Cabinet security monitoring method and device in modern logistics
A technology of security monitoring and modern logistics, applied in the direction of computer security devices, packaging, transportation and packaging, etc., can solve problems such as high cost of use, cumbersome operations for customers, and potential safety hazards, and achieve low cost of use, ensure information security, reduce The effect of chip count
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0041] Embodiment: A kind of anti-theft security monitoring method and device for freight containers in modern logistics
[0042] 1. Anti-theft security monitoring method
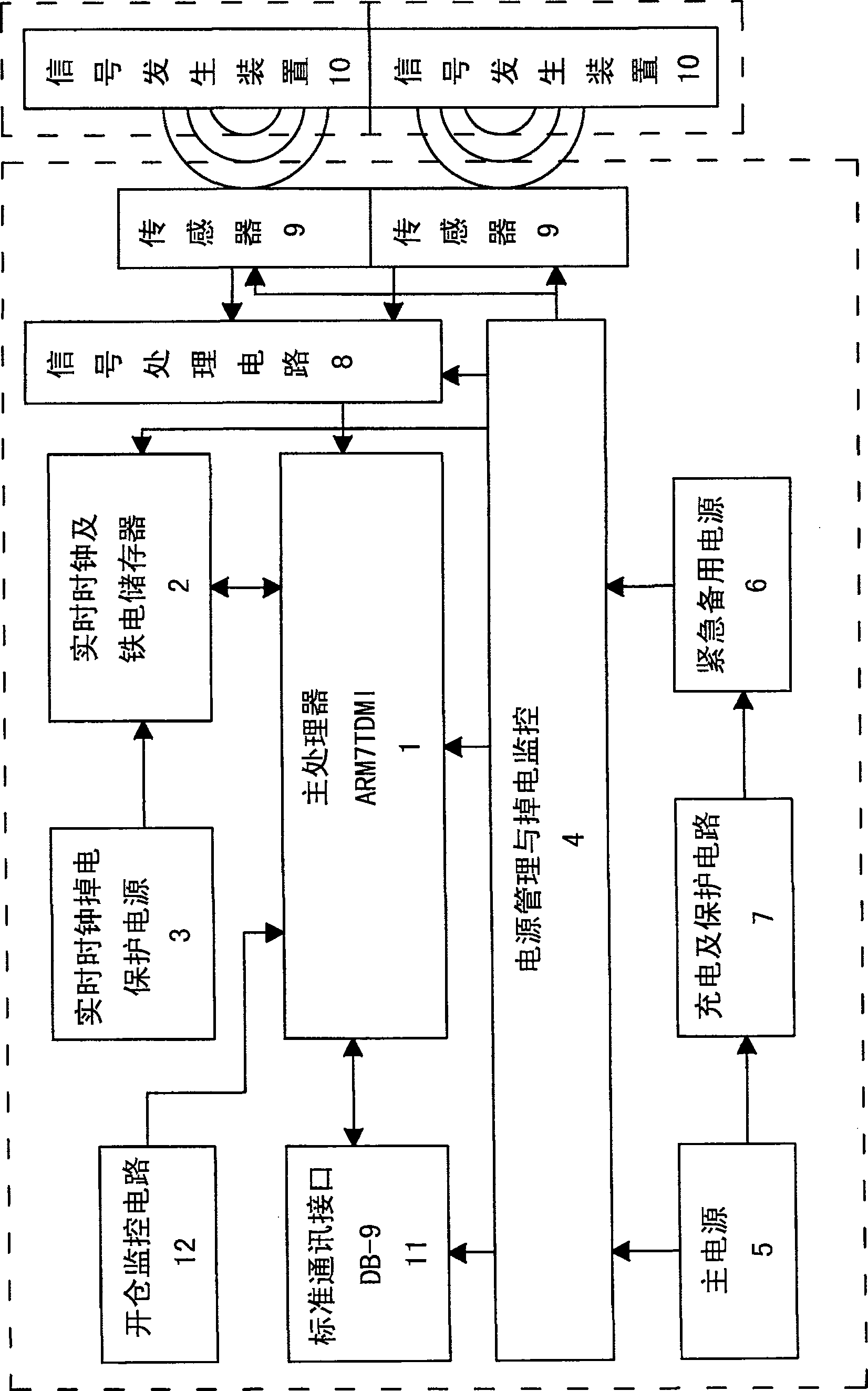
[0043] 1. Set up a black box on each container to automatically record the opening and closing information of the container during the circulation process and the opening information of the black box.
