A method to filter and verify open real IPv6 source address
A verification method and source address technology, applied in the Internet field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
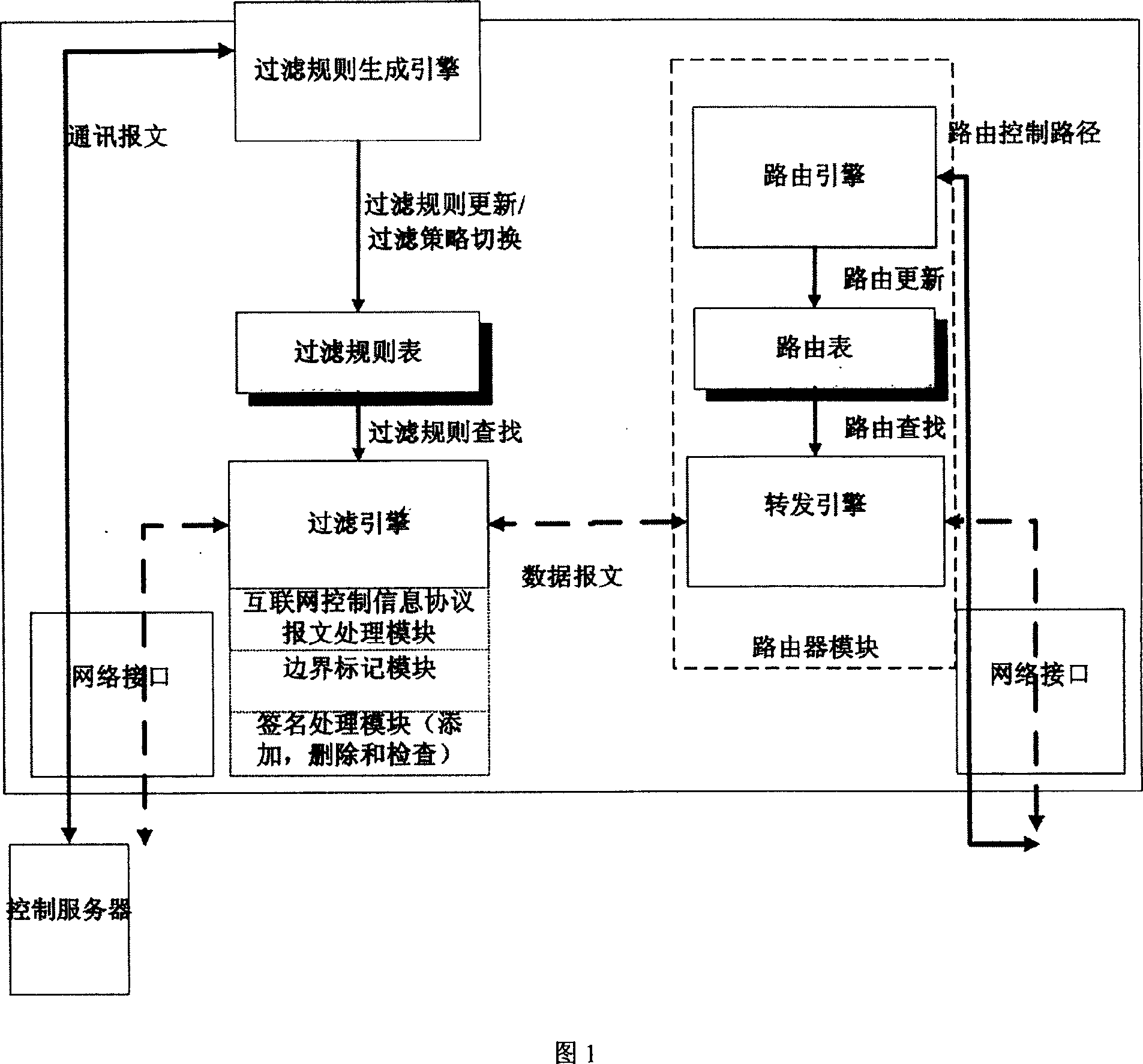
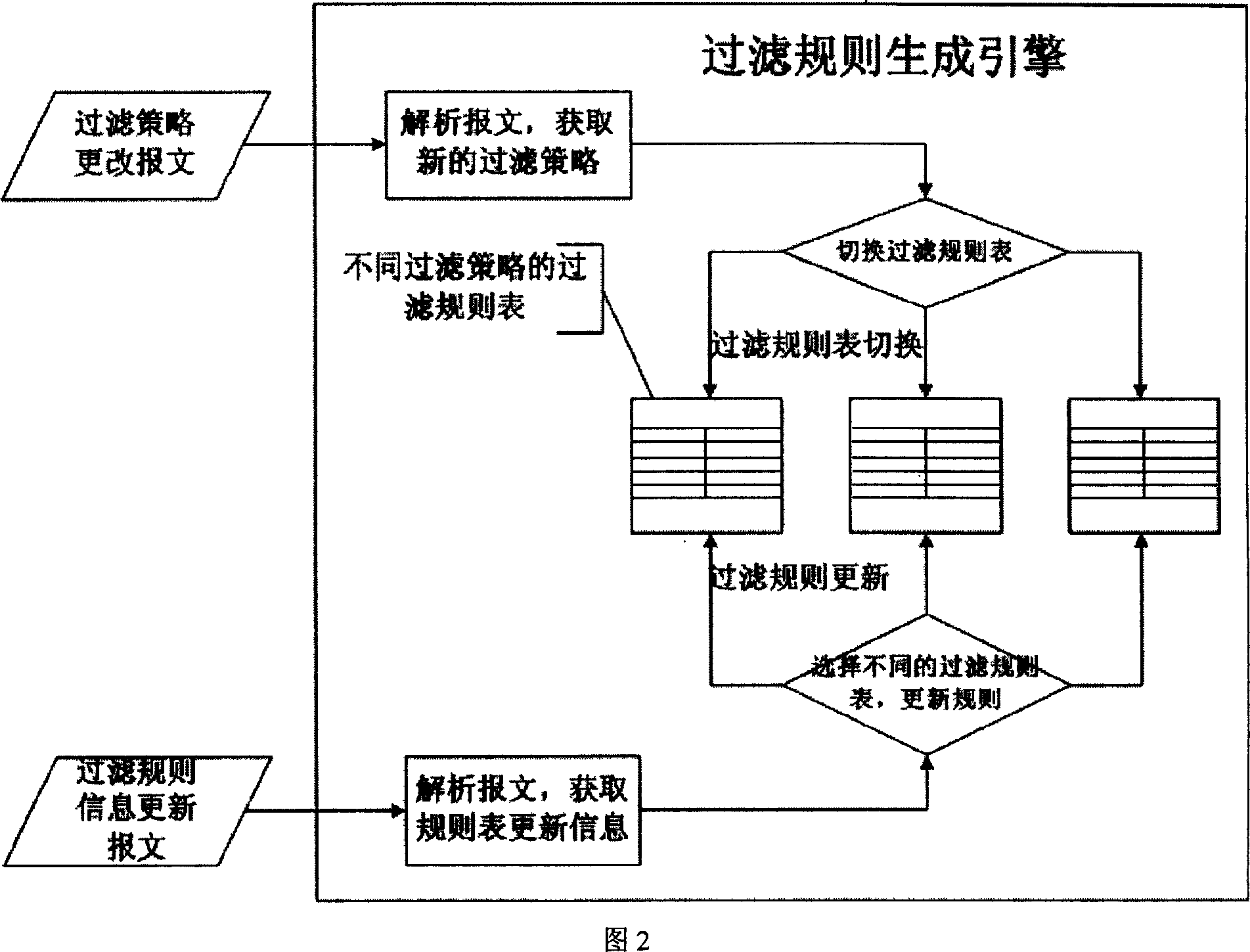
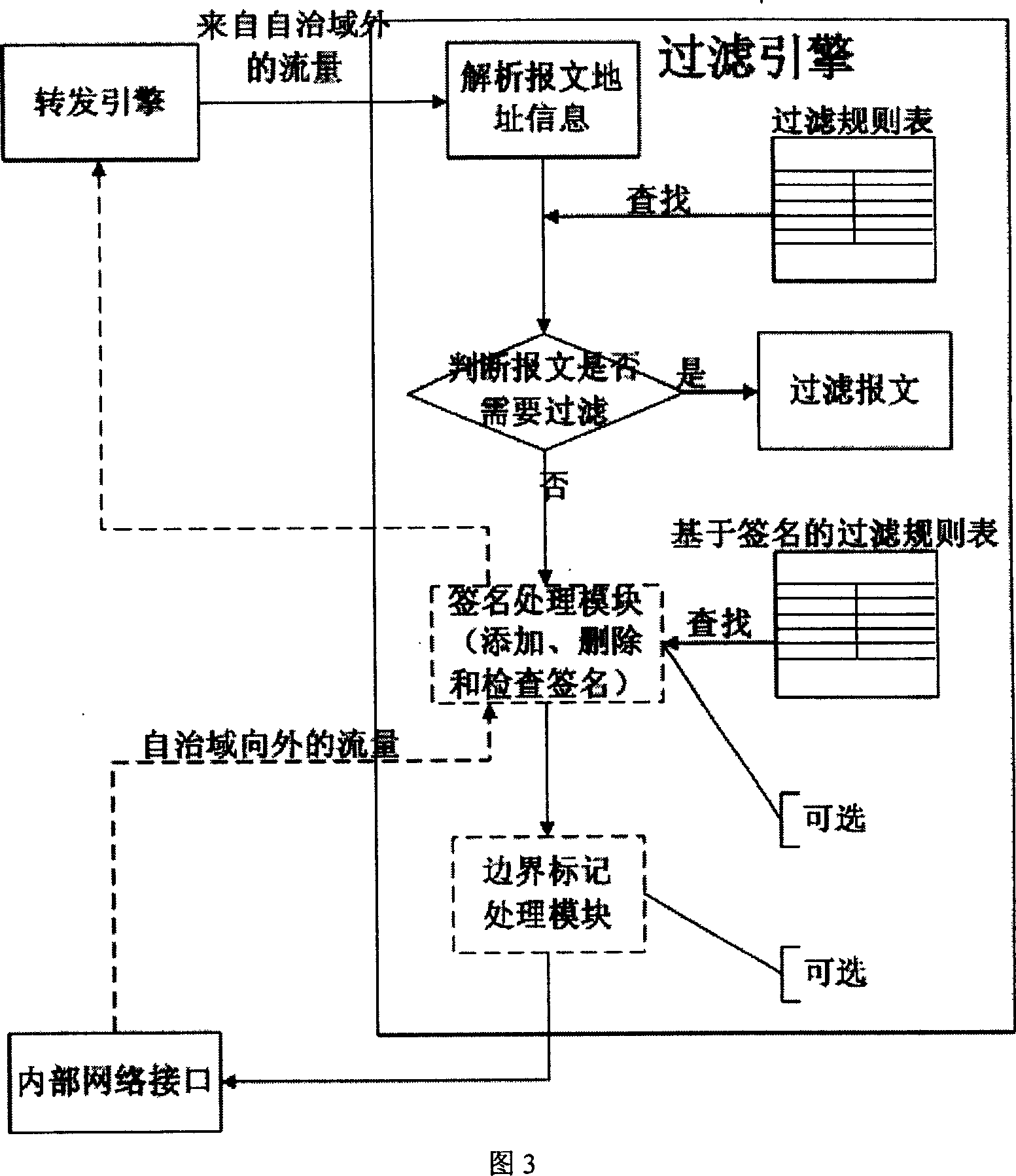
[0041] As shown in Figure 1, the present invention includes two functional engines: the filter rule generation engine dynamically generates a filter rule table according to the communication message and switches the filter rule; the filter engine judges whether to Filtering, and can selectively decide whether to add, delete, and check signatures on the message based on the content of the signature filtering rule table, or perform boundary marking operations on the message, or process Internet control information protocol messages . As shown in FIG. 1 , this method needs to cooperate with the routing engine and the forwarding engine of the traditional router. The filtering module also includes a signature processing module, a message marking module and an Internet Control Information Protocol message processing module.
[0042] The most important data table in the present invention is the filter rule table. The filtering rule table consists of three parts: prefix mapping tabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com