Computer data protecting method
a technology for protecting methods and computer data, applied in the field of security methods, can solve problems such as the illusion that unauthorized users have successfully hacked the inner data system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
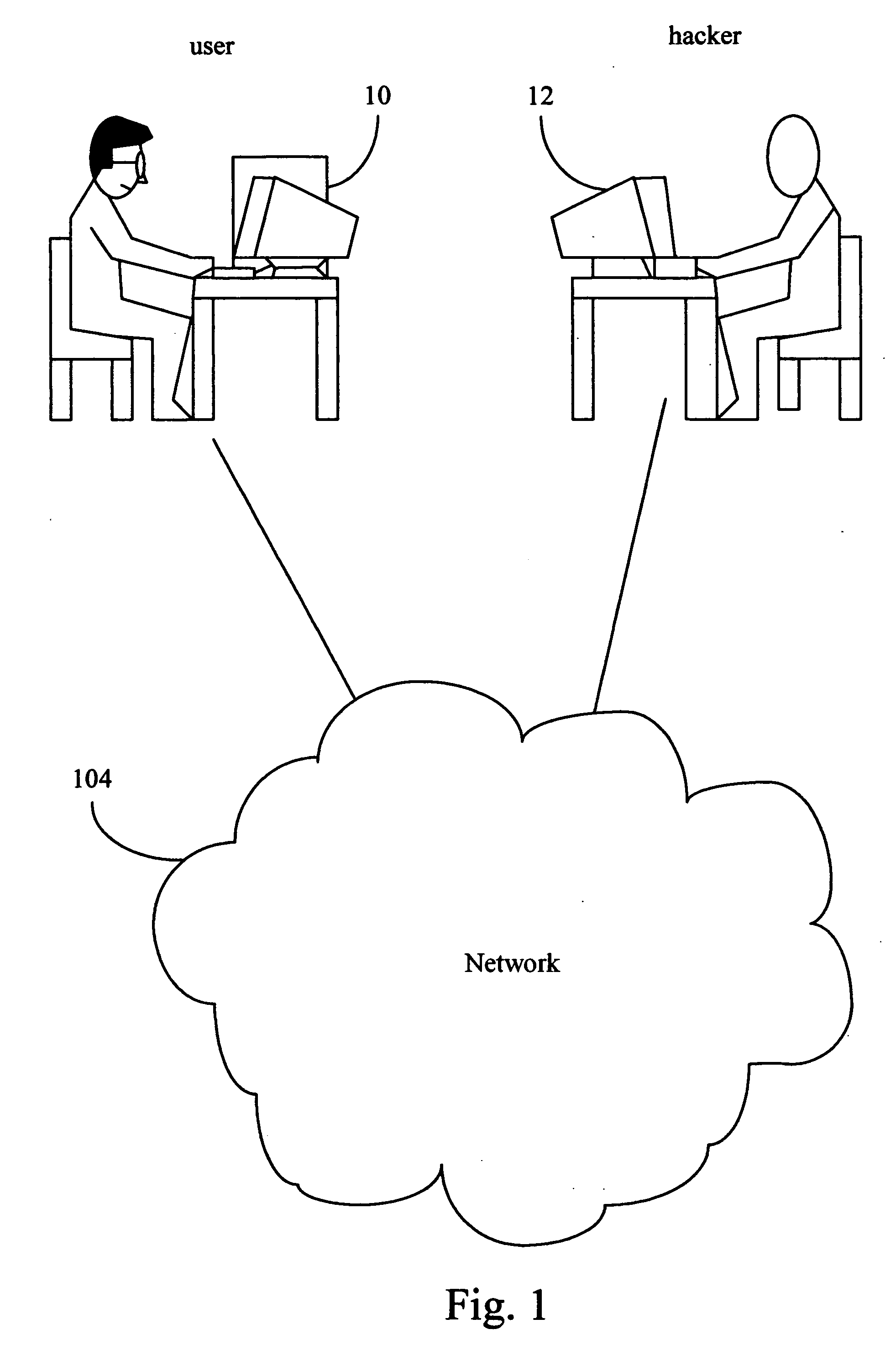
[0024]FIG. 1 illustrates a basic network structure. When a user 10 connected with the network 104, there is a probability of the data stored in the computer belonging to the user 10 being stolen or destroyed by a hacker 12 through the network 104. For example, the hacker 12 can browse the stored data through the network 104 if he can decode the password. Moreover, the hacker also can design and spread viruses on a network 104, and files carrying the viruses are downloaded while the user 10 through the network 104. When these files carrying the viruses are loaded back to the computer of the user 10, under certain situations, such as the infected files or macros are executed, the viruses further sneak into program modules of an operating system and waits to break out so as to damage the computer. Therefore, the present invention provides a system and method for preventing the attack from the hacker.
