A new safety group safety certificate generating method, communication method, and network system
A security credential and generation method technology, which is applied to security communication devices and key distribution, can solve the problems of heavy load and large amount of computation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 3 example
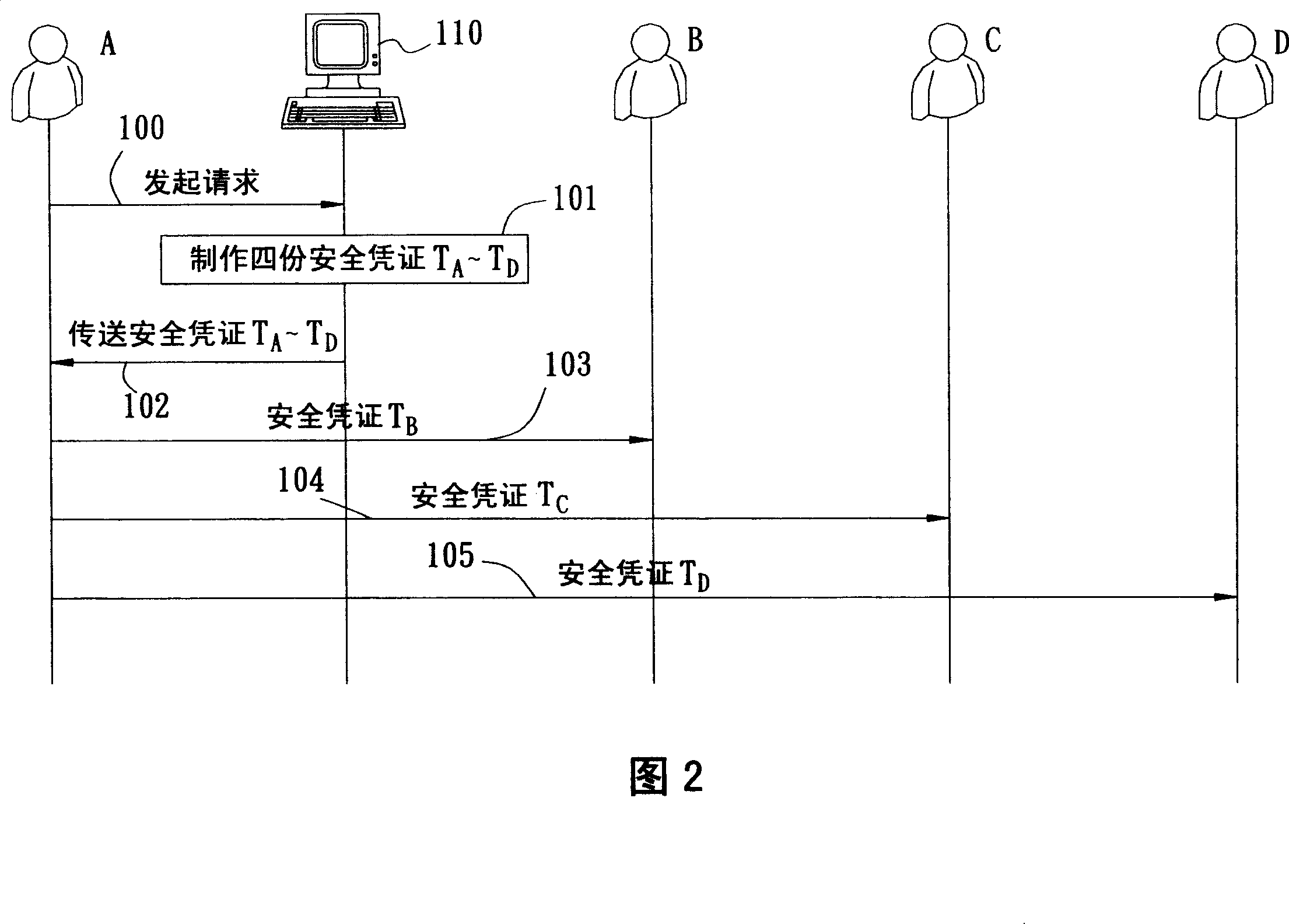
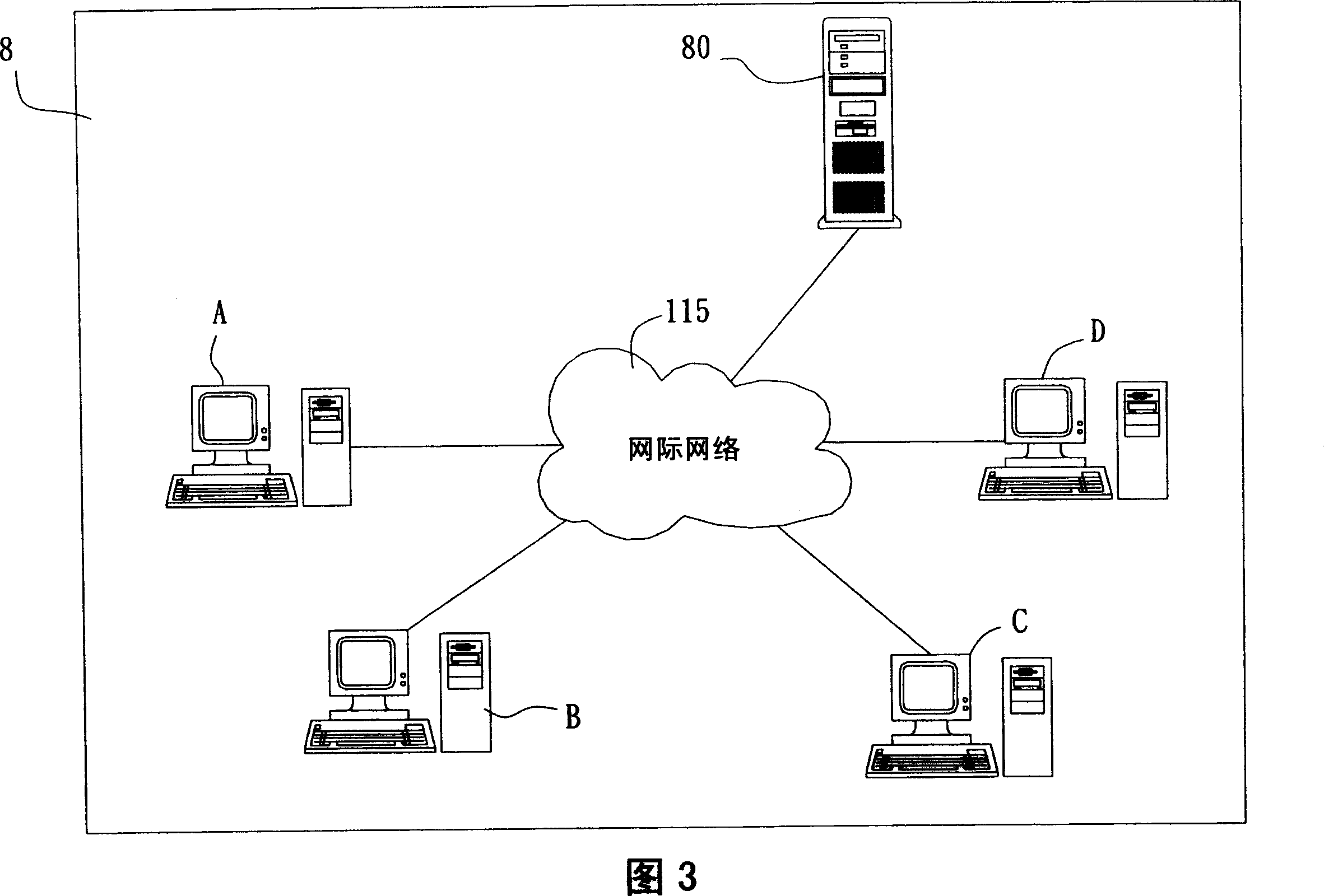
[0052] In the third preferred embodiment of the present invention, the architecture of the secure group network system 1 is the same as that of FIG. 3 , and the internal frame architecture of the communication device 30 included in the KDC 11 and each member is the same as that of the first preferred embodiment, Members A and B are originally included in one security group, members C and D are included in another security group, and members A, B, C, and D are included in one security group as a whole. The situation described in this embodiment lies in the process steps performed when a member who is not the group initiator (member B is taken as an example in this embodiment) wants to leave the original security group.
[0053] Referring to Fig. 9, in this preferred embodiment, members A, B, C and D have become a security group at this moment, when member B wants to leave, at first member B can send out request (LeaveRequest) to member A earlier (Step 601 ), when member A recei...
no. 4 example
[0058] In the fourth preferred embodiment of the present invention, the architecture of the security group network system 1 is the same as that of FIG. A and member B are originally included in one security group, members C and D are included in another security group, and members A, B, C, and D are included in a security group as a whole. The situation described in this embodiment is the group change process steps performed when a group initiator (member A is taken as an example in this embodiment) wants to leave the original security group.
[0059] Referring to Figure 10, when member A wants to leave the original security group, it will first send a leave request (Leave Request) to KDC11 in step 701 to notify KDC11 that it will leave the original security group and designate a new group initiator . In addition to the command to request to generate a new security group key, the leave request also includes information specifying the initiator of the new group. As far as thi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com