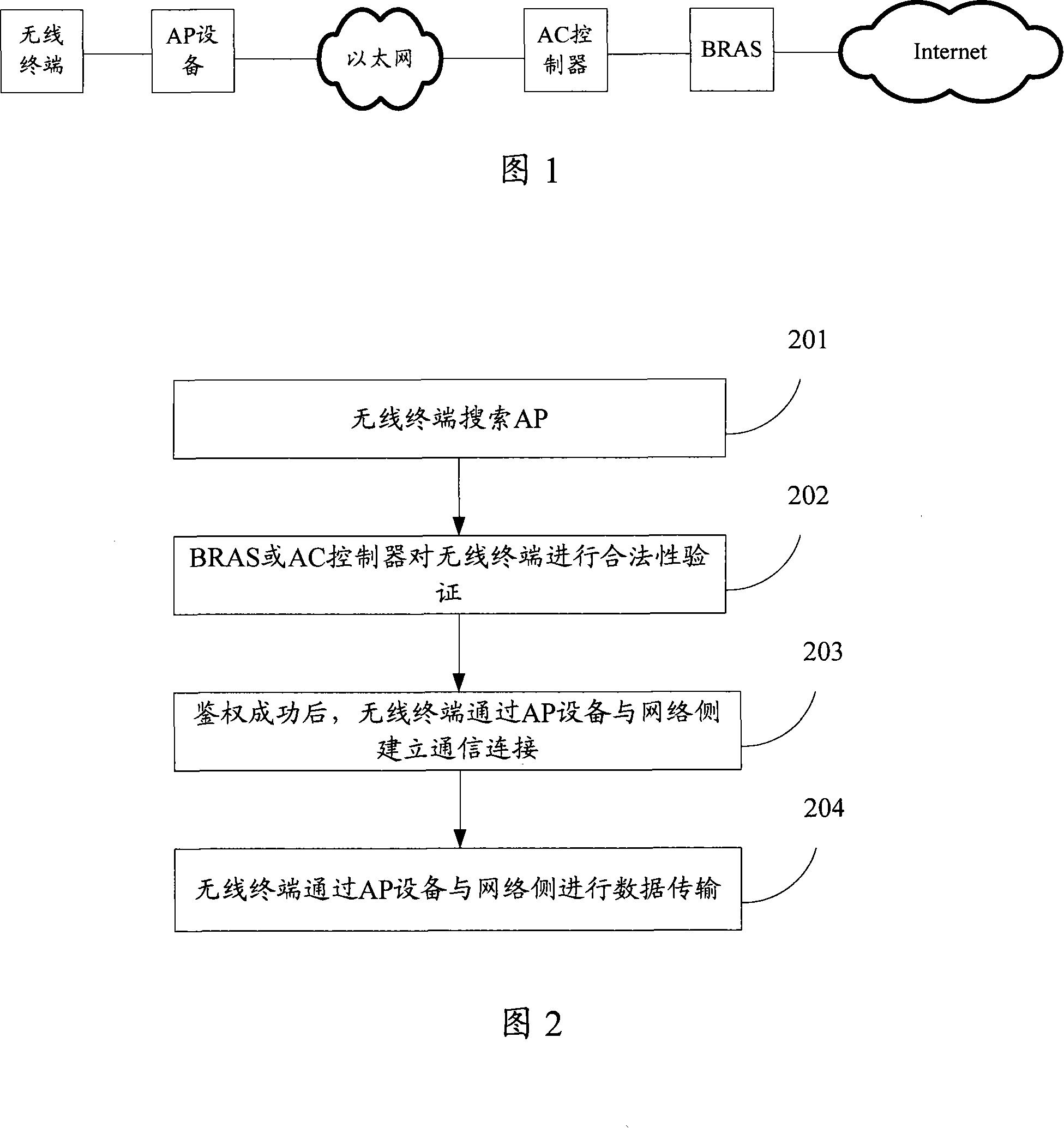
Method and device of access point equipment for preventing error access
A wrong access and access point technology, which is applied in the direction of data exchange through path configuration, user identity/authority verification, etc., can solve the problems that other users' keys cannot be kept secret, and wireless terminals access WLAN, which is inconvenient. Achieve the effect of reducing the risk of user complaints, reducing the number of connection failures, and reducing the impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] In this embodiment, the AP device hides the SSID in the Beacon frame broadcast to each wireless terminal, and the wireless terminal searches for the SSID through a Probe Request method.
[0057] Referring to Fig. 3, it is a flowchart of Embodiment 1, including:
[0058] Step 301: the wireless terminal sends a Probe Request to request a ProbeResponse including SSID, etc.;
[0059] Step 302: the AP device responds to the Probe Request of the wireless terminal, and feeds back a ProbeResponse including the SSID;
[0060] Wherein, the Probe Response includes the basic information of the BSS to which the AP belongs and the basic capability level of the AP.
