USB security gateway
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
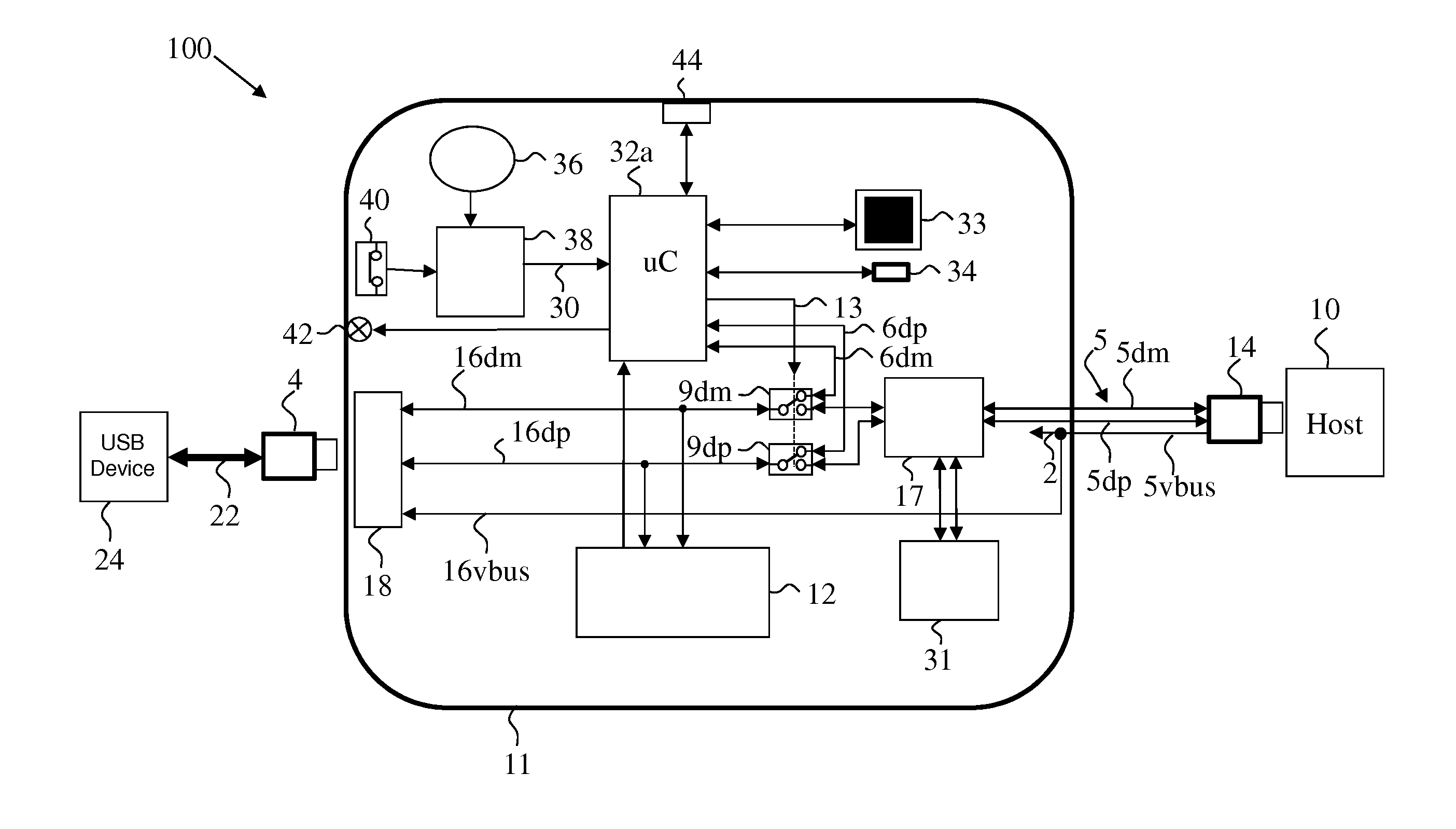
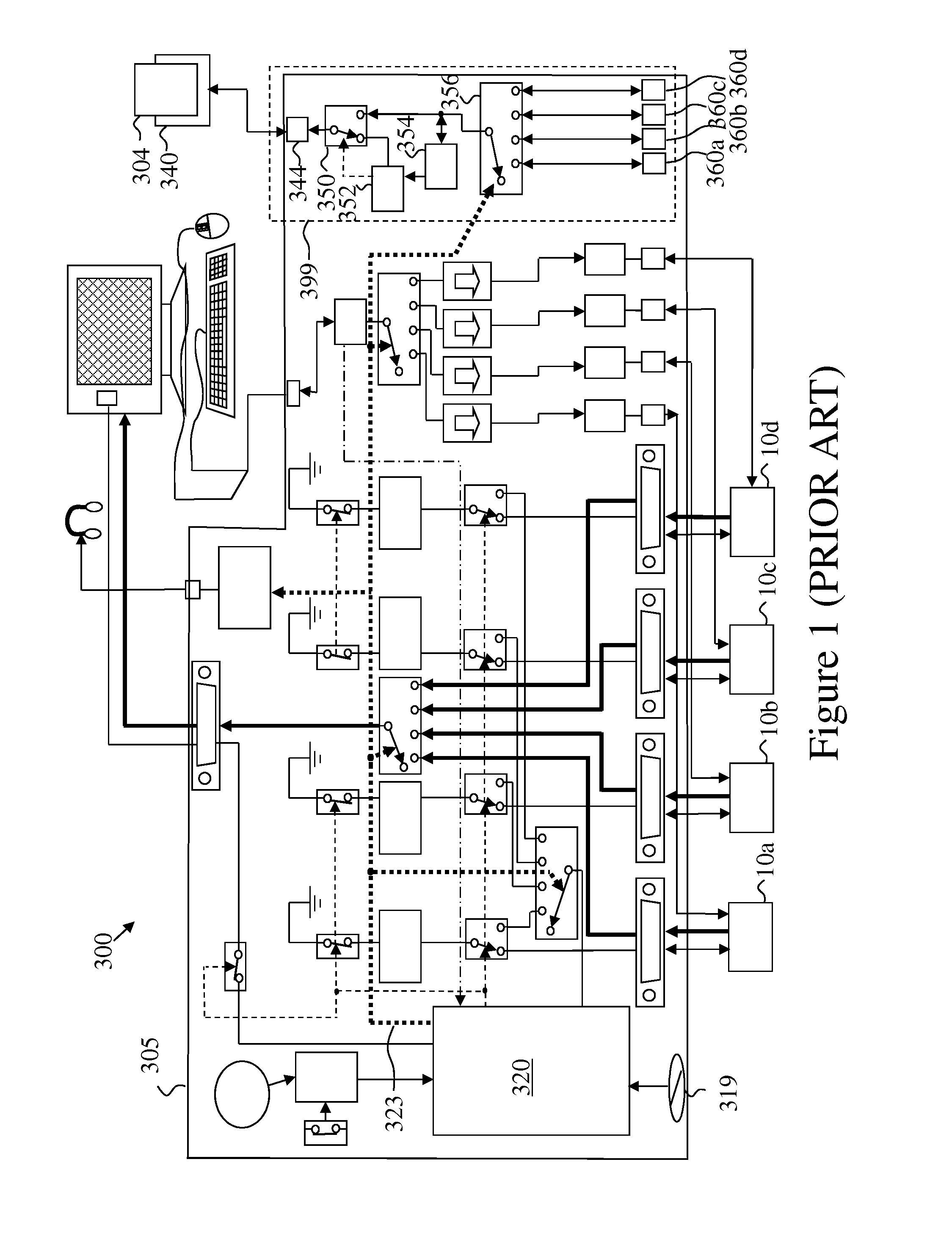
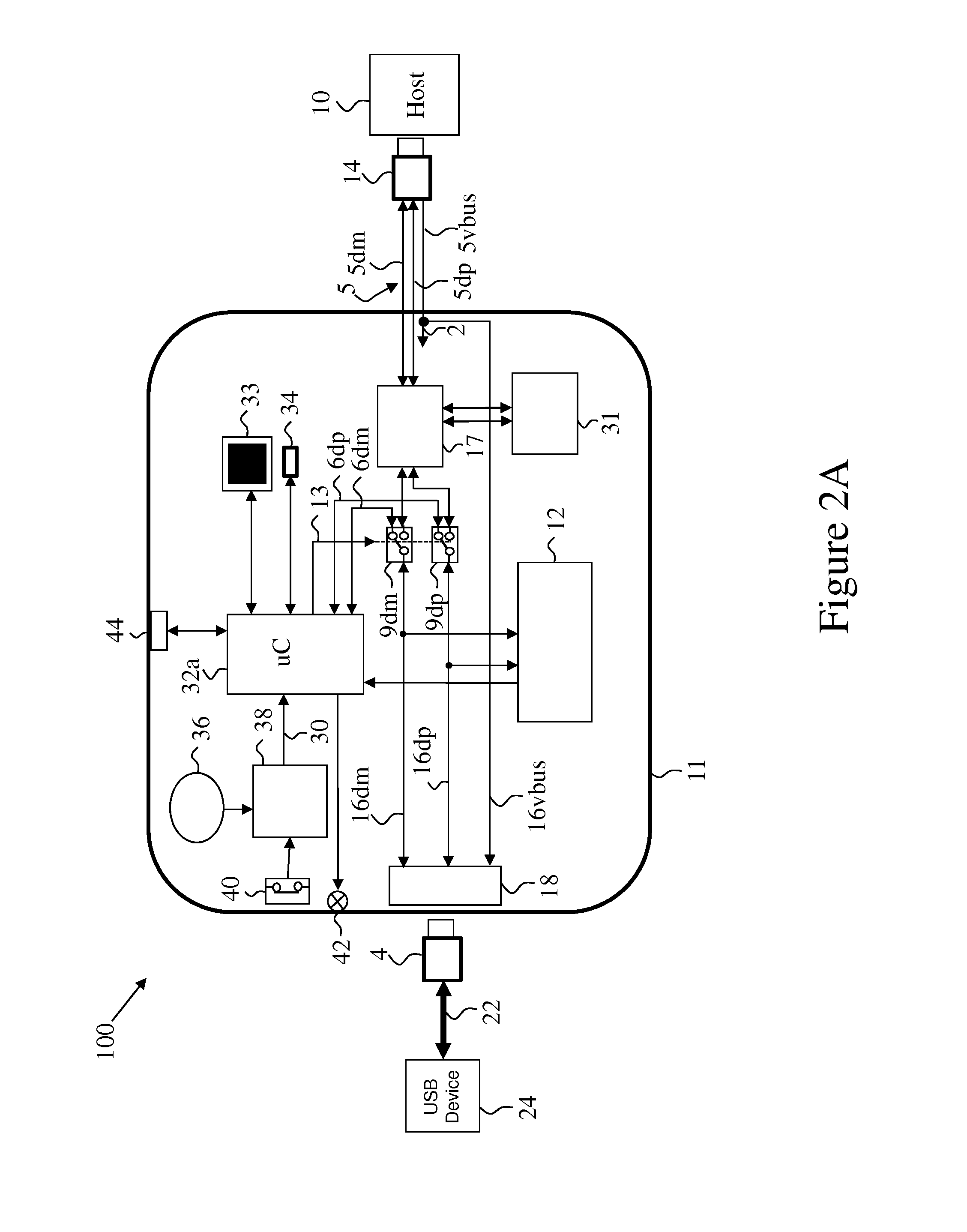
[0024]Some exemplary embodiments of the current invention provide a stand alone unit that performs at least some of the functionality of dedicated peripheral port switching subsystem. Some exemplary embodiments of the current invention provide improved functionality of the dedicated peripheral port switching subsystem.
[0025]Some exemplary embodiments of the current invention provide improved functionality of the dedicated peripheral port switching subsystem.
[0026]Some exemplary embodiments of the current invention provides the functionality of the dedicated peripheral port switching subsystem in a stand alone unit or in a unit integrated within a host computer.
[0027]Some exemplary embodiments of the current invention add functionality missing in the prior art devices, for example (and not limited to):
[0028]1. Fixed dedicated peripheral filter—for example a USB security filter designed to enable only Human Interface Devices (HID Class USB).
[0029]2. Field updateable profiles used to a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com