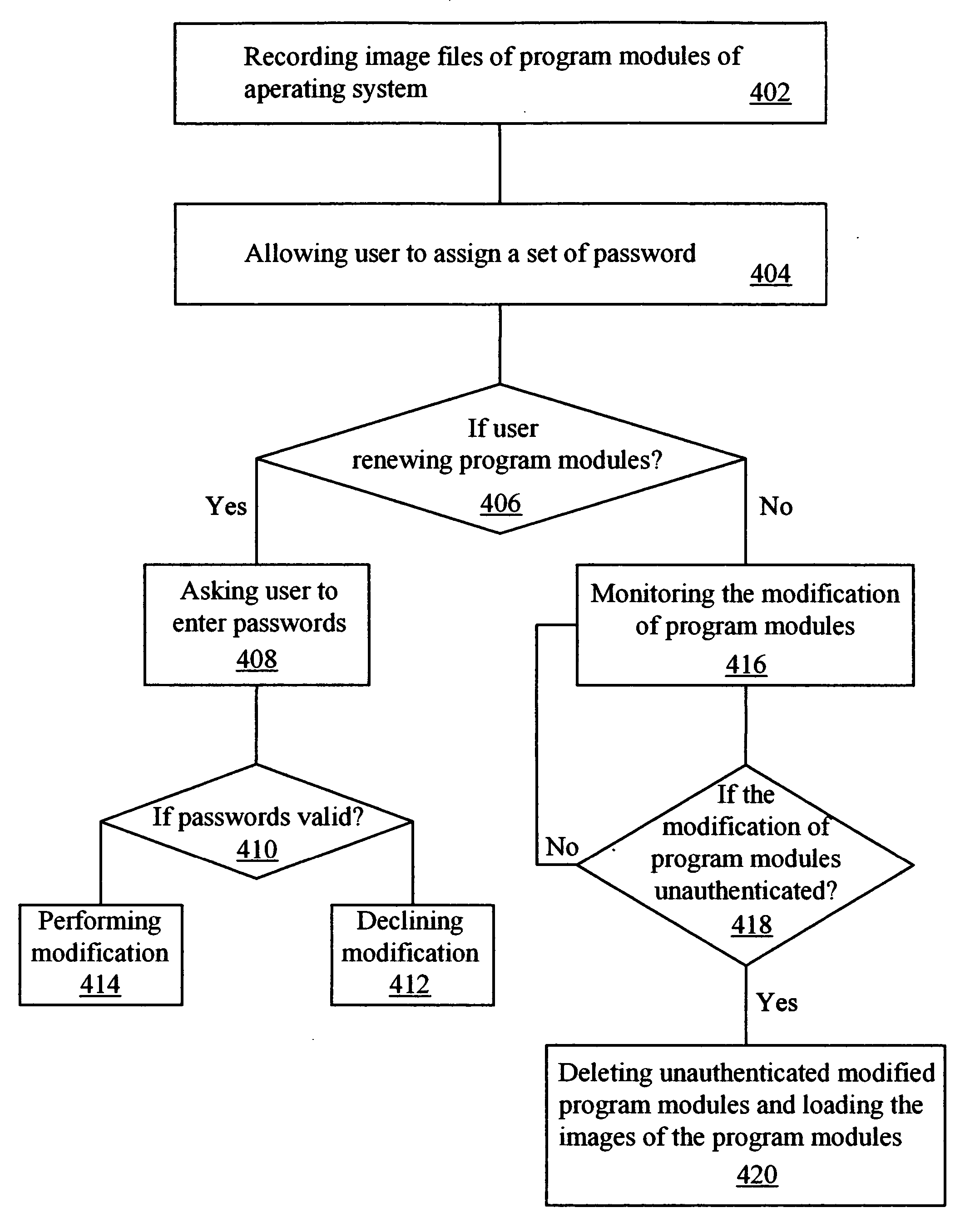
[0025] When a hacker spreads viruses on a network to attack the computer, the present ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com