[0061] In practical applications, due to the strength of the signal, it is likely that the neighbor AP also feeds back the Probe Response to the wireless terminal, and the feedback signal is stronger, causing the wireless terminal to mistakenly connect to the AP device.
[0062] Step 303: the wireless terminal requests ...
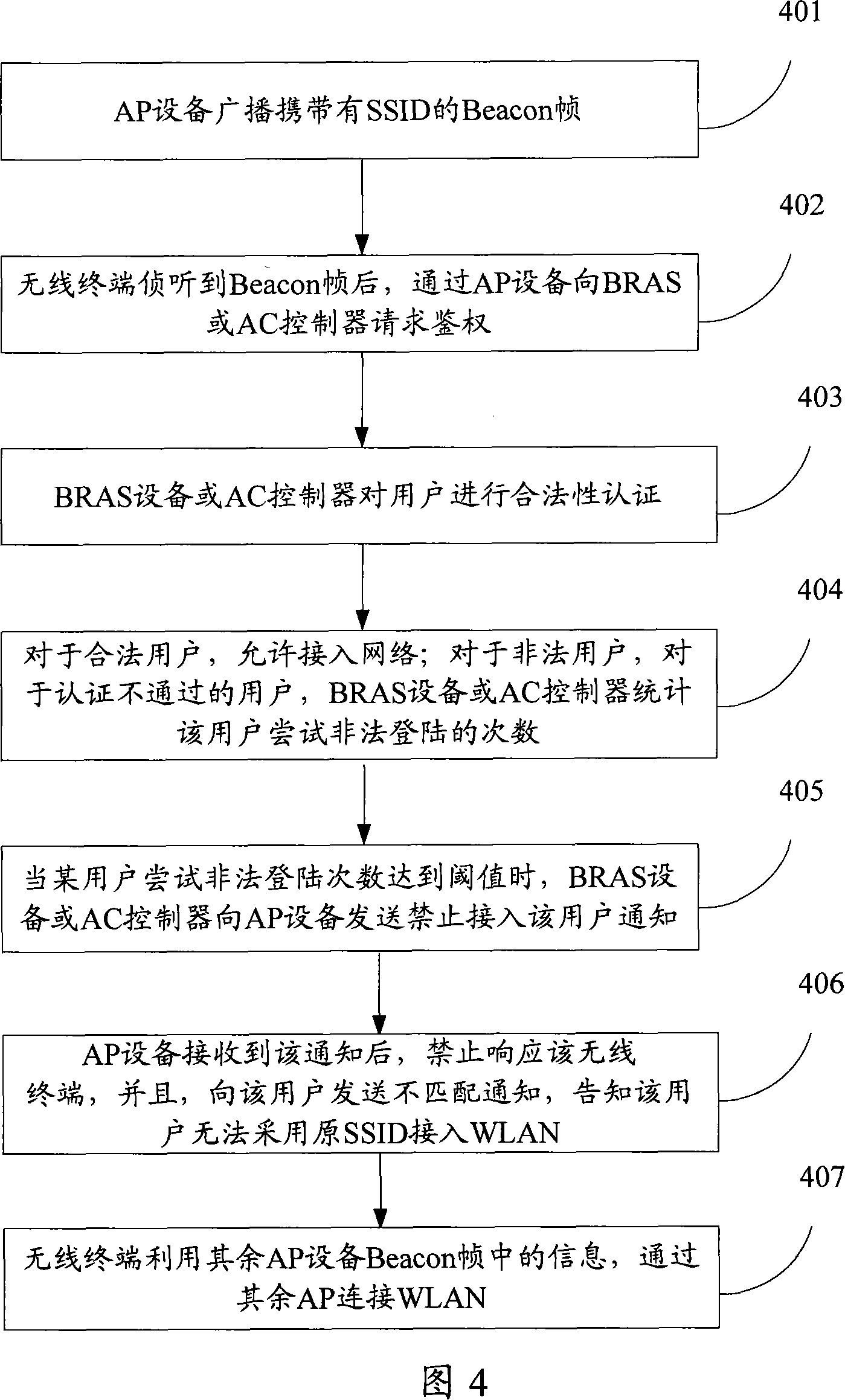
Embodiment 2
[0071] Different from the hidden SSID in the Beacon frame in Embodiment 1, the Beacon frame in this embodiment carries the SSID, and the wireless terminal obtains information such as the SSID by listening to the Beacon frame broadcast by the AP device. When the AP device receives a certain wireless When the terminal prohibits access notification, send a mismatch notification to the wireless terminal, informing the wireless terminal that the SSID used does not match and cannot log in to the network successfully, so that the user can use other SSID to access the WLAN, and also avoid the user's complaint without knowing it.
[0072] Referring to Fig. 4, it is a flow chart of embodiment two, including:
[0073] Step 401: The AP device broadcasts the Beacon frame carrying the SSID;
[0074] Step 402: After the wireless terminal detects the Beacon frame, it requests authentication from the BRAS or the AC controller through the AP device;
[0075] Step 403: the BRAS device or the AC...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com