Methodology for identifying local/mobile client computing devices using a network based database containing records of hashed distinctive hardware, software, and user provided biometric makers for authorization of electronic transactions and right of entry to secure locations
a network based database and computing device technology, applied in the field of secure authorization of electronic transactions and/or a right of entry to secure locations, can solve the problem of no longer any opportunity to gain unauthorized access, and achieve the effect of enhancing the use of multi-factor authentication techniques and reducing the scale of fraudulent transactions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
embodiments
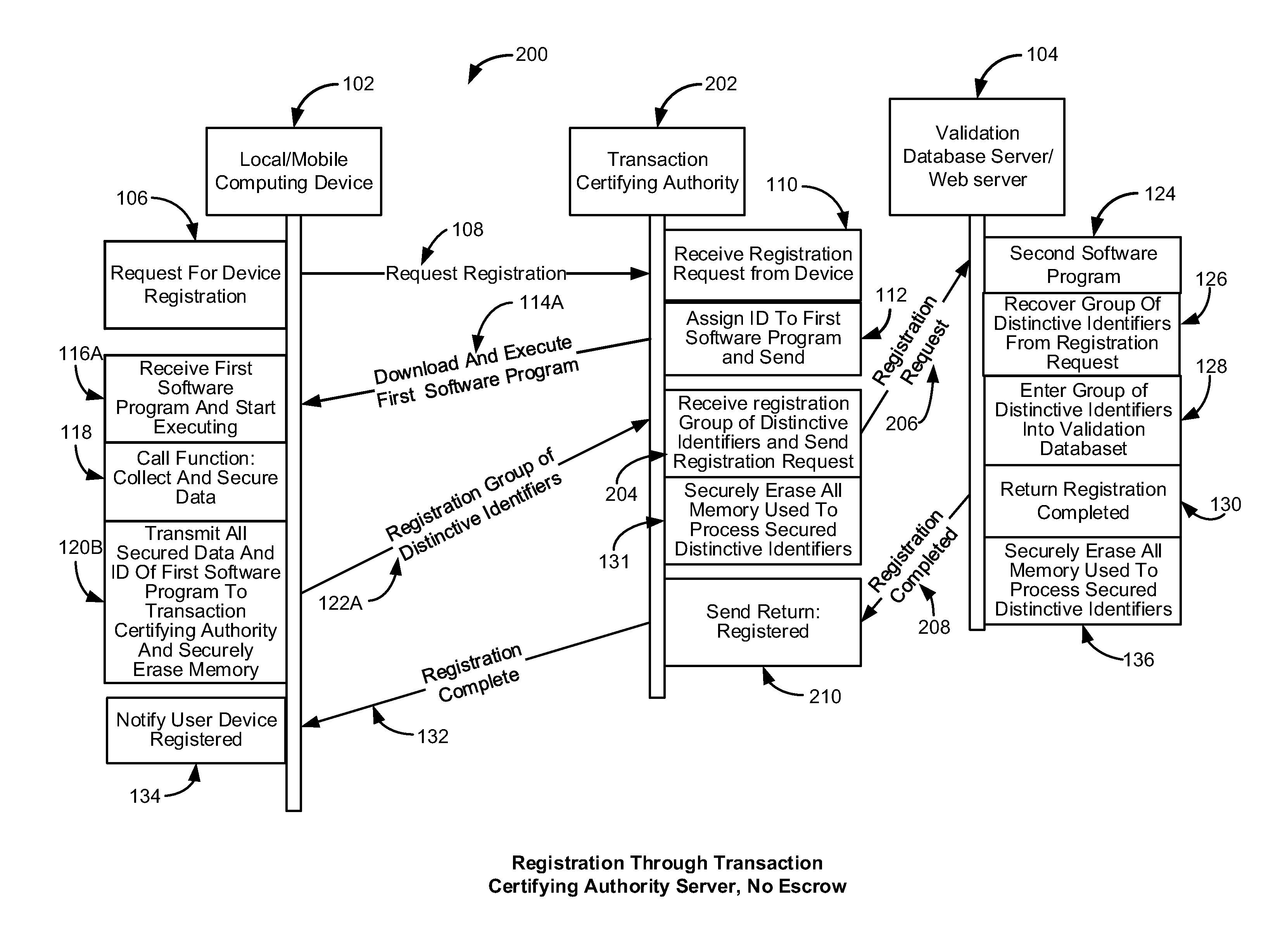
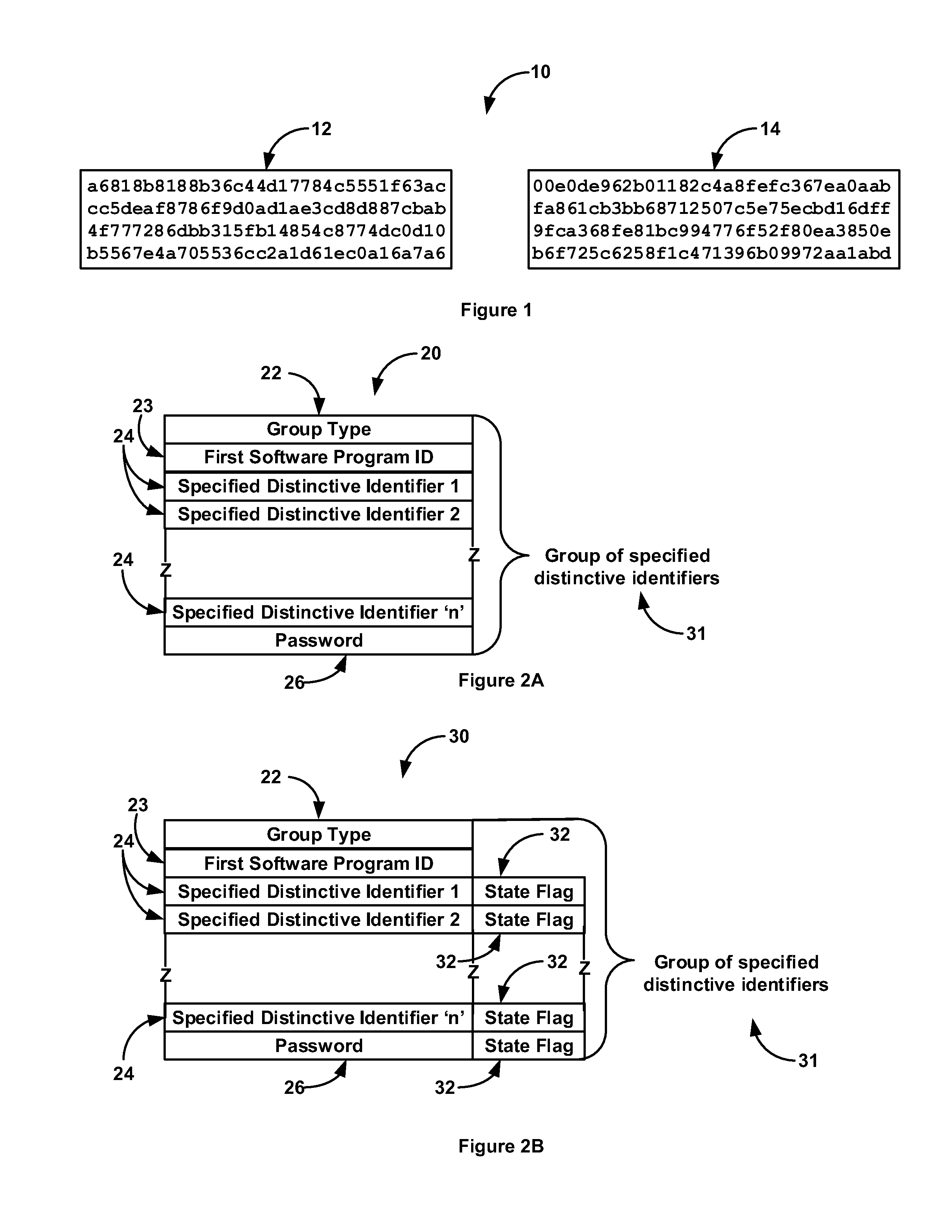
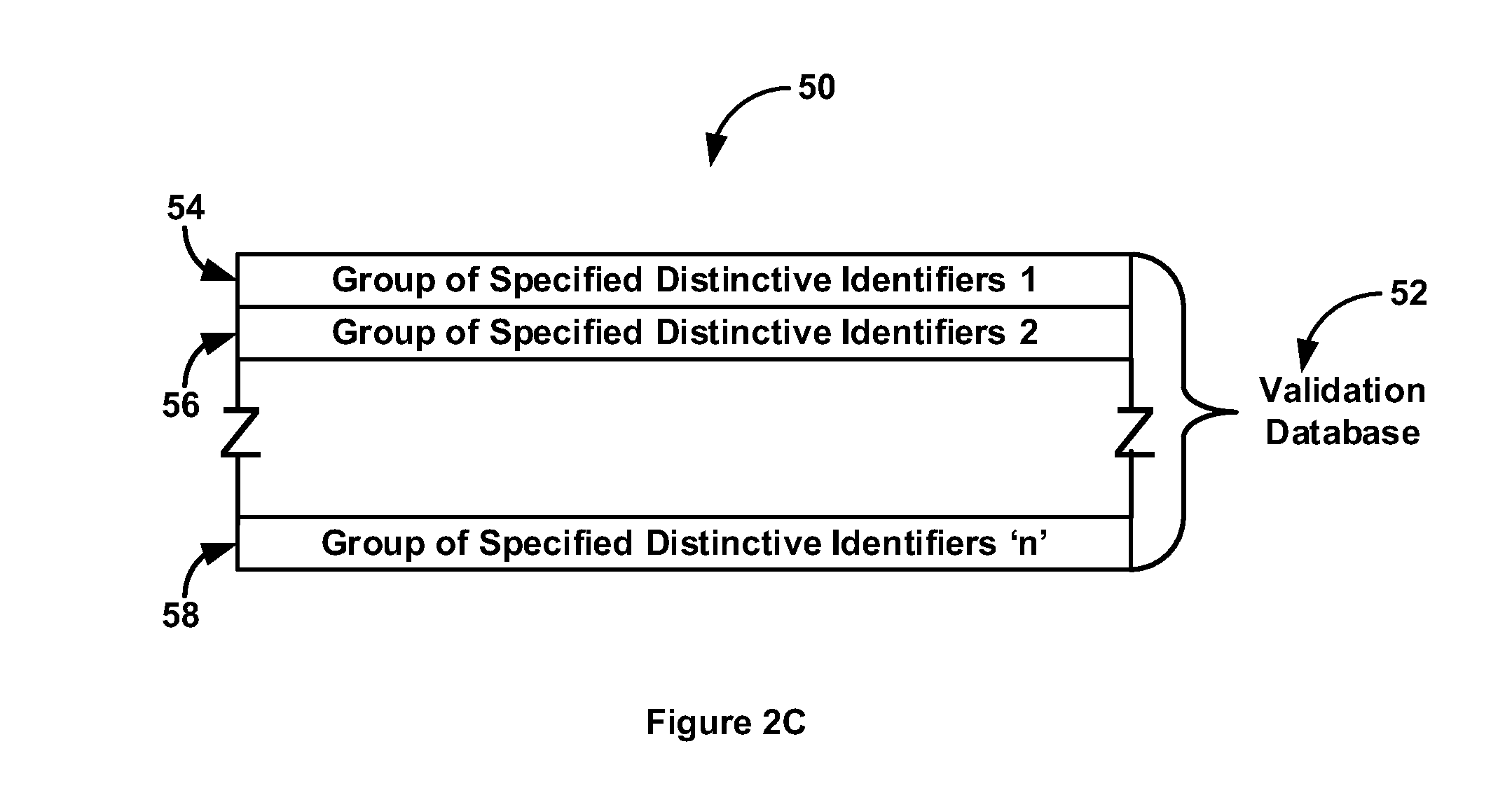
[0100]In a basic embodiment of this invention, the local / mobile computing device that generates a request for authorization or access becomes an authenticating factor in a multi-factor authentication process, and is considered in the process of authorizing a financial transaction or in approving access. This is accomplished by the rightful owner of the local / mobile computing device registering said device with a validation database created by this invention. By registering said local / mobile computing device with said validation database, the rightful owner is giving his consent and approval for the presence of this device to be considered in approving or denying the transaction.
[0101]Because said registered local / mobile computing device is now part of the authorization process, the rightful owner of the account has another layer of protection in insuring that compromised personal and / or financial data cannot alone be used in fraudulent transactions. This additional layer of security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com