Cryptographic key generation method and system based on identity
A key generation and key generator technology, applied in the direction of user identity/authority verification, etc., can solve the problems of key escrow, loss of identity authentication, etc., to prevent impersonation attacks, remove dependencies, and protect privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
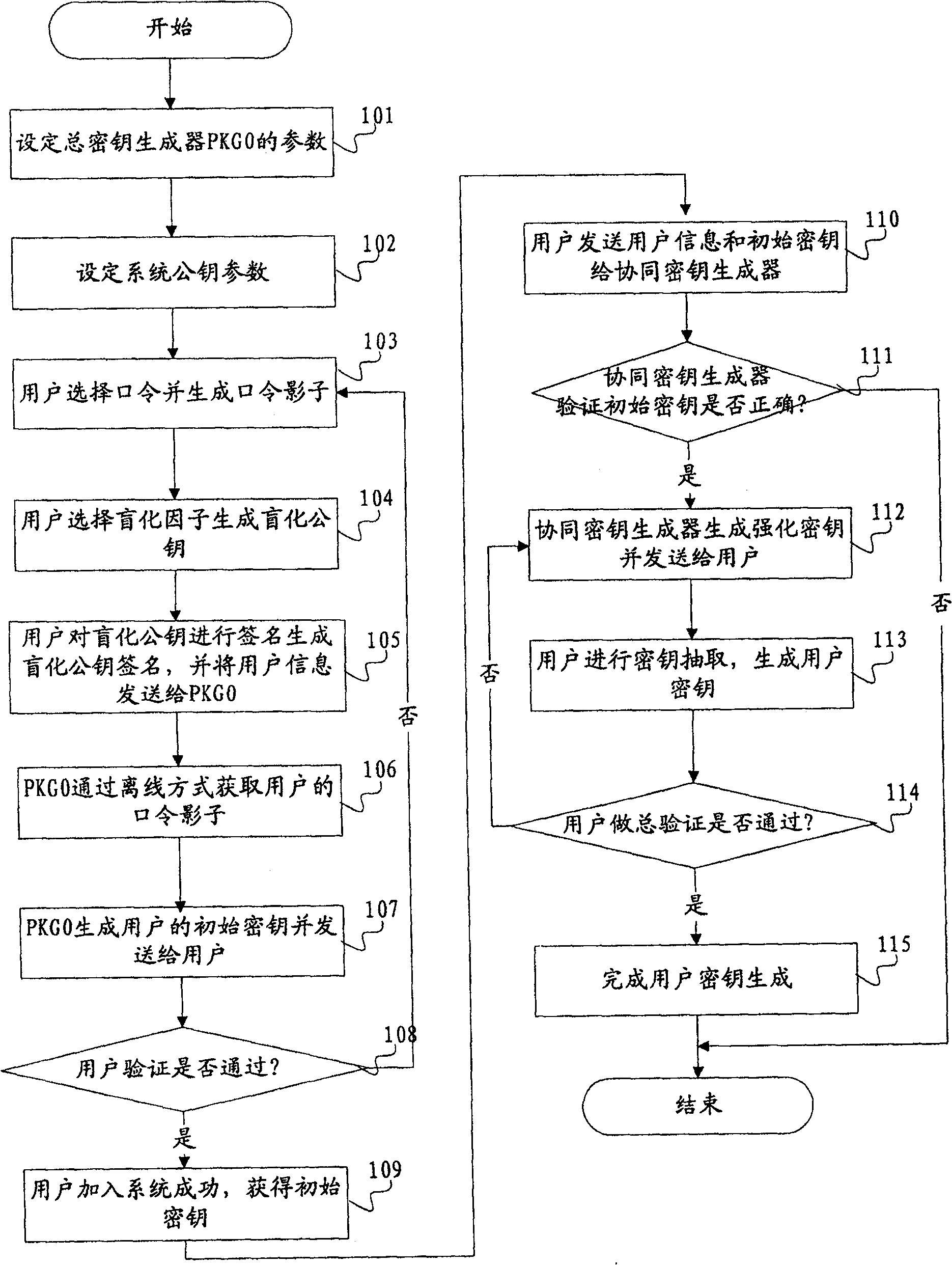
[0043] The present invention will be further described below with reference to the accompanying drawings and examples, but it is not intended to limit the present invention.