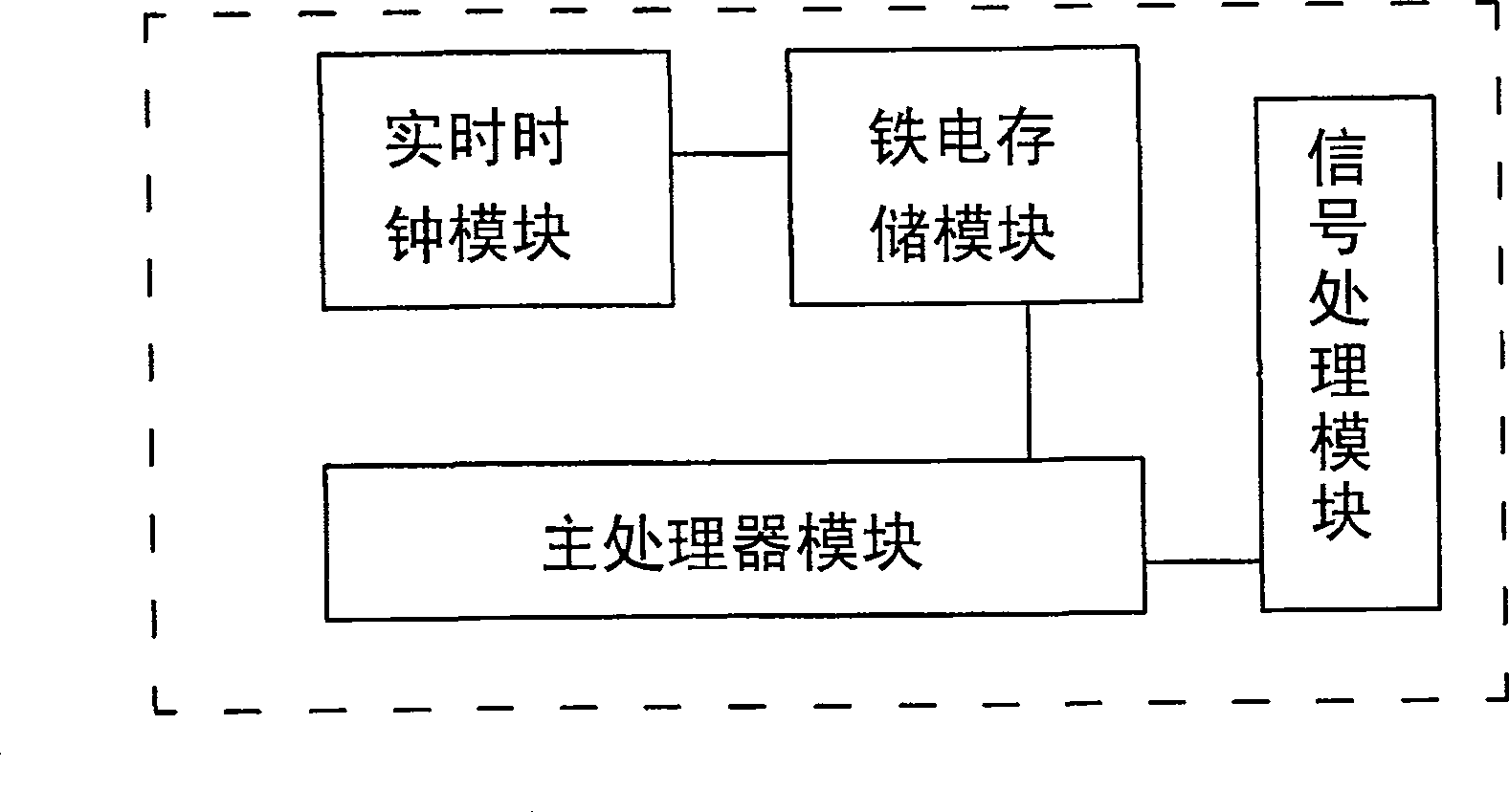
[0044] 2. The black box is composed of two parts: a signal generating device installed on the left and right doors of the container, and a host installed in the middle of the door frame of the container. Wherein, the host includes a sensor, a signal processing circuit, a main processor, a real-time clock circuit, a memory, a power supply circuit, a standard communication interface and a black box opening monitoring circuit. When the door is opened or closed each time, the sensor receives the induction signal from the signal generating device, and sends it to the main processor after being processed by the s...
Embodiment approach
[0089] Implementation method: For the encryption end, select the encrypted key and encryption algorithm through a certain algorithm mechanism. The decryption terminal selects the corresponding decryption algorithm and key according to the encryption-related information carried in the data to decrypt the data.
[0090] 17. Customer service communication encryption: For the communication between the client and the server, in order to provide more service applications, when the user's host computer communicates with the server of the service provider, the data obtained by the client is transmitted to the service provider. Session encryption means to ensure data security.
[0091] Implementation method: (1) Due to the use of public networks such as the Internet, encryption technology platforms such as the original link encryption technology of these networks can be used to ensure communication security. (2) Conversation is used for communication. The specific encryption algorithm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com