[0044] The present invention combines three technologies: blinding technology, multi-party authorization mechanism and password-based authentication mechanism, wherein the function of blinding is to remove the dependence on the secure channel, and the function of multi-party authorization mechanism is to overcome the impact of a separate key generator on the user. The role of private key escrow based on password authentication mechanism is to prevent attackers from impersonating users or a certain key generator.
[0045] The scheme of the present invention is specifically as follows:
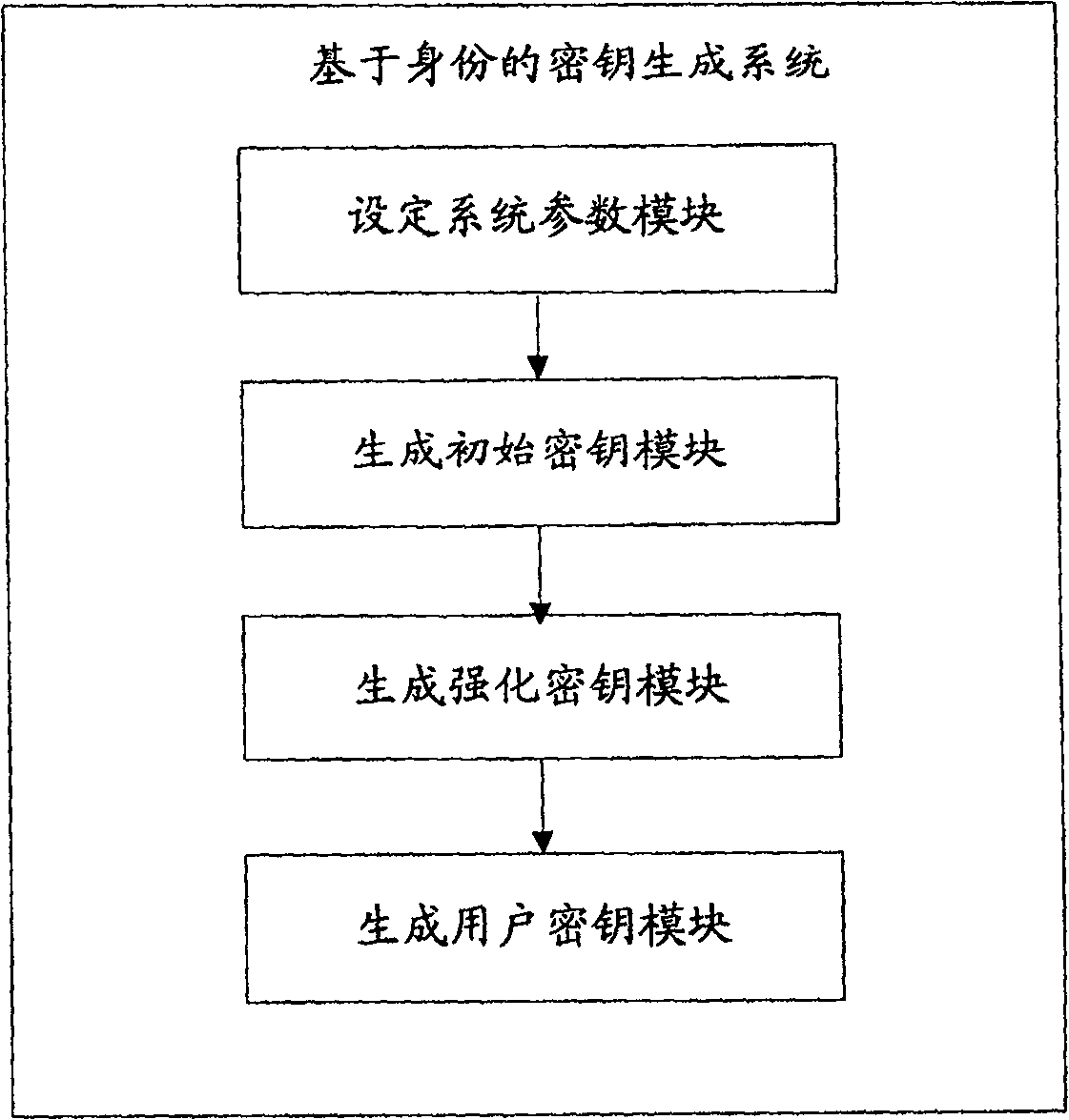
[0046] see figure 1, the present invention provides a method for generating an identity-based key, the method steps are as follows:
[0047] Step A: Set system parameters; the specific implementation steps are as follows...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com